OWASP Penetration Testing: Your Ultimate Guide!
The Open Web Application Security Project (OWASP) is an online community that was established on September 9, 2001, by Mark Curphey, a cybersecurity expert, with the objective of mitigating cyber attacks. OWASP has developed a list of the top 10 attacks, called OWASP Top 10, for multiple technologies such as Web Applications, Cloud, Mobile Security, etc., to aid the internet community in combating cyberattacks and vulnerabilities related to applications. Entities across the globe refer to the OWASP standards as a baseline to review and improve their security posture when it comes to applications across the web, mobile, thick client, and over the cloud as well.
What is OWASP TOP 10?
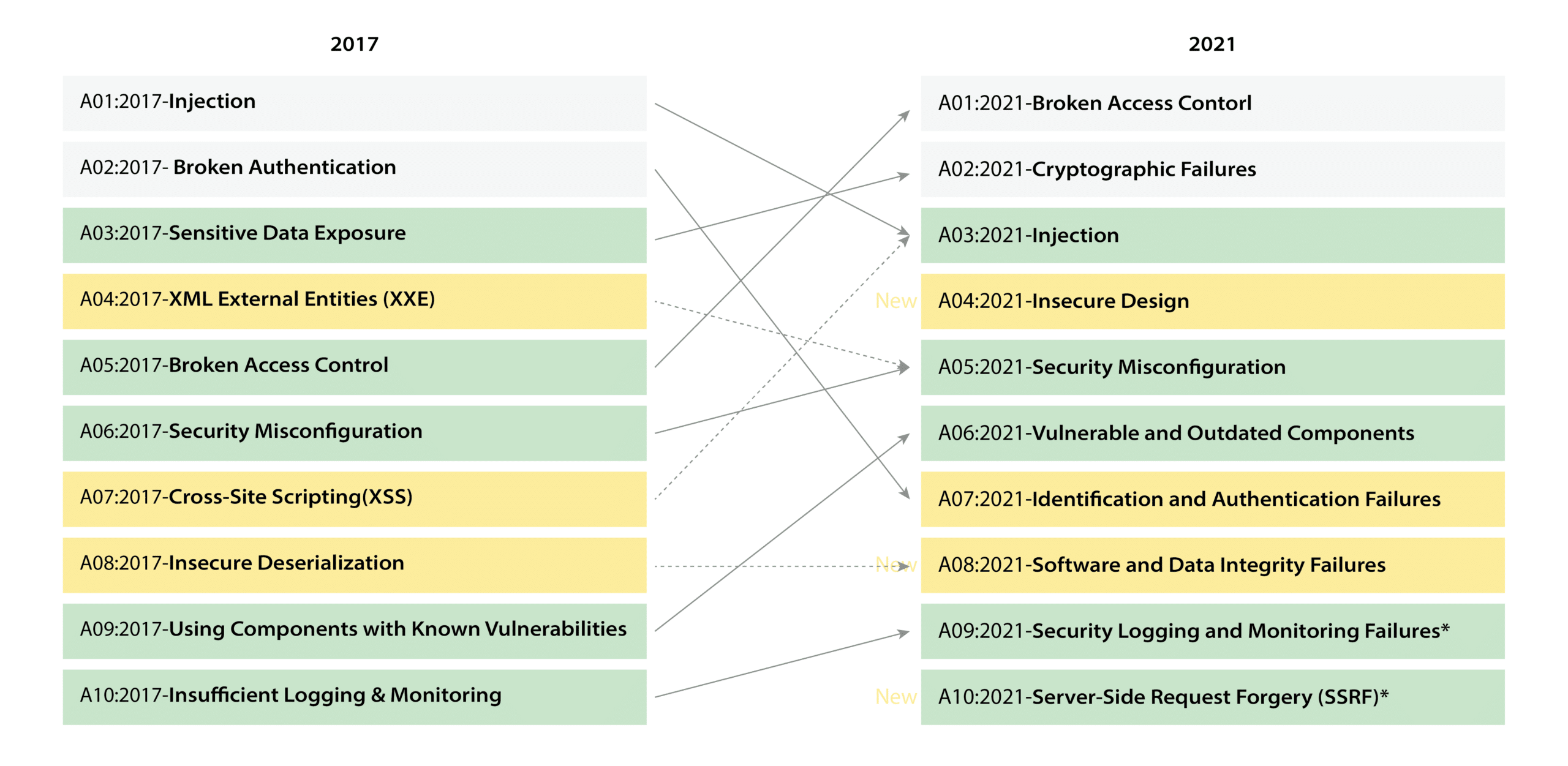
The OWASP Top 10 is a collection of security recommendations that has been maintained by the foundation since 2003. It is updated periodically to incorporate the latest advancements and developments in application security.
