Contents:
REvil ransomware has fully returned and is attacking new victims and publishing stolen files on a data leak site.
As my colleague Elena explained in an article, Sodinokibi ransomware is a Ransomware-as-a-Service.
Sodinokibi was discovered in 2019 and is highly evasive. The group uses a special social engineering move as the ones who spread the ransomware threaten to double the ransom if not paid within a certain number of days, and this is what makes Sodinoki ransomware dangerous for companies of all sizes.
We can only assume that by feeling pressured about being apprehended, the REvil gang shut down on July 13th, 2021, leaving many victims in the dark with no way of decrypting their files.
It was believed at that time that REvil would rebrand as new ransomware, but it seems that they decided to reappear in the ransomware landscape under the same name.
What Happened?
On September 7th the Tor payment/negotiation and data leak sites turned back on and became accessible, allowing the users to log in to the Tor payment site and negotiate with the ransomware gang.
The timers belonging to prior victims were reset, making it look like their ransom demands were left as they were in the moment in which the ransomware gang shut down in July.
The new attacks were proven on the 9th of September, when someone uploaded a new REvil ransomware sample that was compiled on September 4th according to VirusTotal.
Meet the New REvil Representative
You might know that previously the REvil’s public representative was a threat actor known as ‘Unknown’ or ‘UNKN’.
UNKN frequently posted on hacking forums trying to recruit new affiliates and also inform about how the ransomware operation is going.
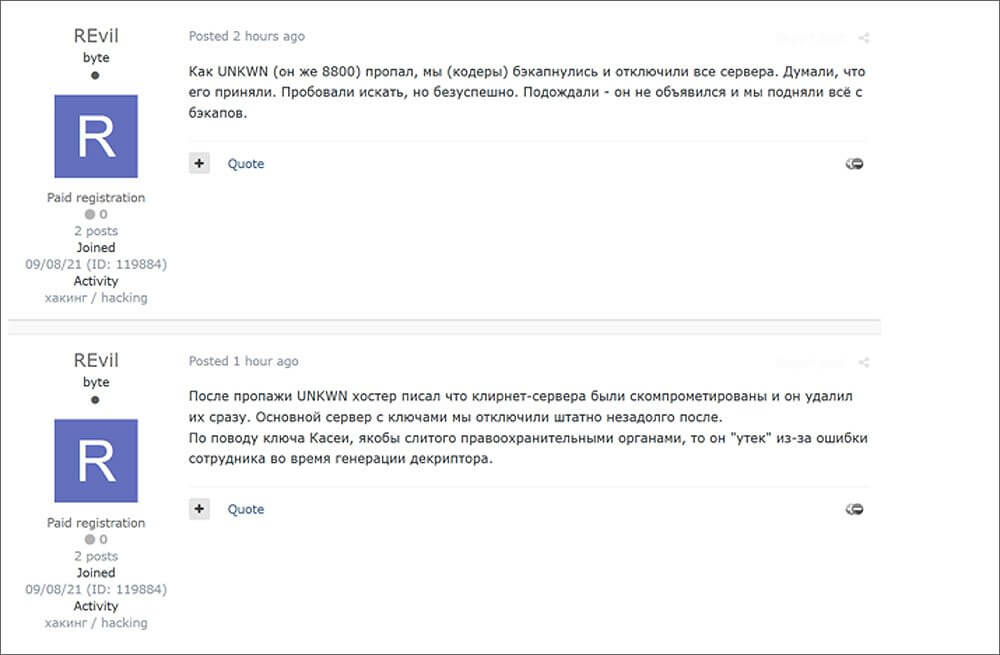
Now it seems that things are different as a new representative named ‘REvil’ started posting at hacking forums claiming that the gang briefly shut down after they thought Unknown was arrested and servers were compromised.
As Unknown (aka 8800) disappeared, we (the coders) backed up and turned off all the servers. Thought that he was arrested. We tried to search but to no avail. We waited – he did not show up and we restored everything from backups.
After UNKWN disappeared, the hoster informed us that the Clearnet servers were compromised and they deleted them at once. We shut down the main server with the keys right afterward.
Kaseya decryptor, which was allegedly leaked by the law enforcement, in fact, was leaked by one of our operators during the generation of the decryptor.
This could mean that Kaseya’s universal decryptor was obtained by law enforcement when they gained access to some of REvil’s servers.
The gang is well known for the numerous attacks against well-known companies, like JBS, Coop, Kaseya, and others.
After the Kaseya ransomware attack, it seemed that REvil shut down its infrastructure and disappeared.
They demanded $50 million for the universal decryptor, $5 million for an MSP’s decryption, and a $44,999 ransom for individual file encryption extensions at affected businesses.
The attack had wide-ranging consequences worldwide and brought the undivided attention of international law enforcement to the group.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










