Critical OWASP Top 10 API Security Threats
It’s no secret that APIs are under attack. Companies are struggling to keep their APIs safe and secure from accidental breaches to malicious hacks. The problem will only worsen as APIs become more complex and more companies rely on them for critical business functions. The security risks increase exponentially.
So, what can businesses do to protect their APIs?
The first step is to understand the various types of threats that are out there and how they can harm your API. Next, you need to apply proper API security measures to mitigate those risks.
OWASP API Top 10 Threats
When it comes to application security, the Open Web Application Security Project (OWASP) is one of the most reliable sources of information. Their Top 10 API security threats document outlines the most common attacks that occur against web APIs and provides tips on protecting your API from these threats. It’s updated every few years as new threats emerge, and old threats become more prevalent. The current version (2019) of the Top 10 is as follows:
1. Broken Object-Level Authorization
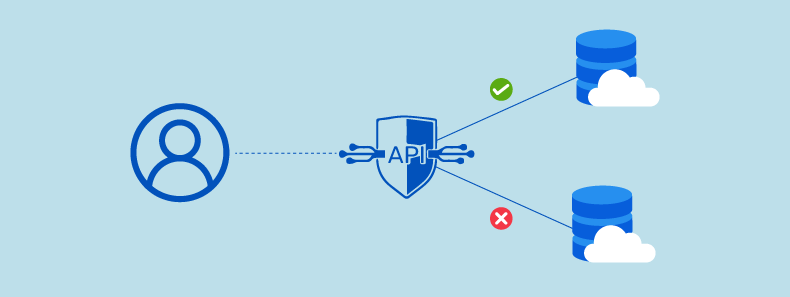
One common type of API vulnerability is the Broken Object Level Authorization (BOLA) vulnerability. This occurs when the authorization controls around objects (such as data files or database records) are broken, allowing unauthorized users access to those objects.
This can be a severe API security threat because it allows attackers to access sensitive data and information that they should not have access to. It can enable them to take control of the system, potentially causing damage or compromising its security. In addition, it can also cause a loss of revenue for the company if confidential information is released to the public.
Solutions:
- It is therefore important for companies to have a system in place that detects and corrects any broken object-level authorization as soon as possible. By doing so, they can minimize the damage that this issue can cause.
- Implement proper authorization mechanism, including object-level authorization checks.
- Use an API gateway.
- Use random non-guessable IDs.
2. Broken User Authentication
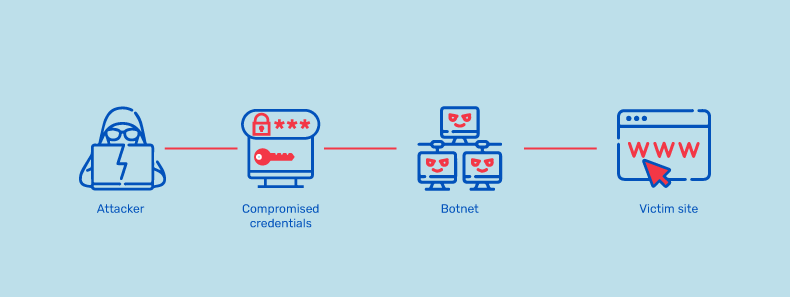
API authentication is a critical process that verifies if the person or application attempting to access an API is authorized. A broken API authentication vulnerability occurs when the authentication mechanisms are misconfigured. This means that anyone who knows the correct username and password can access the API, regardless of whether they are authorized to do so or not. This can lead to data theft, unauthorized account access, and other security breaches.
There are many ways that an attacker can exploit broken user authentication, including using stolen credentials, session hijacking, and social engineering.
Once attackers have gained access to systems and data, they can exploit them further or sell them on the black market. They can also use them to launch other attacks, such as denial-of-service (DoS) attacks or ransomware attacks.
Solutions:
- Enforce multi-layer authentication to verify the user’s identity.
- Limit the number of login attempts.
- Protect user credentials.
- Use strong API keys, just like passwords.
3. Excessive Data Exposure
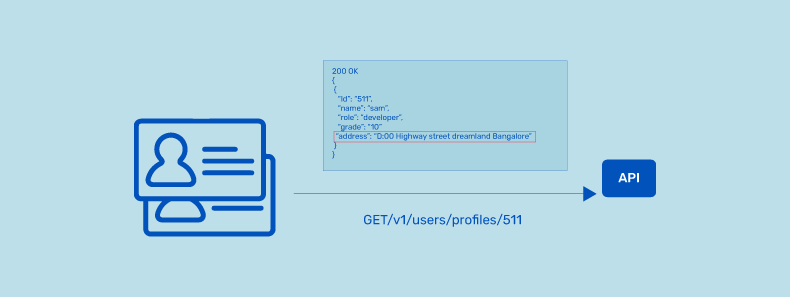
While data exposure can refer to several different issues, in the context of application programming interfaces (APIs), it is when an application reveals more information than necessary to the user via an API response.
