A 26-year-old Finnish man was sentenced to more than six years in prison today after being convicted of hacking into an online psychotherapy clinic, leaking tens of thousands of patient therapy records, and attempting to extort the clinic and patients.
On October 21, 2020, the Vastaamo Psychotherapy Center in Finland became the target of blackmail when a tormentor identified as “ransom_man” demanded payment of 40 bitcoins (~450,000 euros at the time) in return for a promise not to publish highly sensitive therapy session notes Vastaamo had exposed online.
Ransom_man announced on the dark web that he would start publishing 100 patient profiles every 24 hours. When Vastaamo declined to pay, ransom_man shifted to extorting individual patients. According to Finnish police, some 22,000 victims reported extortion attempts targeting them personally, targeted emails that threatened to publish their therapy notes online unless paid a 500 euro ransom.
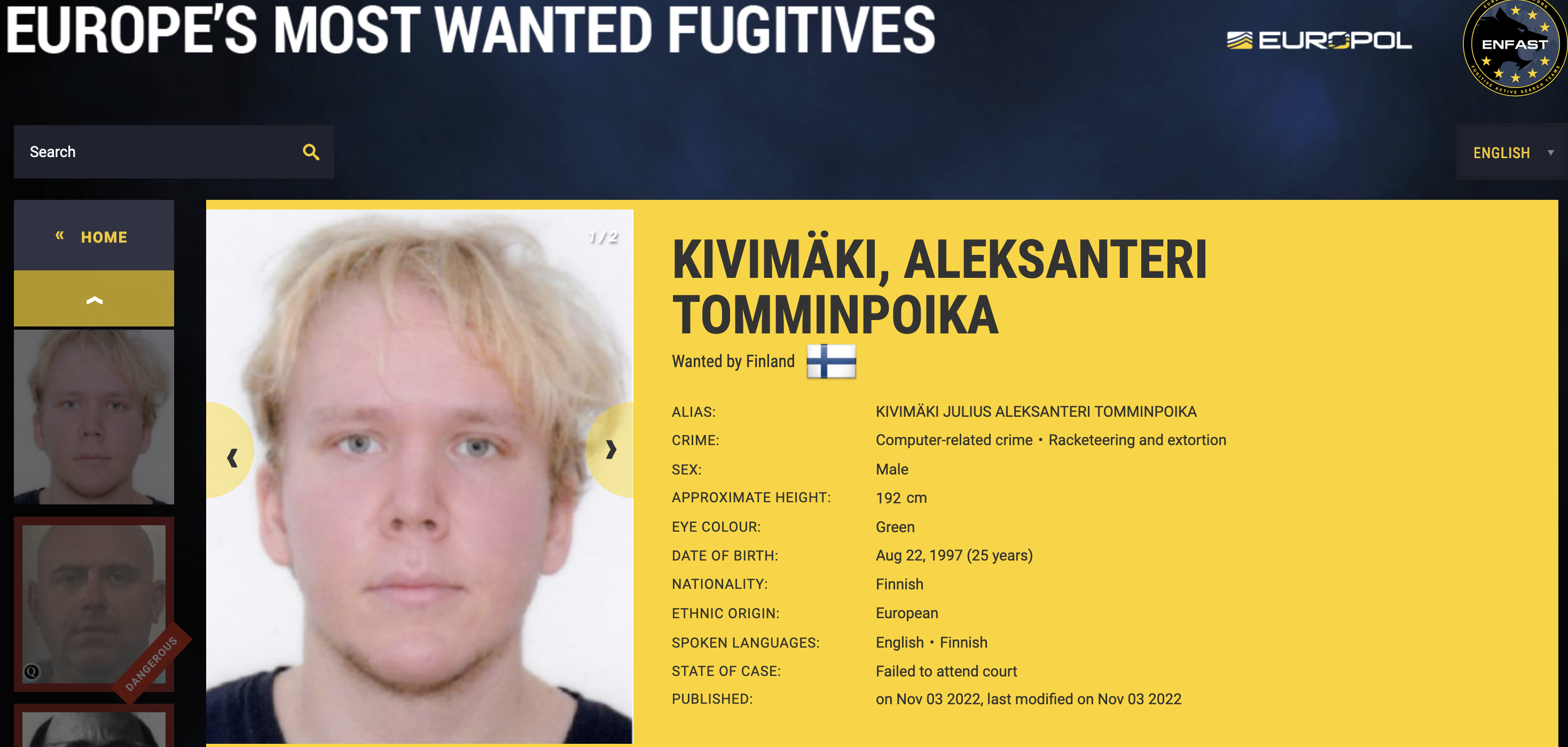
Finnish prosecutors quickly zeroed in on a suspect: Julius “Zeekill” Kivimäki, a notorious criminal hacker convicted of committing tens of thousands of cybercrimes before he became an adult. After being charged with the attack in October 2022, Kivimäki fled the country. He was arrested four months later in France, hiding out under an assumed name and passport.
