Who’s Behind the NetWire Remote Access Trojan?
Krebs on Security
MARCH 9, 2023
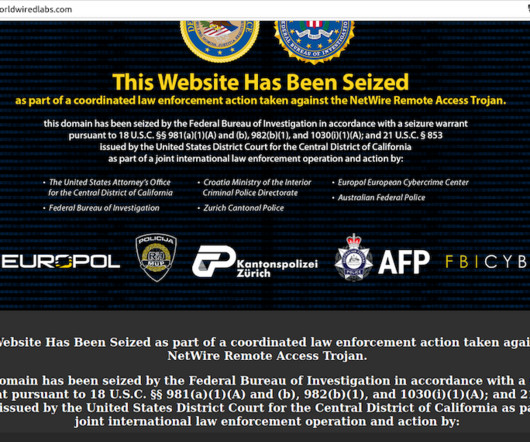
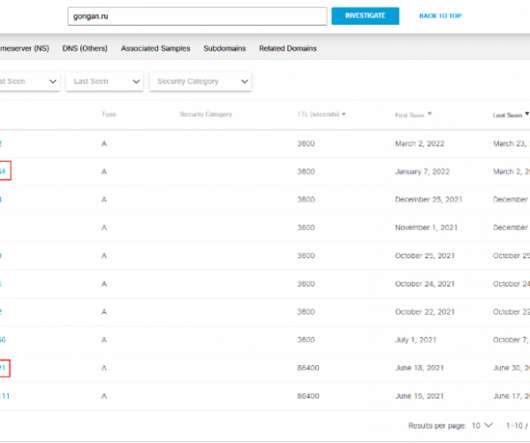
The site’s true WHOIS registration records have always been hidden by privacy protection services, but there are plenty of clues in historical Domain Name System (DNS) records for WorldWiredLabs that point in the same direction. A review of DNS records for both printschoolmedia[.]org The WorldWiredLabs website, in 2013.






































Let's personalize your content