This can include sensitive data like social security numbers, credit card numbers, and login credentials. When this information is released, malicious actors can use it to exploit the user in some way, such as identity theft or financial fraud.
API developers often make the mistake of exposing all object properties without considering their individual sensitivity and rely on the client-side code to perform the data filtering.
Solutions:
- Starting a positive security approach early in the API design process can limit the API security threats, including excessive and sensitive data exposure.
- Avoid depending on clients for performing data filtering.
- Minimize the return response from the back-end system to make it harder for hackers to discover the vulnerabilities.
4. Lack of Resources & Rate Limiting
When an API doesn’t limit the number of requests that can be made in a given period of time, it can quickly lead to congestion and affect the overall performance of the API. It can also lead to a denial of service (DoS) attack when a site is overwhelmed with traffic to the point where it becomes inaccessible to legitimate users.
Even worse, it can cause the API to fail altogether, which would be a massive inconvenience for both developers and users. This is a problem because it can severely impact the business or service using the API. If their requests are constantly being blocked, they won’t serve their customers or users as they intended.
Solutions:
The API security solutions should monitor API call rates, the number of resources requested, and their response. This helps ensure that the system is not overloaded with too many requests and that the correct response is sent back to the requester. Additionally, it can help identify any malicious actors trying to overload the system or gain access to unauthorized data.
5. Broken Function Level Authorization
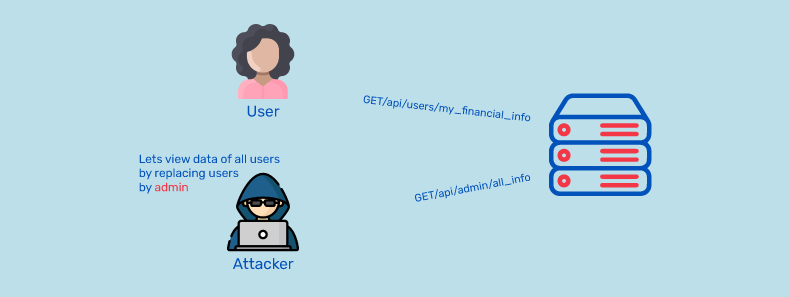
Broken function-level authorization is listed as the 5th most common threat in the list of OWASP Top 10 API security threats. When authorization is implemented at the functional level, it allows access to specific functions or resources based on the authenticated user. This can be an issue if that function is mistakenly left open to anyone, regardless of their authentication status.
Solutions:
- It is important to have a well-defined policy that outlines who has what level of access and roles are within the organization. This will help ensure that everyone understands their responsibilities and is aware of the consequences of violating the policy.
- Additionally, it is important to regularly audit your system to make sure that the access controls are still effective and that no unauthorized users have gained access.
6. Mass Assignment
Applications that rely on user input (such as contact forms, search results, etc.) are susceptible to API security attacks. Mass assignment vulnerability is when a web application takes a set of user-provided data and automatically assigns it to variables in the application code without proper sanitization.
This security flaw allows an attacker to inject malicious data into an application’s input fields, resulting in the execution of unintended actions or the exposure of sensitive data. Applications that use the JSON (JavaScript Object Notation) format especially are vulnerable to this type of attack because they often accept input in the form of JSON data.
Solutions:
- Enforce proper penetration testing to find vulnerabilities.
- Avoid direct mapping of client inputs to internal input variables.
- Whitelist properties, which a client can access and make sure only those with the proper privilege can access the API response.
7. Security Misconfiguration
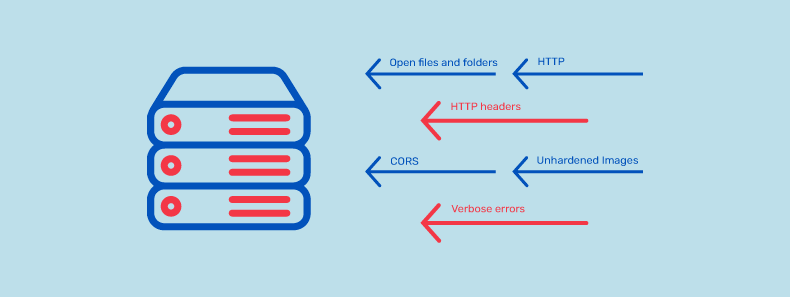
The following vulnerability in our list of API security threats is Security Misconfiguration. A security misconfiguration is an unintentional error in the security settings of an application that can leave it open to attack. This is a most consent security threat against both API and non-API applications.