The importance of adopting the OWASP Top 10 lies in the actionable information it offers. The list serves as a critical security checklist when writing or reviewing code, testing various kinds of applications, helping organizations to write more secure code, and preventing critical security vulnerabilities and attack vectors in their applications.
OWASP Top 10 Vulnerabilities
In this section, we explore each of these OWASP Top 10 vulnerabilities to better understand their impact and how they can be avoided.
1. Broken Access Controls
Broken Access Control vulnerabilities are a well-known security risk that affects web applications, resulting from either inaccurate or absent authorization checks. These vulnerabilities enable unauthorized users to gain access to sensitive data or manipulate it, posing a significant threat to the application’s integrity. Attackers often exploit Broken Access Control vulnerabilities to breach the system, making them a prime target for cyberattacks.
2. Cryptographic Failures
In software development, it is imperative to encrypt sensitive data to ensure its protection. Cryptographic measures are commonly implemented to achieve this aim. Cryptographic failures can arise from a range of issues, including the use of HTTP to transmit sensitive data, the presence of hard-coded sensitive data such as API keys, employment of weak encryption, improper key management, and the lack of key rotation mechanisms. These issues must be avoided to ensure that the encrypted sensitive data remains secure.
3. Injection
Injection attacks are a prevalent form of a security breach that occurs when an attacker inputs a harmful payload into an input field on a website. The payload is then interpreted by the website and executed as a script created by the attacker. The malicious script can then cause significant damage to the website’s server and its data. These attacks can manifest in various forms, such as SQL injection, cross-site scripting (XSS), and command injection, and can be initiated through multiple entry points, including form fields, URLs, and APIs.
4. Insecure Design
Insecure design pertains to a range of security concerns that arise from inadequate knowledge and awareness of security vulnerabilities. This issue is attributable to the same underlying cause as insecure coding, namely, a lack of expertise in security matters. In many cases, security considerations are not given due importance and are not incorporated as requirements during software development.
5. Security Misconfiguration
In the realm of web application security, a security misconfiguration vulnerability arises when a component of the application is vulnerable to attack as a result of a misconfigured or insecurely configured option. These types of vulnerabilities can leave the entire application stack open to exploitation, thereby rendering the application susceptible to attacks that may originate from any part of the stack.
6. Vulnerable and Outdated Components
A prevalent challenge encountered in web application development is the utilization of components that contain known vulnerabilities or outdated components. This issue typically arises not because of a lack of awareness but because of the complexity involved in migrating to updated versions. Components such as jQuery, Bootstrap, and AngularJS, which are commonly used in web applications, are particularly vulnerable. Being popular components, they are more susceptible to hacking attacks, resulting in an increased likelihood of vulnerabilities.
7. Identification and Authentication Failures
Identification and Authentication Failures, previously referred to as Broken Authentication, have been incorporated into the Common Weakness Enumerations (CWEs). This category includes several common vulnerabilities, such as inadequate protection against brute force attacks, weak password policies, insufficient or weak multi-factor authentication, and improper session management.
8. Software and Data Integrity Failures
In software engineering, the prevalence of data integrity failures remains high. Ensuring data integrity requires careful attention to code implementation. Failure to maintain data integrity can result in security vulnerabilities such as insecure deserialization, untrusted Content Delivery Networks (CDNs), and insecure Continuous Integration/Continuous Deployment (CI/CD) pipelines.
9. Insufficient Logging and Monitoring
Log monitoring plays a pivotal role in a comprehensive security program. It is an essential component of log management, enabling organizations to identify and investigate security incidents promptly. However, approximately 2 out of every 5 enterprises lack the capability to detect and analyze security events in near real-time due to inadequate customization and management of their log monitoring systems.
10. Server-Side Request Forgery (SSRF)
Server-side request forgery (SSRF) is a security weakness that arises when an application sends a request to a remote host that is not authenticated and fails to adequately verify the request. In essence, the application is deceived into making a request to a remote host that it believes to be local. This vulnerability poses a significant risk because the remote host’s software lacks authentication, making it susceptible to being compromised or running malicious code.
