Contents:
According to a new study on the state of IoT devices left on corporate networks during the COVID-19 pandemic, this type of devices is a major source of security compromise.
Zscaler researchers analyzed over 575 million device transactions and 300,000 IoT malware attacks blocked over the course of two weeks in December 2020. A 700% increase was observed when compared to pre-pandemic findings.
These attacks targeted 553 different device types, including printers, digital signage, and smart TVs, all connected to and communicating with corporate IT networks while many employees were working remotely during the COVID-19 pandemic.
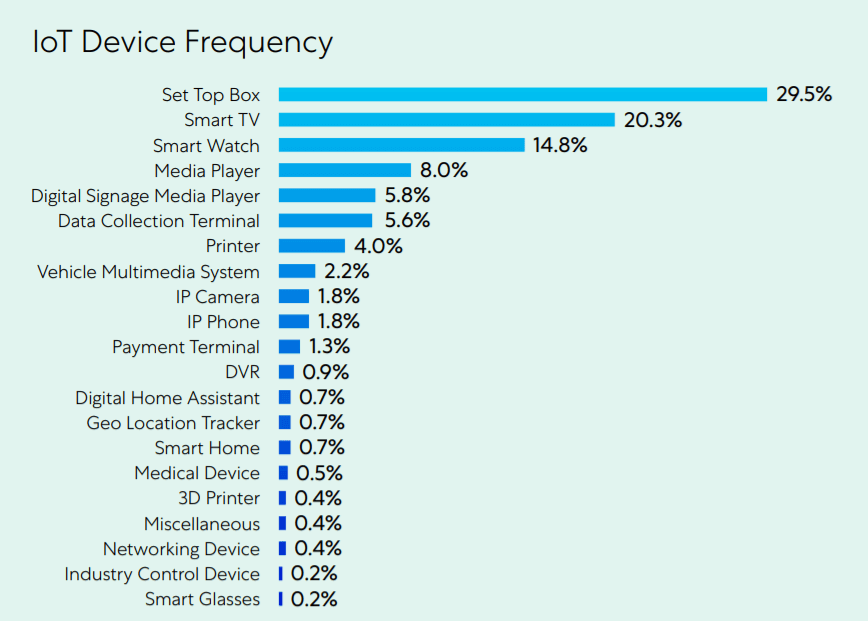
Image Source: Zscaler
The research team identified the most vulnerable IoT devices, most common attack origins and destinations, and the malware families responsible for the majority of malicious traffic to better help enterprises protect their valuable data.
Key Findings
- Despite much of the global workforce working from home, IoT malware on corporate networks has increased by 700% since 2019;
- Due to their variety, low percentage of encrypted communication, and connections to suspicious destinations, entertainment, and home automation devices posed the most risk;
- Gafgyt and Mirai, malware families popularly used in botnets, accounted for 97% of the IoT malware payloads;
- Technology, manufacturing, retail & wholesale, and healthcare industries accounted for 98% of IoT attack victims;
- Most attacks originated in China, the United States, and India, while most targets for IoT attacks were in Ireland, the United States, and China.
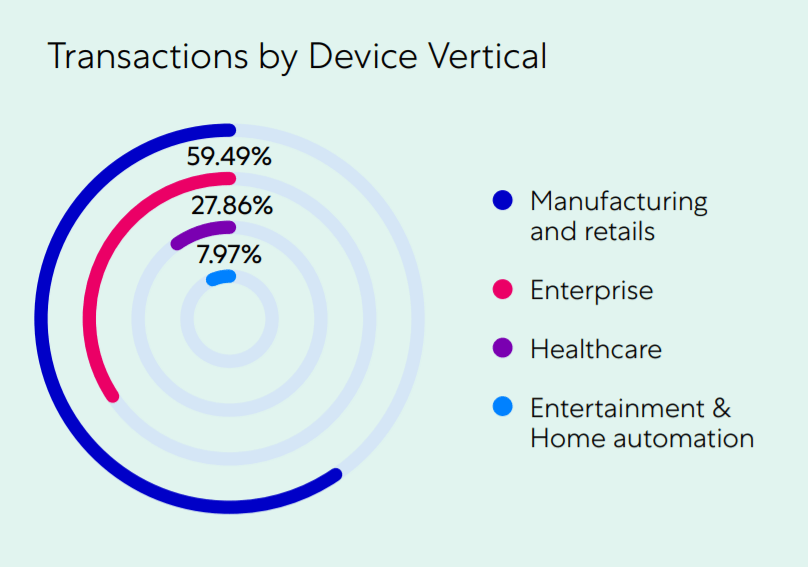
Image Source: Zscaler
The researchers also observed that 76% of total transactions from IoT devices occurred over plain-text channels, with only 24% of transactions occurring over secure encrypted channels.