Antti Kurittu is a former criminal investigator who worked on an investigation involving Kivimäki’s use of the Zbot botnet, among other activities Kivimäki engaged in as a member of the hacker group Hack the Planet (HTP).
Kurittu said the prosecution had demanded at least seven years in jail, and that the sentence handed down was six years and three months. Kurittu said prosecutors knocked a few months off of Kivimäki’s sentence because he agreed to pay compensation to his victims, and that Kivimäki will remain in prison during any appeal process.
“I think the sentencing was as expected, knowing the Finnish judicial system,” Kurittu told KrebsOnSecurity. “As Kivimäki has not been sentenced to a non-suspended prison sentence during the last five years, he will be treated as a first-timer, his previous convictions notwithstanding.”
But because juvenile convictions in Finland don’t count towards determining whether somebody is a first-time offender, Kivimäki will end up serving approximately half of his sentence.
“This seems like a short sentence when taking into account the gravity of his actions and the life-altering consequences to thousands of people, but it’s almost the maximum the law allows for,” Kurittu said.
Kivimäki initially gained notoriety as a self-professed member of the Lizard Squad, a mainly low-skilled hacker group that specialized in DDoS attacks. But American and Finnish investigators say Kivimäki’s involvement in cybercrime dates back to at least 2008, when he was introduced to a founding member of what would soon become HTP.
Finnish police said Kivimäki also used the nicknames “Ryan”, “RyanC” and “Ryan Cleary” (Ryan Cleary was actually a member of a rival hacker group — LulzSec — who was sentenced to prison for hacking).
Kivimäki and other HTP members were involved in mass-compromising web servers using known vulnerabilities, and by 2012 Kivimäki’s alias Ryan Cleary was selling access to those servers in the form of a DDoS-for-hire service. Kivimäki was 15 years old at the time.
In 2013, investigators going through devices seized from Kivimäki found computer code that had been used to crack more than 60,000 web servers using a previously unknown vulnerability in Adobe’s ColdFusion software. KrebsOnSecurity detailed the work of HTP in September 2013, after the group compromised servers inside data brokers LexisNexis, Kroll, and Dun & Bradstreet.
The group used the same ColdFusion flaws to break into the National White Collar Crime Center (NWC3), a non-profit that provides research and investigative support to the U.S. Federal Bureau of Investigation (FBI).
As KrebsOnSecurity reported at the time, this small ColdFusion botnet of data broker servers was being controlled by the same cybercriminals who’d assumed control over SSNDOB, which operated one of the underground’s most reliable services for obtaining Social Security Number, dates of birth and credit file information on U.S. residents.
Kivimäki was responsible for making an August 2014 bomb threat against former Sony Online Entertainment President John Smedley that grounded an American Airlines plane. Kivimäki also was involved in calling in multiple fake bomb threats and “swatting” incidents — reporting fake hostage situations at an address to prompt a heavily armed police response to that location.
Ville Tapio, the former CEO of Vastaamo, was fired and also prosecuted following the breach. Ransom_man bragged about Vastaamo’s sloppy security, noting the company had used the laughably weak username and password “root/root” to protect sensitive patient records.
Investigators later found Vastaamo had originally been hacked in 2018 and again in 2019. In April 2023, a Finnish court handed down a three-month sentence for Tapio, but that sentence was suspended because he had no previous criminal record.




The addiction to money makes one do strange things. Trying to gank psychiatric patients seem a desperate scrape at the bottom of the feeding trough, IMHO. I wonder how much he made off of those patients, and what got him popped from hiding…
I could be wrong, but I wouldn’t think money was his main motivation. Unless this was just a crime of opportunity (root/root? Really??) going after a shrink’s notes sounds more about having power over people. At 500 Euros/person, he wasn’t gonna get rich. But he would be able to make people grovel. I suspect that was more his motivation
Uhh … he targeted 22,000 people with the 500 euro blackmail attempt. Even if a tenth of those he contacted decided to pay, he’d get over a million. I’d say money factored pretty heavily in his decision.
“Even if a tenth of those he contacted decided to pay”
A tenth is extremely generous to the point of absurdity, non-targeted attacks like this where such a wide net is case generally have a success rate that would be a very, very small fraction of the 1/10 number you provided.
So in three years and a month or so he’s back on the street?
