Facial Scanning by Burger King in Brazil
Schneier on Security
JANUARY 10, 2024
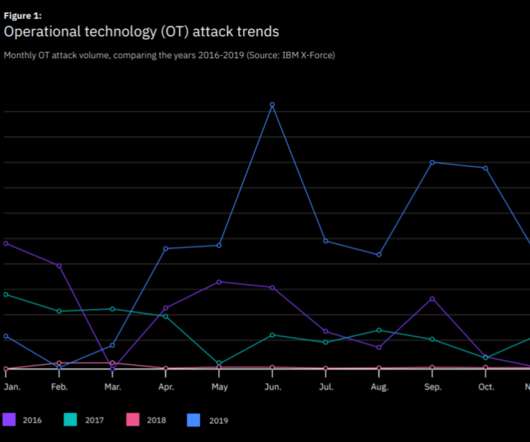
In 2000, I wrote : “If McDonald’s offered three free Big Macs for a DNA sample, there would be lines around the block.” “BK presents Hangover Whopper, a technology that scans your hangover level and offers a discount on the ideal combo to help combat it.” ” The stunt runs until January 2nd.












































Let's personalize your content