Cyber Threats Haunting IoT Devices in 2021
With new technological advancements coming to light every day, the supply and demand for IoT devices has increased significantly. Humans have started relying on these devices for even the most basic everyday functions. In fact, as per a study conducted by IDC, 4 out of 5 people check their phones within 15 minutes of waking up! With IoT devices taking over our daily lives, cyber criminals are a little too ambitious to let the opportunity slide.
As IoT devices store, transmit and process so much essential data every day, they serve as the perfect target for cyber criminals. According to an article published by Cyber Magazine, IoT devices suffer an average of 5,200 cyber attacks every month. While businesses are reaping huge benefits from the IoT ecosystem, the risk of cyber attacks has increased exponentially as well.
Major IoT Cyber Threats in 2021
There are a number of cyber risks plaguing the world of IoT devices. Some of the major IoT cyber threats in the current times include:
Get in!
Here’s an opportunity for you to stand out from the crowd!
Join
our weekly newsletter Cyber Times and become a part of our Cyber Resilient Community
#1 Absence of Updates and Unencrypted Updates
Another primary cyber risk associated with IoT devices is the lack of regular updates and weak update mechanisms. These devices may be secure initially, however, they become vulnerable with the discovery of new security bugs or issues. If these bugs and issues are not fixed through regular updates, the devices become exposed to attacks.
Several old devices don’t even provide any security updates and most of the newer models do not ensure secure installation of security patches. The absence of proper encryption in a device’s security patch installation process significantly increases the risk of code modification by threat actors.
The infamous Satori malware serves as a perfect example of such attacks. This malware delivers a worm to a vulnerable device so that the infection spreads from device to device without any human interaction. It spreads by targeting known vulnerabilities in specific ranges of IoT devices.
In December 2018, Satori infected several D-Link home routers around the globe, making them a part of the potent IoT botnet used for attacking websites and mining cryptocurrency. The routers were infected by exploiting a 2-year-old remote code-execution vulnerability.
What Can be Done?
In order to eliminate the risks associated with irregular or unsecure security updates, organizations should make it a point to use only those IoT devices that provide regular and encrypted security updates. Also, regardless of whether the updates are encrypted or not, companies worldwide should connect their IoT devices to encrypted networks while updating software.
#2 Weak Password Protection
Manufacturers of IoT devices set default passwords while selling their products. Very often, organizations overlook some basic security measures like changing these default passwords. This simple mistake enables malicious actors to gain access to the devices by using brute force and dictionary attacks.

The Mirai malware is a great example of such attacks. It infected a wide range of IoT devices including routers, video cameras and video recorders by logging in using a table of 61 common hard-coded default passwords and usernames. It successfully created a vast botnet and took over a string of 4,00,000 connected devices.
In September 2016, Mirai-infected devices were used to launch the first 1Tbps Distributed Denial-of-Service (DDoS) attack in the world on the primary servers of the internet services. The attack affected parts of Amazon Web Services along with some of its clients including Netflix, GitHub, Airbnb and Twitter.
What Can be Done?
The manufacturers of IoT devices as well as the organizations utilizing these devices should make it a priority to take appropriate measures for countering this risk. Organizations worldwide should enforce strict password policies and educate employees about the risk of password sharing and using easy-to-guess passwords.
#3 Insecure Interfaces
The major function of all IoT devices is to communicate and process data. Often, these devices come with apps, services and protocols to make it easy for the users to control them. Many manufacturers incorporate web, cloud, application API and mobile interfaces to enhance communication.
Some of the most acute IoT vulnerabilities originate from insecure interfaces. These vulnerabilities enable hackers to compromise a device and all the data it holds. Some of the most common issues associated with insecure interfaces include lack of sufficient device authorization and authentication and absence of proper encryption. Malicious actors can exploit these insecure interfaces through credential theft attacks to gain unauthorized access to the device.
What Can be Done?
