Contents:
The LockBit ransomware was launched in September 2019 as a ransomware-as-a-service. The RaaS concept is similar to SaaS (Software as a Service) and PaaS (Platform as a Service) concepts since the malicious actors do not need to create malware kits from scratch, as they can rent or purchase them from a RaaS provider.
This type of ransomware works just like a business, the affiliates earning 70% to 80% of the ransom payment, whilst the LockBit developers can keep the rest.
The ransomware operation has been very active, having representatives of the gang promoting the activity and providing support on hacking forums, and when ransomware topics started being banned on hacking forums, LockBit ransomware started to promote the LockBit 2.0 ransomware-as-a-service operation on their data leak site.
Lockbit 2.0 Comes With New Features
LockBit 2.0 apparently comes with a long list of features, as the developers claim to have automated the ransomware distribution throughout a Windows domain without needing any scripts.
The threat actors breach a network and gain control of the domain controller, as they utilize third-party software to deploy scripts that disable antivirus and then execute ransomware on the machines on the network.
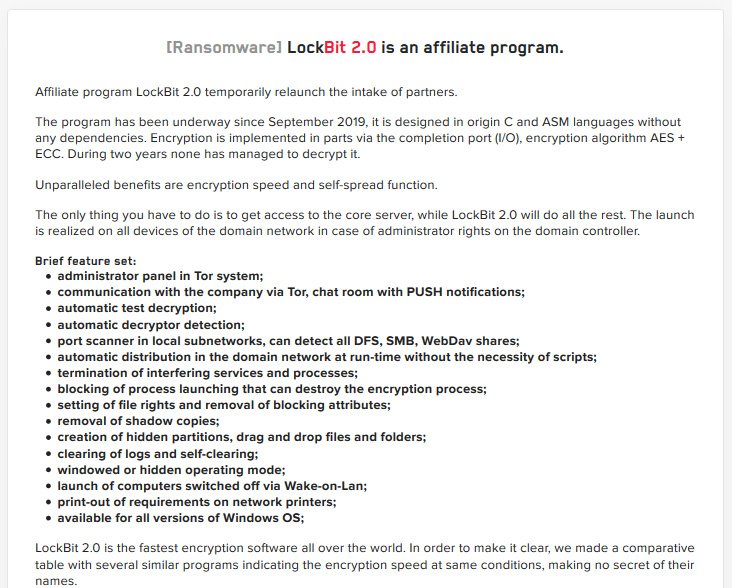
The researchers at MalwareHunterTeam analyzed the samples of the LockBit 2.0 ransomware discovered and found out that the threat actors automated this process making the ransomware distribute itself throughout a domain when executed on a domain controller, as it is able to create new group policies on the domain controller that will be then pushed out to every device on the network.
The policies in question disable Microsoft Defender’s real-time protection, alerts, submitting samples to Microsoft, and default actions when detecting malicious files, alongside creating other group policies, including one that creates a scheduled task on Windows devices that launch the ransomware executable.
Vitali Kremez declared for BleepingComputer that the ransomware will use the Windows Active Directory APIs in order to be able to perform LDAP queries against the domain controller’s ADS to get a list of computers, and in this way, the ransomware executable will be copied to each device’s desktop and the scheduled task configured by group policies will launch the ransomware using the UAC bypass.
This is the first ransomware operation to automate this process, and it allows a threat actor to disable Microsoft Defender and execute the ransomware on the entire network with a single command. A new version of the LockBit 2.0 ransomware has been found that automates the interaction and subsequent encryption of a Windows domain using Active Directory group policies.
The malware added a novel approach of interacting with active directory propagating ransomware to local domains as well as built-in updating global policy with anti-virus disable making “pentester” operations easier for new malware operators.
LockBit 2.0 also has an interesting feature that was previously used by the Egregor Ransomware operation. This feature is able to print bomb the ransom note to all networked printers.

In the Egregor attack that took place against Cencosud, this specific feature caused the ransom notes to shoot out of receipt printers after they conducted the attack.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