What is OWASP Penetration Testing?
OWASP Penetration testing involves a comprehensive assessment of an application’s security posture, using a variety of techniques and tools to simulate real-world attacks. The goal is to identify potential security weaknesses before they can be exploited by attackers, and to provide guidance on how to remediate those weaknesses.
It is an essential component of a comprehensive software security program since identifying potential vulnerabilities before they can be exploited by attackers, organizations can significantly reduce their risk of data breaches and other security incidents.
Unlocking the Advantages of OWASP Penetration Testing
OWASP Penetration Testing is an essential aspect of the information security landscape that helps organizations identify and remediate security weaknesses and vulnerabilities in web applications. The main objective of a pen test is to simulate an attacker’s behavior and evaluate the security posture of web applications to identify potential vulnerabilities that may lead to data breaches and other security incidents. Here are some of the key benefits of OWASP Penetration Testing:
1. Identify and address vulnerabilities before cybercriminals exploit them
2. Reduce the risk of data breaches and damage to services
3. Provide an independent overview of security controls and compliance assurance
4. Improve software development and quality assurance practices
5. Support more informed decision-making around security investments
OWASP Security Checklist
The OWASP Security Checklist is a standardized testing guide that has been developed by OWASP to ensure uniformity in internal penetration testing and external vendor services. The purpose of this checklist is to identify the targets that need to be tested and not to describe the testing methods.
The OWASP Security Checklist can be utilized as a Request for Proposal (RFP) template, benchmark, and guide for web security testing. The OWASP Web Security Testing Guide offers an all-inclusive guide for testing web applications and services.
The OWASP Web Security Testing Guide is the result of collective efforts from several cybersecurity professionals and volunteers who have contributed to its development. It provides a comprehensive and systematic approach to testing web application security to identify vulnerabilities and mitigate risks.
WeSecureApp’s Approach
WeSecureApp follows a systematic and comprehensive approach of OWASP guidelines to ensure that their testing is thorough and effective. Their approach can be broken down into the following steps:
Planning and Preparation: Begins by understanding the client’s requirements and objectives, including the scope of testing, the target systems, and any specific testing goals. They then create a testing plan that includes the tools, techniques, and methodologies to be used.
Reconnaissance: In this phase, WeSecureApp gathers information about the target system using both passive and active techniques. This helps to identify potential vulnerabilities that can be exploited during the testing phase.
Scanning and Enumeration: Performs vulnerability scanning using automated tools to identify known vulnerabilities. They also use manual techniques such as port scanning and service enumeration to identify any hidden or unknown vulnerabilities.
Exploitation: In this phase, WeSecureApp attempts to exploit identified vulnerabilities to gain access to the target system or data. They use a combination of automated and manual techniques to exploit vulnerabilities and gain access.
Reporting and Remediation: Provide a detailed report of the vulnerabilities identified during the testing, along with recommended remediation steps. They also offer post-testing support to ensure that any identified vulnerabilities are properly addressed.
Conclusion
OWASP Penetration Testing is a critical process for identifying security vulnerabilities in web applications and networks. By following the OWASP Security Framework and adhering to best practices, security professionals can ensure that they are conducting thorough and effective penetration tests.
It is essential to remember that penetration testing is just one component of an overall security strategy, and it should be complemented by other security measures, such as regular software updates, access controls, and firewalls. WeSecureApp’s Testing services include a thorough analysis of the target system, vulnerability scanning, manual testing, and reporting of vulnerabilities with recommended remediation steps. They also provide post-testing support to ensure that any identified vulnerabilities are properly addressed.
Recommended Reading
How to Choose a Penetration Testing Vendor Wisely?
The Penetration Testing Guide for Compliance and Audits
Red Team Assessment versus Penetration Testing
Top 7 Penetration Testing Companies in the USA
The post OWASP Penetration Testing: Your Ultimate Guide! appeared first on WeSecureApp :: Simplifying Enterprise Security.
*** This is a Security Bloggers Network syndicated blog from WeSecureApp :: Simplifying Enterprise Security authored by Khushboo Chahal. Read the original post at: https://wesecureapp.com/blog/owasp-penetration-testing-your-ultimate-guide/