He didn’t make a dime out of those patients, because his blackmailing attempts failed.
Good riddance to this human garbage. He’ll be in jail again, though. His kind will never rehabilitate.
Please correct your facts:
“Investigators later found Vastaamo had originally been hacked in 2018 and again in 2019, but that Tapio never told anyone about the intrusions until ransom_man began his extortion spree.”
I have not been charged in any court case for concealing the 2018 data breach or any data leak, and the charges for concealing the 2019 data breach have been dismissed in all court cases.
“I have not been charged in any court case for concealing the 2018 data breach or any data leak, and the charges for concealing the 2019 data breach have been dismissed in all court cases.”
That’s a fair and possibly true statement. However for the purpose of full transparency; Which external stakeholders did you inform concerning the 2018 and 2019 intrusions, post detection? and when?
I am going to ignore what the judicial system thinks in this situation, because as CEO and ultimate gatekeeper of a private database of highly sensitive medical records, you had a MORAL obligation to protect the very personal details of some of society’s most vulnerable individuals and you failed miserably.
Forget the legal implications. Enlighten the audience here what processes or procedures you put in place after the initial breaches to protect your clients – other than cover your own arse and those of your investors? If you cannot or will not answer that question, methinks you have failed society as a leader .. and as human .. and should NOT be trusted with the same responsibility ever again.
When I got the first ransom message in Sep 2020, I ordered a FDIR investigation from Nixu Corporation and established an incident response team with Nixu and the National Bureau of Investigation and the National Cyber Security Center the very next day. I authorized Nixu’s experts to share all information from the investigation directly with the authorities. We also had a daily meetings with the whole incident response team during the FDIR project.
Starting from the first reply, all communication with the extortionist was carried out according to the police’s instructions, or as a police covert operation in my name, which I believe had a big impact on the fact that the perpetrator was caught and convicted.
Before the incident already in 2017, I had organized a data privacy and protection committee including a medical director, legal director, DPO and system administrator. The committee for e.g. created a risk analysis, a self-monitoring plan, and made an audition for the information system, that was renewed with help from external consultant later in the summer of 2017. At that point the system was in secure state based on the FDIR and police investigations.
Ville,
The citizens of my home country lost $2.7 billion in 2023 to financial scams directly related to corporate data breaches similar to the events that occurred at Vastaamo in 2020, and this doesn’t even take into account the social welfare or mental health impacts after the fact. As an IT professional, I’ve had years assisting private individuals picking up the pieces after they’ve become victims, directly due to irresponsible corporate security practices, leaving devastating affects. I’ve seen the impacts first hand. I’m also sick of colleagues complaining about the lack of funding or resources being denied by C Suite for basic security assets when posting record profits. Communities, globally, have a right to be angry.
I’m not going to lie. I half expected not to receive a reply from you on a public security forum such as Brians. The fact that you have, speaks volumes, considering the public scrutiny/commentary into your actions from 2017 – 2020. I respect your position and willingness to engage, but am still conflicted with parts of your statement, particularly the last paragraph.
You state that you put together a risk management team responsible for data privacy and protection as early as the summer of 2017 and the system was in a secure state based on the FDIR and police investigations, yet; “According to Nixu’s technical investigation, the best practices of safe service maintenance and protection methods were not followed in the maintenance of the Vastaamo patient information system server, which exposed the server to cyber attacks.”, as per The Office of the Data Protection Ombudsman, which was a basis for the EUR 608 000 financial sanction imposed on Vastaamo and it’s subsequent insolvency. The data wasn’t even encrypted … sigh.
If your whole business model revolved around handling and maintaining a private database of highly sensitive medical records, then as CEO, security HAS to be your number one priority, no ifs or buts. Ahead of marketing, research and software development, sales and finance, even HR. The clients safety absolutely MUST come first. The fact you deny committing the offence you were convicted of and claiming that you did not know Vastaamo’s IT security was poor for several years is evidence you still do not comprehend this simple fact. You were obligated to find out on behalf of your clients and your investors.
I’m going to refrain from vilifying you anymore than you already have been, as I see it you have already been judged by the Finnish judicial system and am sure you have already spent many sleepless nights self reflecting on these events. But I do hope that you use this experience to advocate for worlds best practice in privacy and security of end users in the tech space moving forward.
Godspeed
As Nixu’s project manager testified at my trial, Nixu’s report was misinterpreted by the authorities. At the end of Nixu’s report, as is their general practice, there were recommendations for general good practices. They were not a list of deficiencies found in this case. Health care also has its own laws and requirements for data processing, which I will not go into in depth here.