The best way of preventing such attacks on an organization’s IoT devices is to establish and enforce a robust password policy for all the employees who access the device through these interfaces. Also, conduct periodic IoT security testing to make sure there are no exploitable vulnerabilities for the hackers to misuse.
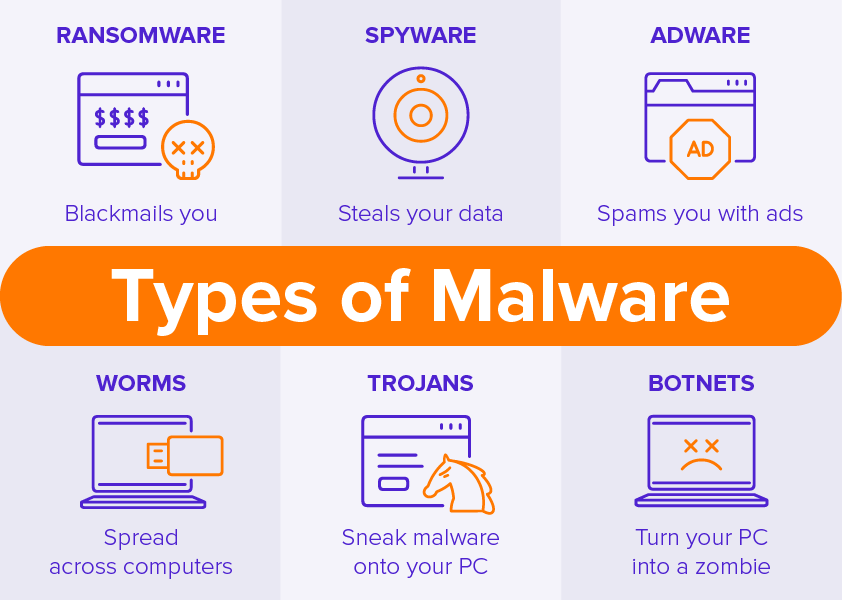
#4 Malware
Malware has become a widely used attack vector for compromising IoT devices. An article published by Global Security Mag reported that malware attacks on IoT devices in 2020 showed an increase of 66%, growing from 34.3 million attacks in 2019 to around 56.9 million attacks in 2020.
Due to the lack of built-in security features like other devices, IoT devices serve as an easy target for malware. Hackers use IoT malware for launching brute force attacks, scanning for open ports or deploying Distributed Denial of Service (DDoS) attacks.
What Can be Done?
Since you can’t simply install anti-virus software on IoT firmware, you have to take certain measures to keep your organization protected against such attacks. You can use network segmentation to stop the malware from moving laterally. Also, always change default passwords and make sure to run port scans on all the devices.
#5 Unencrypted Data
When it comes to data protection in IoT devices, lack of encryption is one of the most frequent concerns raised worldwide. One of the prime challenges associated with IoT security is that malicious actors can access confidential data from compromised devices. In fact, according to an article by IoT Now, 98% of all IoT device traffic is unencrypted.
The lack of encryption can enable threat actors to intercept a device’s network by using man-in-the-middle attacks or some other kind of eavesdropping methodology and gain access to sensitive data. Unencrypted data and networks make data breaches considerably more disastrous for organizations globally.
What Can be Done?
Organizations should make sure to encrypt the networks being used by their IoT devices for transmitting data. Data encryption prevents cyber criminals from viewing or using your data in case of unauthorized access or theft. It also ensures data privacy and confidentiality and minimizes the risks of data theft.
As IoT devices have become one of the biggest parts of every organization around the world, it’s time to recognize the threat they pose and take appropriate measures to ensure security.
Did we leave out any major cyber threats associated with IoT devices? Leave a comment below!
Get your hands on the latest DMARC report!
Check out the latest trends in Email Security
The post Cyber Threats Haunting IoT Devices in 2021 appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Dhwani Meharchandani. Read the original post at: https://www.kratikal.com/blog/cyber-threats-haunting-iot-devices-in-2021/




