Flight TA2541 is cleared for take off.
Wait... that's not a plane, and it's not a bird either. It's an advanced persistent threat (APT) that has troubled the transportation sector for years.
Security researchers from Proofpoint have tracked an APT that has targeted the aviation, aerospace, transportation, manufacturing, and defense industries dating back to 2017, and are calling it TA2541.
The threat actor behind this APT uses remote access trojans (RATs) capable of remotely controlling compromised systems.
Here is how Proofpoint describes the APT:
"TA2541 is a persistent cybercriminal actor that distributes various remote access trojans targeting the aviation, aerospace, transportation, and defense industries, among others. Proofpoint has tracked this threat actor since 2017, and it has used consistent tactics, techniques, and procedures (TTPs) in that time. Entities in the targeted sectors should be aware of the actor's TTPs and use the information provided for hunting and detection.
TA2541 uses themes related to aviation, transportation, and travel. When Proofpoint first started tracking this actor, the group sent macro-laden Microsoft Word attachments that downloaded the RAT payload. The group pivoted, and now they more frequently send messages with links to cloud services such as Google Drive hosting the payload. Proofpoint assesses TA2541 is a cybercriminal threat actor due to its use of specific commodity malware, broad targeting with high volume messages, and command and control infrastructure."
Phishing in the transportation sector
Security researchers say the threat actor does not rely on current events or news in social engineering schemes, as so many cybercriminals typically do. Instead, they use keywords, or "lure themes," related to transportation, such as flight, aircraft, fuel, yacht, charter, etc.
Here is one example of a phishing email requesting information on aircraft parts:
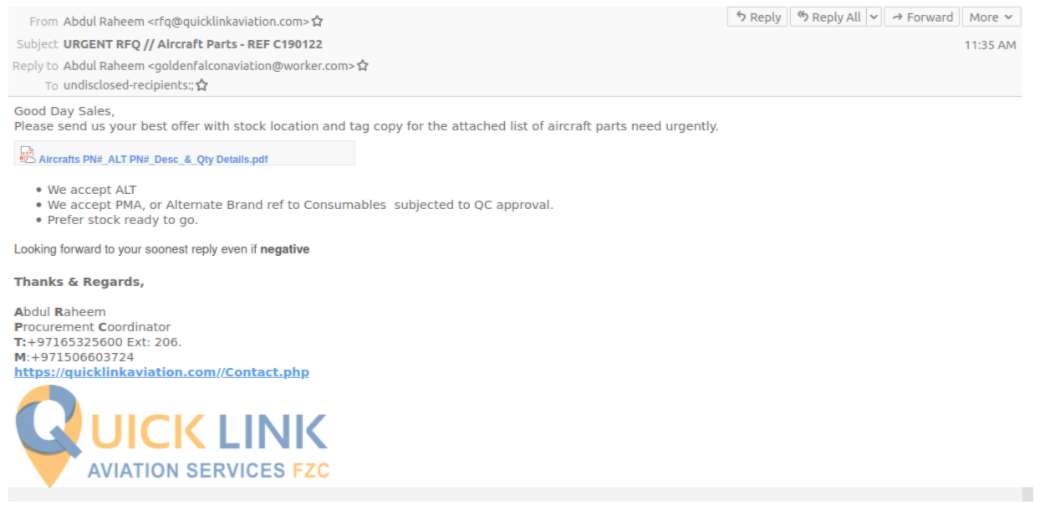
And another requesting information about ambulances:
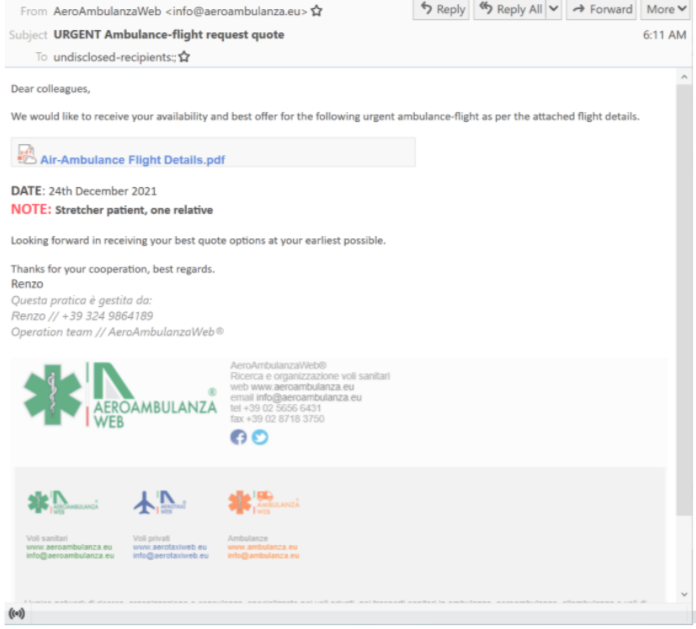
While the threat actor used generic messages like these in their social engineering attempts, they did briefly adopt messages to match COVID-19 related themes early on in the pandemic, though they quickly returned to their tried-and-true method of transportation topics.
TA2541 threat still active
In the threat actor's campaigns, they consistently sent hundreds to thousands of messages to organizations across the transportation industry. Proofpoint provided what a typical attack chain could look like:
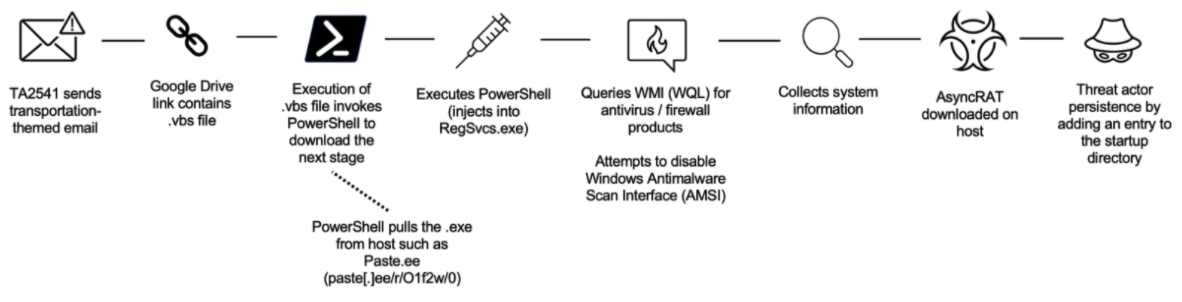
While the threat has been identified by security researchers, it is still a serious threat to organizations:
"TA2541 remains a consistent, active cybercrime threat, especially to entities in its most frequently targeted sectors. Proofpoint assesses with high confidence this threat actor will continue using the same TTPs observed in historic activity with minimal change to its lure themes, delivery, and installation. It is likely TA2541 will continue using AsyncRAT and vjw0rm in future campaigns and will likely use other commodity malware to support its objectives."
For more detailed information on TA2541, read the report from Proofpoint.




