Contents:
Researchers at TrendMicro released yesterday a report documenting a new malvertising campaign. It uses the same malware they wrote about in 2020, the Cinobi banking trojan that used to steal banking credentials, but they also identified a rebranded version of it. This targets Japan and the way it works is by taking advantage of sideloading vulnerabilities.
A Little Bit of Background on Cinobi Banking Trojan
In 2020, a new banking trojan emerged. It was dubbed as Cinobi Banking Trojan, being part of a campaign named “Operation Overtrap”. The malicious group behind it was known as “Water Kappa”. Its methods were deployed in two ways: either via spam or making use of the Bottle exploit kit that contained CVE-2020-1380 and CVE-2021-26411 (2 Internet Explorer exploits). What was interesting was that only Internet Explorer users were targeted through these malvertising attacks. Now the TrendMicro researchers wrote a report on the new campaign using the Cinobi Banking Trojan and its other variants.
If the campaign showed no signs of activity for some time, the above-mentioned experts identified a new malvertising campaign that implies social engineering tactics, which, via a compromised application, delivers the Cinobi banking trojan. The targeted country is Japan and the way it works is by corrupting sideloading bugs. Researchers at TrendMicro are of opinion that the same hackers that engaged in the “Operation Overtrap” campaign are behind this new one.
The Recent Malvertising Campaign: What’s New Here
In the past hackers used to target Internet Explorer users, now they seem to exclude the latter and target other web browser users. The Cinobi banking trojan has not changed that much. What’s new here is that it upgraded its configuration. At the present moment, on the target list, one can found also Japanese websites whose topics are cryptocurrency exchange. Cryptocurrency accounts’ credentials are now what hackers want to obtain by deploying the banking trojan called Cinobi.
Besides, in the rebranded version of the malware, the archive the impacted users will download to deploy it contains now only 3 files (xjs.dll, format.cfg and “ros”) with 3 stages instead of 4 and just one C&C server instead of two command-and-control (C&C) servers.
How the Cinobi Banking Malware Works
The same report documented the specific steps the Cinobi banking trojan follows to distribute its malicious activity. According to the researchers’ statement:
- A user will receive an apparent commercial whose topic can be related to Japanese animated porn games, applications that are used for video streaming, or other apps with reward benefits.
- These are actually malvertisements controlled by the hackers.
- The users will click on the text “index.clientdownload.windows” which does nothing else than download a Zip archive.
- The user will receive instructions on how to open and execute what’s inside.
- After the archive is extracted, it shows a bunch of files.
- dll and cfg.config will be copied to directory %TEMP% by means of the format.cfg that contains the shellcode.
- These files will be renamed to a.dll and 1.txt and then an export function will be executed:
rundll32.exe “%TEMP%\a.dll”,a %TEMP%\1.txt
- How is the shellcode executed? a.dll will take the needed APIs and resolve them, then it will load 1.txt. With an XOR key, this will be decrypted and then the shellcode executed.
The researchers determined that the Cinobi Banking Trojan is deployed via 4 stages, the one described above representing basically the first stage. The steps mentioned above represent the general way Cinobi banking malware operates.
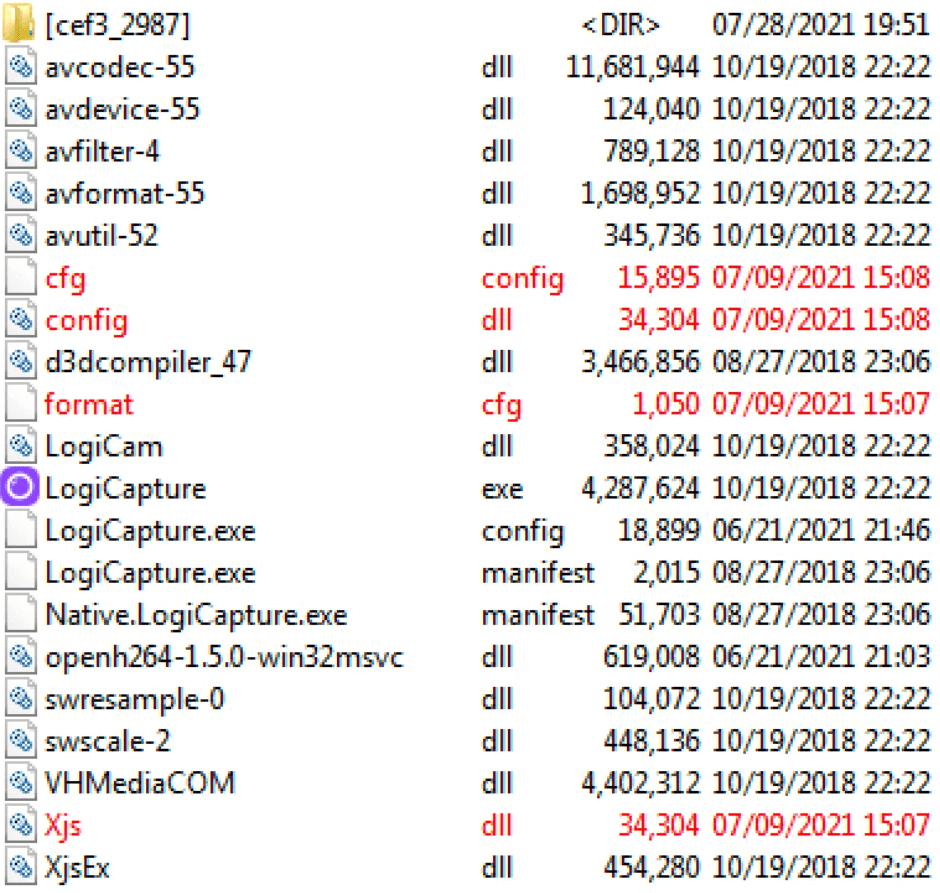
The Cinobi Banking Trojan Refactored Version
Now, the researchers, as mentioned earlier in the news, have also discovered a refactored version of this trojan that involves only 3 files with 3 stages and one C&C and what’s also new is that in the first stage format.cfg is decrypted and loaded by Xjs.dll. What does this variant now is to use the “ros” file and extract documents from there and the danger here is if a user uses a compromised machined and clicks on a link found in the configuration file that was extracted from the “ros” file, a malware feature is activated: the form-grabbing capability. The user will fill out a form and when it returns to the server, the malware will be installed and the credentials stolen.
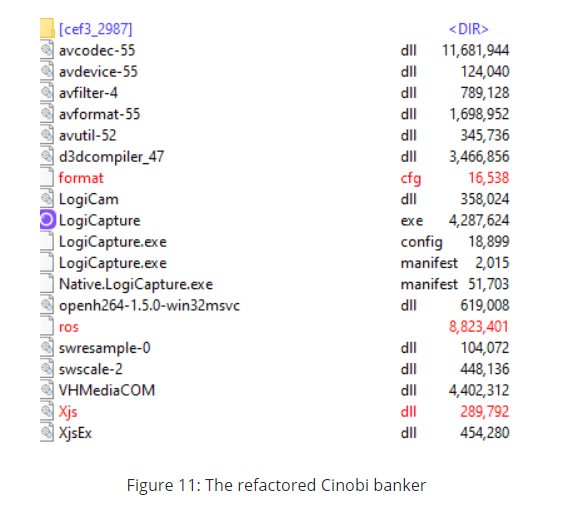
According to the report, what is also interesting to note is that the malicious website can be accessed only via Japanese IP addresses and that malicious threat actors behind the malvertising campaign are trying to steal cryptocurrency. The only mitigation measure for now remains the vigilance of the users.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