While this ratio seems unacceptably low, it is almost a 3x improvement from our 2019 study, in which only 8.5 percent of IoT communications were encrypted. Nonetheless, the security risk persists: plaintext communications are much easier for attackers to spy on or, worse, to intercept and modify, allowing them to exploit the IoT devices for malicious purposes.
How to Improve Your IoT Security
Change your default passwords and usernames
For the best results, we recommend you make the password at least 10 characters long, and use at least 1 capitalized letter, 1 normalized one, 1 number, and 1 special character, such as an * or a &.
Also, try to have a different password for each device. That way, if one device gets hacked, then you can rely on the other ones.
Update to the Latest Software
The manufacturers of the best IoT devices release frequent updates to improve functionality and also patch security vulnerabilities. For this reason, try to make sure your device receives these updates whenever they are available.
Login Lock Settings
Even strong passwords and custom usernames can be vulnerable to a dictionary or brute force attack. These will bombard a login page with countless password combinations until it hits the right one.
iPhones for instance, have a setting that locks the PIN authentication after too many attempts. At the 10th attempt, it completely wipes the device.
IoT devices with good built-in security should have a similar option you can use to ensure their login integrity.
Two-Factor Authentication
The Internet of Things has lagged behind other services in implementing two-factor authentication, but as the industry matures, the feature will become more and more prevalent.
In the meantime, be sure to activate it whenever your devices support it.
Physical Weaknesses in IoT Devices
Sometimes, all it takes to infect a PC is to introduce a USB stick in it and let Windows autorun the USB, and by implication the malware. The same principles apply to smart devices. If it has a USB in it, then all a malicious hacker has to do is to plug it in, wait a bit, and that’s it.
If you can, try to place your device in such a way so that sticking a USB stick in it isn’t a straightforward process.
Encryption
Most smart devices work by communicating with a central server, Internet network, or smartphone. Unfortunately, the information isn’t properly encrypted in most cases. Either the devices are too small to carry a strong processor, or the manufacturer decided to cut costs (including security features).
Whenever available, we strongly recommend you activate the option to encrypt the data it sends and receives.
Create A Second Network for Your IoT Devices
A good way to secure your smart devices is to create a separate network for them to communicate in.
If you want to control your smart devices from your phone, you’ll need to switch between Wi-Fi to control your IoT network.
Secure Your Home Wi-Fi
Your Wi-Fi router is one of the first attack points for a malicious hacker. To make sure it is secure, we suggest you do the following:
- Use a strong and secure password.
- Change your username, and make it non-recognizable. Don’t make it easy for an attacker to identify which Wi-Fi is yours.
- Set up a firewall to protect your Wi-Fi. In most cases, the firewall will be software-based, but some routers come with a preinstalled hardware.
- Disable guest network access for your wireless network.
Here’s a more in-depth guide on how to protect your wireless network from outside intrusion that you might find useful.
Disconnect the Device from the Internet When You Don’t Use It
Devices such as Smart TVs don’t need to be permanently connected to the Internet. By keeping them off the Internet, you limit the time interval in which a cybercriminal could attempt to break its security.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security