SIEM Content, False Positives and Engineering (Or Not) Security
Anton on Security
MAY 4, 2023
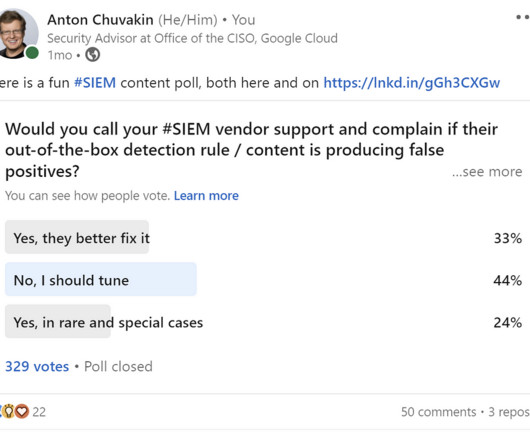
Related posts: “Detection as Code? No, Detection as COOKING!” “How How to Measure Threat Detection Quality for an Organization?” As we learned , SIEM still matters in 2023.






















Let's personalize your content