A simple request to the VirusTotal scanning service reveals thousands of mobile-application databases left open to the public by developers in a three-month period.
March 15, 2022

An easy search of VirusTotal for open Firebase databases found more than 2,100 datastores used by mobile applications were left accessible by developers, exposing company bank balances, family photos, and sensitive information from healthcare applications, according to researchers.
The mobile applications ranged from relatively unpopular apps — such as a dating app with more than 10,000 downloads — to far more common apps, such as a customer portal for a South American department store chain with more than 10 million downloads. The department store application, for example, mistakenly exposed its API gateway credentials and keys, while a completely unsecured database for a running tracker left GPS coordinates, users' heart rates, and other health information exposed, research published on March 15 by cybersecurity firm Check Point Software Technologies shows.
As companies and developers have adopted cloud-native technologies, security has typically lagged behind, says Lotem Finkelsteen, head of threat intelligence and research at Check Point Software.
"While cloud environments replaced traditional on-prem servers, it has also opened the assets to the Internet, outside of the perimeter," he says. "Developers who are used to on-site servers tend to forget it and use them while trusting security [which may not be present] to protect the network."
The data leaks found by Check Point researchers are the latest caused by openly accessible database backends to mobile applications or cloud services. From an exposed Amazon Web Service (AWS) Simple Storage Service (S3) bucket leaking a half-million documents to publicly accessible MongoDB instances leaking 700,000 guest records from Choice Hotels, misconfigurations have caused enormous data breaches in recent years.
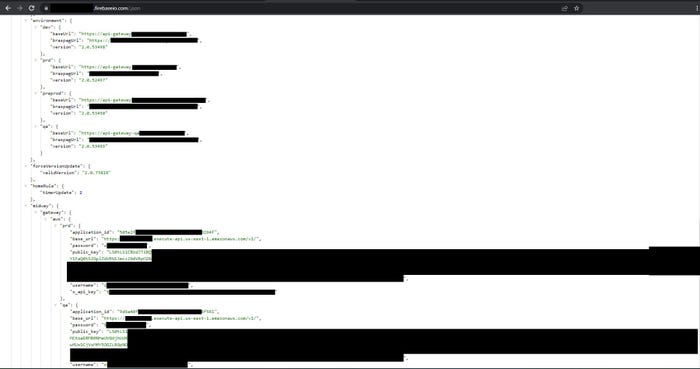
Open DB from a widely used e-commerce mobile application with cleartext credentials. Source: Check Point Software Technologies
Even cybersecurity firms are not immune to the issue. In early March, security firm Reposify scanned the networks of 35 major cybersecurity firms, finding that 86% of the companies exposed at least one sensitive remote-access service and 80% exposed network assets. More than half (51%) also had at least one exposed database, including 72% with an exposed PostrgreSQL database instance, 50% with an exposed OracleDB instance, and 28% and 21% with an exposed MySQL and MSSQL instance, respectfully, the firm found.
"Databases are modern treasure chests — the severity of the attack will depend directly on the type of data they hold," says Dor Levy, director of security research at Reposify.
Google Firebase Databases Misconfigured
In the latest research, Check Point Software researchers enumerated 2,113 Firebase databases that appeared to have been left in publicly accessible "test mode" or had exposed credentials that allowed the company's researchers to access the database. Firebase is a Google service to provide easily integrated and managed backends for mobile applications.
Check Point Software researchers used a search of the malware and malicious URL database VirusTotal, also owned by Google, to search for open databases. Developers often upload their apps to VirusTotal to make sure that they are not flagged as malicious, according to Check Point Software. About 5% of the more than 100,000 Firebase applications uploaded to VirusTotal had the address for an open database.
The research demonstrated how easily attackers could find potentially valuable data sets stored in the cloud and exposed to the public. Any hacker could search VirusTotal for public files and retrieve the full address of the cloud backend, which could then be accessed if left in test mode or with exposed credentials, Check Point Software's Finkelsteen said in an earlier statement.
"Everything we found is available to anyone," he said. "Ultimately, with this research we prove how easy it is for a data breach or exploitation to occur. The amount of data that sits openly and that is available to anyone on the cloud is crazy. It is much easier to breach than we think."
A logo-design application with more than 10 million downloads exposed approximately 130,000 usernames, email addresses, and passwords, according to Check Point researchers. Other applications include an audio social-media app and a bookkeeping app for small and midsize businesses.
The open databases do not just expose sensitive data, but — since they allow data to be written to the database — they could be abused by an attacker to change values in the database, inject malicious content into the application on users' devices, or encrypt the database for ransom. Misconfiguration is the leading cause of data breaches in the Information industry — accounting for more than 70% of breaches — and is often among the top three causes of breaches for other industries, according to Verizon's "2021 Data Breach Investigations Report" (DBIR).
"We have to assume that any tool available to us is also available to hackers for exploitation — unfortunately, that’s part and parcel of cybersecurity protocol," says Reposify's Levy. "Searchable services such as [Google, Shodan, and VirusTotal] are a good starting point for any attack surface research or audit. The issue is finding all the associated services belonging to a specific target that need to be protected, audited, and accounted for."
Check Point Software notified the app developers mentioned in its advisory, stressing that the security misconfiguration is not the fault of Google Firebase, which offers ways to better secure assets.
"Cloud technologies have grown so fast that developers are struggling to catch up and leave their databases open to everyone by mistake," Check Point's Finkelsteen says, adding: "Developers should be aware of the blessing of cloud technologies but also the dangers. Security experts should facilitate the transition to cloud and cover mistakes their developers do."
The company recommends that developers take steps. On Amazon Web Services, users should make sure that S3 buckets are not publicly accessible, while Google Cloud Platform users should lock down the Cloud Storage DB against anonymous or public access. Last, Microsoft Azure users can set the default network access for Storage Accounts to Deny.
About the Author(s)
You May Also Like
The fuel in the new AI race: Data
April 23, 2024Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