This API vulnerability is commonly a result of ad-hoc configurations, insecure default configurations, misconfigured HTTP headers, permissive CORS (Cross-Origin resource sharing), unnecessary HTTP methods, and verbose error messages comprising sensitive information.
Solutions:
- Consider doing security audits periodically to detect missing patches or misconfigurations. Don’t rely on default configurations.
- Also, avoid inserting sensitive data in error messages.
8. Injection
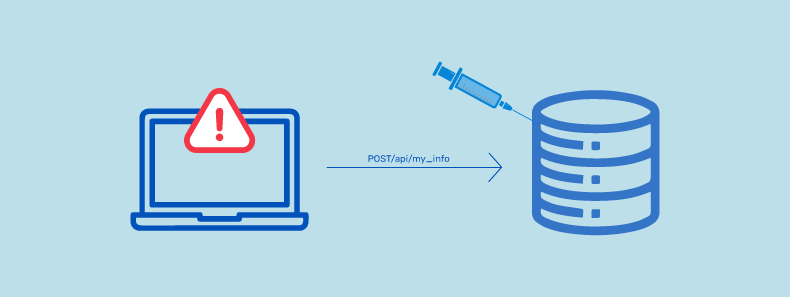
The injection is an API security issue that can occur when an application takes input from an untrusted source and uses it unsafely. This could allow attackers to execute malicious code or access sensitive data. Typical attack vectors of malicious API injection threats include SQL, OS commands, and XML.
FOR EXAMPLE, in SQL injection, an attacker sends a specially crafted request that includes malicious code. The code will be executed by the application when it parses the input.
Solutions:
- Always monitor API requests for unusual behavior using a Web Application Firewall (WAF).
- Use an API Gateway.
- Validate user inputs to avoid untrusted and SQL data types.
9. Improper Assets Management
API security attacks target outdated or older APIs. These APIs are so vulnerable that older assets are hardly checked for security issues.
Further APIs typically expose more endpoints than traditional monolithic web applications. Also, APIs have many different functions, versions, and parameters, which affect the behavior of API endpoints. This makes proper documentation highly important because attackers target to exploit incomplete, obsolete, or undocumented API functionalities.
Solutions:
Synchronized documentation and properly deployed API versions inventory play a vital role in mitigating API security threats, which exploits exposed debug endpoints, and deprecated API versions.
10. Insufficient Logging & Monitoring
API security threats are often missed because of poor logging and monitoring practices. If businesses do not have good logging and monitoring in place, they cannot detect or fix API vulnerabilities and abuse attempts when they occur.
Many businesses only concentrate on infrastructure logging like server logins and network events logging. The lack of APIs-specific monitoring leaves the door open for attackers to exploit them and gain access to the back-end systems. This can lead to data theft, fraud, and other criminal activities.
Solutions:
API logging is essential for ensuring the security and stability of your API. It can help identify any potentially malicious activity taking place with the API. It can also help identify usage spikes or drops that may be caused by a software issue or an attack on the system.
By monitoring for any abnormal behavior, you can quickly identify and address any issues before they cause harm to your API or its users.
Strengthen Your API Security
API attacks are a serious problem that can result in significant financial losses. To stay ahead of hackers, it’s important to have a robust security system in place that can identify and block malicious requests.
It is also important to adhere to some advanced API security best practices if you plan to share your APIs publicly (using strong authentication and authorization, encrypting traffic, rate limit, to name a few). You also need to test your API regularly for vulnerabilities so that you can fix them before they are exploited.
To further enhance your defense against API security attacks, you can use WAAP (Web Application and API Protection) which brings together Web Application Firewalls, Anti-DDoS Solutions, API protection, and Bot Mitigation.
Found this article interesting? Follow Indusface on Facebook, Twitter, and LinkedIn to read more exclusive content we post.
The post Critical OWASP Top 10 API Security Threats appeared first on Indusface.
*** This is a Security Bloggers Network syndicated blog from Indusface authored by Vinugayathri Chinnasamy. Read the original post at: https://www.indusface.com/blog/critical-owasp-top-10-api-security-threats/