I have noticed as a broader phenomenon, that the discussion with cyber security experts goes too quickly to the point of pushing the final legal responsibility to the “C Suite” without even getting into a constructive discussion about what exactly caused the events and how similar things could possibly be prevented in the future by developing better management practices.
In this particular incident, it is clear that the classic “no resources were given, experts were not listened to, profit targets outweighed the risks” explanations does not fit the case, but nevertheless, all of them have been presented numerous times, even after the trial, where no basis was found for these claims. In this way, the right lessons are missed.
It is not realistic to expect that health care managers in an operating environment with very diverse requirements will ever become self-sufficient and information security experts capable of taking responsibility alone. However, if we do so for convenience, we are only cheating ourselves to outsource the unpleasant responsibility to a smaller group, and we will never be able to make these incidents stop.
I plan to act in the future to solve this problem, as you suggested, and I am open to further discussions on other platforms such as LinkedIn.
Respect,
Ville
Which makes it all ok I suppose?
The perp is a habitual predator criminal who has been at it at least since his early teens. There is no possibility of him becoming a positive role model or a productive law abiding citizen of any society other than his favorite criminal underground gangs. What to do with perps like him? Why not put him in a hard physical work situation, so he can get to taste what it feels like to put in a hard days work.
That’s not in contradiction to what is being stated in the article. Not being charged / getting the charges dismissed does not mean that you reported the breach to the proper authorities. The fact that you were even charged in the first place means that the process wasn’t followed, as specified. Proper reporting of breaches doesn’t usually result in being charged with concealment of that breach. If a company ever makes the mistake of granting you this responsibility again, you might want to consider spending some time constructing an infosec policy on password complexity and rotation frequency …
It is not like that.
Aaaashhahahahahha is all I can say
The humiliating publications caused several suicides. Would have thought there would be a multiple man slaughter charge and he would have gotten much stiffer punishment.
Source?
Google really isn’t that hard you know;
https://yle.fi/a/74-20077285
Finnish Public News site – English edition to make it easier for you.
My error. Thought the suicides were common knowledge. My source was here:
https://yle.fi/a/74-20077285
After he’s released, guaranteed he’ll make his way to Russia and resume his activities there, protected by and working for the FSB.
This perp clearly picked the wrong country to hide in. France? Really!? If he went to something like Russia he’d be a free man with a presidential Medal of Honor.
You failed to include most recent revelations about the perpetrator in your post. Kivimäki is also the person behind the Dnstats MITM proxy scams. He has made millions of euros by scamming darknet marketplace customers.
This is documented in the following article in a reputable Finnish weekly magazine: https://suomenkuvalehti.fi/paajutut/uudet-tiedot-yhdistavat-vastaamo-syytetyn-huijauksiin-tor-verkossa-onko-aleksanteri-kivimaki-dnstats/?shared=1288285-55987891-999 (the URL parameter is needed to bypass the paywall)
See here for English summary done by someone: http://g66ol3eb5ujdckzqqfmjsbpdjufmjd5nsgdipvxmsh7rckzlhywlzlqd.onion/post/ed279bc8924cc8e91381
The article is based on official police documents that can be currently downloaded here and which contain more specific details: http://4tdb2oju6nrrp77en6opmyfucvycs22y5ohuizfgjvbyjqjovltooyyd.onion/wujqp
it means he’s a psycho
A psycho and/or a Sadistic Internet Troll
https://www.psychologytoday.com/us/blog/your-online-secrets/201409/internet-trolls-are-narcissists-psychopaths-and-sadists
Internet Trolls Are Actually Sadists, Study Finds
https://time.com/8265/internet-trolls-are-actually-sadists-study-finds/
New Study: Most Trolls Have Subclinical Sadism
https://www.psychologytoday.com/us/blog/finding-a-new-home/202208/new-study-most-trolls-have-subclinical-sadism
Internet trolls are also real-life trolls
https://www.theguardian.com/science/head-quarters/2014/feb/25/internet-trolls-are-also-real-life-trolls
First of all, NOT a new study. Both of those articles are about ONE single report published in 2014. It was two online personality study with a total of about 1,200. That’s far from the kind of repeated quality research required in science to draw any firm conclusions. It is, at best, fodder for future research. And perhaps some slight evidence supporting the conclusions.
With that said, I don’t doubt many of these trolls are sadists or have other personally disorders.
This reprobate man-child apparently does not learn from life experiences. A couple of stints in the cooler may awaken the humanity that may possibly still exist within him. Thanks Brian, for keeping tabs on this character.
wow this is upsetting
HTP/Hack the Planet was a movement way before this clown was even born.
Thanks for sharing this.
If you think that already said this thing, then what should I say something else.