
Unpatched Microsoft Exchange servers are being targeted by the Prometei botnet and added to its operators' army of Monero (XMR) cryptocurrency mining bots.
This modular malware can infect both Windows and Linux systems, and it was first spotted last year while using the EternalBlue exploit to spread across compromised networks and enslave vulnerable Windows computers.
Around since at least 2016
Cybereason's Nocturnus team recently discovered that the botnet has likely been active for almost half a decade, according to Prometei artifacts submitted to VirusTotal in May 2016.
Based on new malware samples recently found by Cybereason during recent incident responses, the botnet has also been updated to exploit Exchange Server vulnerabilities patched by Microsoft in March.
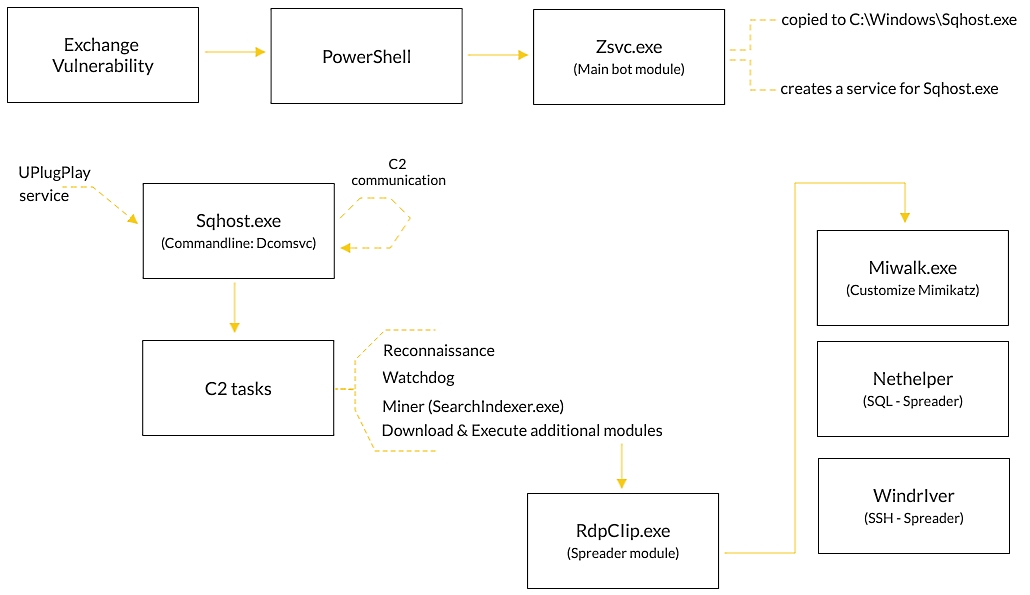
The main focus of Prometei's attacks on Exchange servers is to deploy the cryptomining payload, start earning money for its operators, and spread to other devices on the network using EternalBlue and BlueKeep exploits, harvested credentials, and SSH or SQL spreader modules.
"When the attackers take control of infected machines, they are not only capable of mining bitcoin by stealing processing power, but can also exfiltrate sensitive information as well," said Assaf Dahan, Cybereason senior director and head of threat research.
"If they desire to do so, the attackers could also infect the compromised endpoints with other malware and collaborate with ransomware gangs to sell access to the endpoints."
Cryptojacking botnet with backdoor features
However, the malware has been upgraded with backdoor capabilities with support for an extensive array of commands.
These include downloading and executing files, searching for files on infected systems, and executing programs or commands on behalf of the attackers.
"The latest versions of Prometei now provide the attackers with a sophisticated and stealthy backdoor that supports a wide range of tasks that make mining Monero coins the least of the victims' concerns," Cybereason Nocturnus Team said.
While the threat actor(s) behind this botnet is unknown, there is evidence that they speak Russian, including the name of the botnet, Prometei (Russian for Prometheus), and the Russian code and product name used in older versions.
Cybereason's research also points to the botnet operators being financially motivated and likely not sponsored by a nation-state.
"As observed in the recent Prometei attacks, the threat actors rode the wave of the recently discovered Microsoft Exchange vulnerabilities and exploited them in order to penetrate targeted networks," the Cybereason Nocturnus Team added.
"This threat poses a great risk for organizations, since the attackers have absolute control over the infected machines, and if they wish so, they can steal information, infect the endpoints with other malware or even collaborate with ransomware gangs by selling access to the infected endpoints."
Over 90% of vulnerable Exchange servers now patched
The CVE-2021-27065 and CVE-2021-26858 flaws exploited by Prometei were also abused by several Chinese-backed hacking groups and other hacking groups to deploy web shells, ransomware [1, 2], and cryptomining malware.
According to stats shared by Microsoft last month, roughly 92% of all Internet-connected on-premises Exchange servers affected by these vulnerabilities are now patched and safe from attacks.
Redmond also released a one-click Exchange On-premises Mitigation Tool (EOMT) tool to help small business owners quickly mitigate the security bugs even without the help of a dedicated security team.
Adding to that, Microsoft Defender Antivirus automatically protects unpatched Exchange servers from ongoing attacks by automatically mitigating the vulnerabilities.


Comments
AlfaX - 3 years ago
"When the attackers take control of infected machines, they are not only capable of mining bitcoin by stealing processing power, but can also exfiltrate sensitive information as well," said Assaf Dahan, Cybereason senior director and head of threat research.
The Senior Director and Head of Threat Research doesn't know you can't mine Bitcoin on cpu/gpu anymore? The SD&HTR should know better.