Contents:
An email marketing account that belongs to the American chain of fast casual restaurants specializing in tacos Chipotle has been compromised by cybercriminals who used it to conduct a phishing campaign.
Threat actors send out phishing emails in an attempt to convince their targets into clicking on malicious links.
Almost all the messages guided the potential victims to credential-collecting websites posing as services from a banking organization and tech company Microsoft. Fortunately, just a few phishing emails had malware attachments.
How Did the Chipotle Phishing Attack Happen?
During the phishing operation, more than 120 malicious emails were sent from a hacked Mailgun account that the American business used for email marketing purposes [mail.chipotle.com].
It is important to know that utilizing an authentic email address increases the chances of a successful attack especially when there are automated protection solutions in place that verify if email addresses pass the DomainKeys Identified Mail (DKIM) and Sender Policy Framework authentication methods.
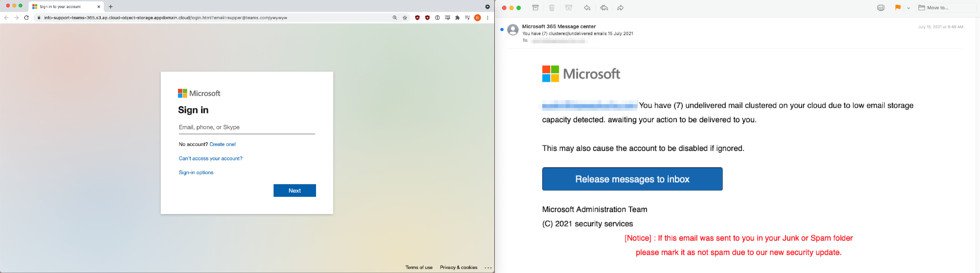
Most of the messages pretended to be from Microsoft having the intention to harvest login information from the recipients. In a blog post, email security company Inky stated that they detected 105 such emails in this three-day-long phishing operation.
Almost everyone has a Microsoft account, and logins there can lead to all kinds of interesting data, including other logins, trade secrets, financial details, and other intelligence.
According to BleepingComputer, the emails seemed to come from “Microsoft 365 Message center” and notified the victim of emails that could not be sent “due to low email storage” in the cloud.
So when the user clicks on the button that supposedly “release messages to inbox” he is immediately redirected to a false Microsoft login page that collects the confidential data.
The attackers also posed as the United Services Automobile Association (USAA), a San Antonio-based Fortune 500 diversified financial services group of companies that provides banking, investing, and insurance to people and families who serve or served, in the United States Armed Forces.
While the email security firm didn’t reveal what kind of threat was delivered, business email compromise (BEC) fraudsters frequently use phishing to deliver information stealers to harvest data that can be used for the social engineering part of the scam.
Hacking an email marketing platform for phishing attacks has been described earlier this year as Microsoft revealed it has discovered a wide-scale malicious email campaign operated by Nobelium, the group responsible for the SolarWinds attacks.
The researchers at Inky declared that nothing shows the latest phishing operation was conducted by the same threat actors.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










