Contents:
Tropic Trooper is an independent terrorist organization that has conducted operations directed at specific targets in Taiwan, the Philippines, and Hong Kong. Since 2011, Tropic Trooper has been operating with the goal of targeting organizations in the public sector, the healthcare industry, the transportation sector, and the high technology sector.
What Happened?
Researchers in the field of cybersecurity have uncovered a new campaign that has been connected to the Chinese hacking outfit known as “Tropic Trooper.” This campaign makes use of a novel loader known as Nimbda as well as a new form of the Yahoyah trojan.
We have concluded that this activity is probably connected to Tropic Trooper, and TA428 by proxy, based on the following TTPs:
- The loading process of the final payload, from the use of steganography to hide a payload DLL inside of a downloaded image, to the exported function name of the payload DLL, invoked by SN Yahoyah in order to run the logic inside — StartWork.
- The use of TClient as a final payload.
- The C&C check-in format shared almost verbatim by SN Yahoyah and USBFerry, a malware deployed by Tropic Trooper that targets air-gapped networks. The version naming and the victim’s data formatting in both samples are very similar, considering 4 years of development and tool differences.
As BleepingComputer reports, the trojan is concealed inside a piece of greyware known as “SMS Bomber,” which is designed to launch denial of service (DoS) attacks on mobile devices by overwhelming them with a large number of text messages. Tools of this kind are often used by “beginner” threat actors with the intention of launching attacks on websites.
In addition, the threat actors have an in-depth understanding of cryptography, as shown by the fact that they extended the AES standard in a bespoke implementation, as stated in a report by Check Point.
Check Point Research has recently been tracking a cluster of malicious activity that has been going on for the past several years. The observed activity has strong connections to the Tropic Trooper cluster of activity, as documented by Trend Micro, based on shared infrastructure, tools, and coding practices. Tropic Trooper was previously observed targeting Philippines, Hong Kong and Taiwan; while the two latest are Chinese-speaking countries.
This activity in particular caught our interest due to its unusual technical quirks and targeting, as well as the use of a new net-capable strain of a previously documented piece of malware. In this article, we share our findings, with an emphasis on the technical highlights (this is a polite way of saying there won’t be an IDA screenshot of a single-byte-XOR decryption).
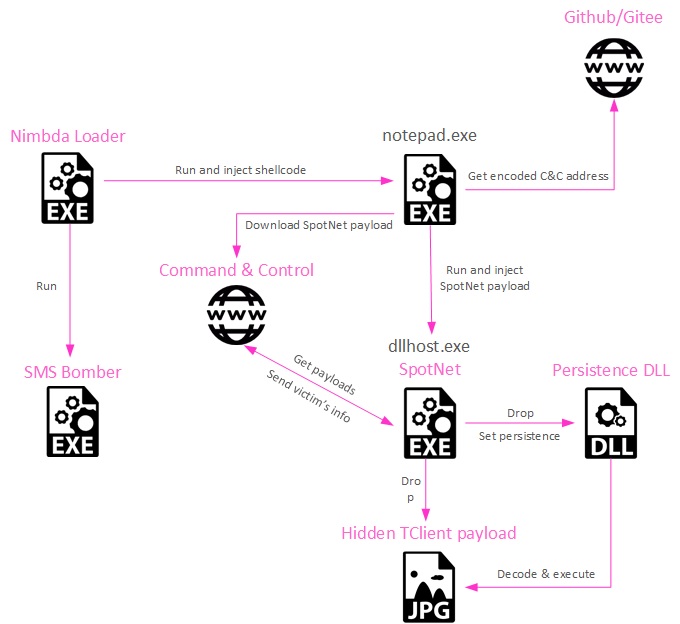
Downloading a malicious version of the SMS Bomber program, which includes the malware as well as the utility’s usual capabilities, is the first step in the infection process. The download, on the other hand, has been altered to incorporate extra code that injects itself into a process using notepad.exe.
The icon of SMS Bomber is used by the “Nimbda” loader, which also includes SMS Bomber as an embedded program. The file that was downloaded is really the “Nimbda” loader.
The loader secretly injects shellcode into the process of notepad in order to communicate with a GitHub repository, get an obfuscated executable, decode it, and then launch it by hollowing out the process of ‘dllhost.exe’ in order to execute it.
This payload is the new Yahoyah variety, and it communicates with the C2 server to relay information that it has gathered about the host, like he local wireless network SSIDs that are in close proximity to the victim machine, the computer name, the MAC address. the operating system version, the installed AV products, the availability of WeChat and Tencent files.
Steganography is used to hide the final payload, which is dumped by the Yahoyah executable. This payload is hidden in a JPG picture.
If you liked this article follow us on LinkedIn, Twitter, YouTube, Facebook, and Instagram to keep up to date with everything cybersecurity.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










