ANALYZING SUCURI’S 2018 HACKED WEBSITE TREND REPORT
The Sucuri team recently released their second annual security report for 2018 – Hacked Website Report 2018. It looks at a representative sample of infected websites from the Sucuri customer base ONLY. This report helps understand the actions taken by bad actors once they penetrate a website.
This report analyzed 25,466 infected websites and 4,426,795 cleaned files; aggregating data from the Threat Research Group. This is the team that works side-by-side with the owners of infected websites on a daily basis, and are also the same team members that generate a lot of the research shared on the Sucuri Blog and Sucuri Labs.
This report is divided into the following sections:
- Top affected open-source CMS applications
- Outdated CMS risk assessment
- Blacklist analysis and impact on webmasters
- Malware family distribution and effects
This post will build on the analysis found in the report, and share additional insights from the reports webinar.
CMS ANALYSIS
The analysis shows that in 56% of the hacked sites the core platform was patched with the latest version. The real insights, however, come into focus as we dive into the specific CMS’ distribution in the sample base.
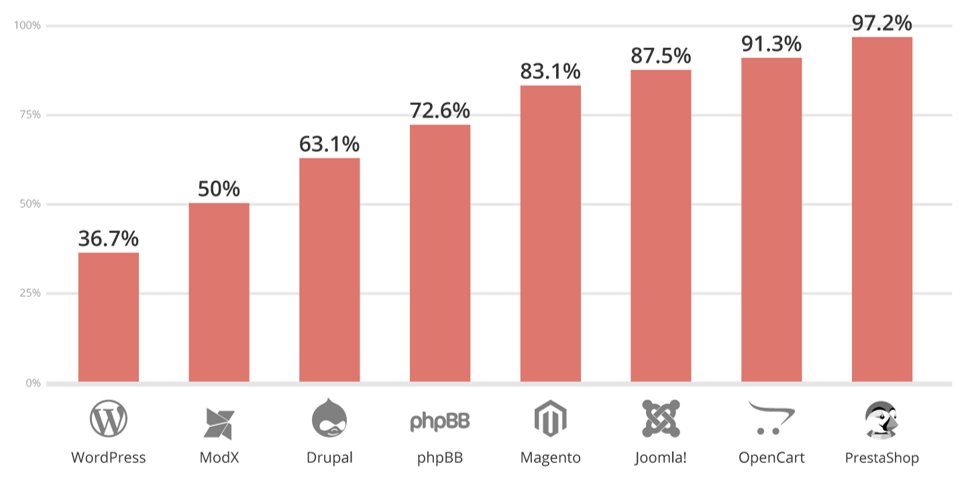
Although WordPress is the one platform that is the most up-to-date at the point of infection, it continues to be the # 1 platform we see in our environment.
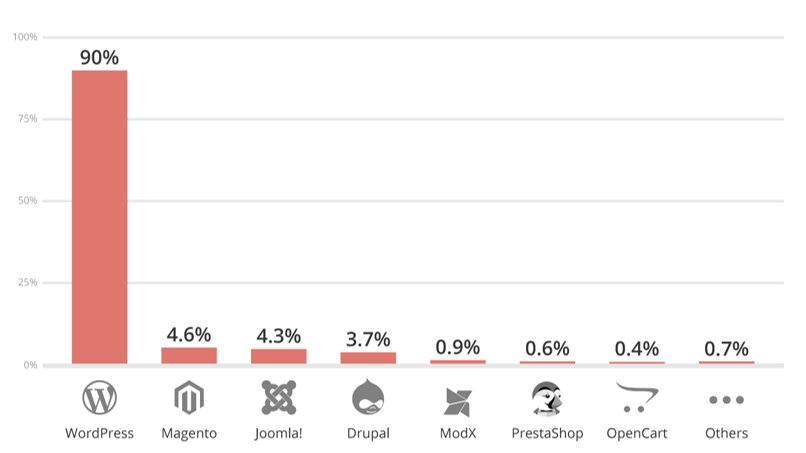
This is undoubtedly related to Sucuri’s popularity in the platform ecosystem, but with 60% market share of CMS applications, and 34% of the websites on the web its representation is also understandable. What this also highlights is that something else is contributing to these hacked sites.
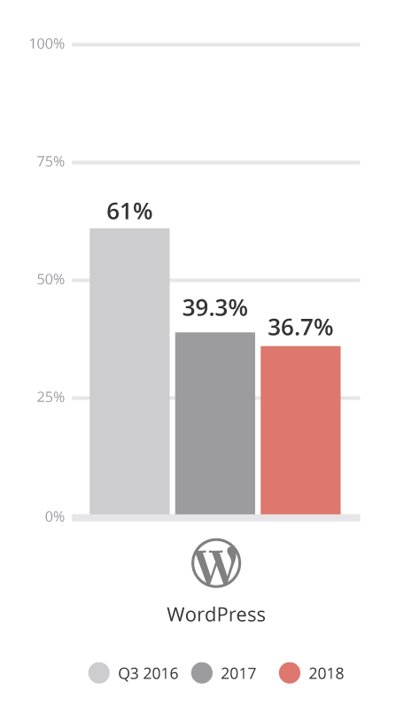
WordPress Version – In the 2016 report, 61% of the WordPress sites had been out of date at the point of infection. In 2018, this number dropped to 36.7% (2017/39.3%). Overall I’d say that’s pretty amazing, and a direct reflection of the hard work by the WordPress security team to introduce and deploy auto-updates.
E-commerce Platforms – The platforms that do concern me the most are the platforms used for online commerce. They represent a big % of the platforms that are out-of-date at the point of infection – Magento (83.1%), OpenCart (91.3%) and PrestaShop (97.2%). These are the core applications users are leveraging to perform online commerce transactions. This is especially concerning, because unlike WordPress, these platforms are still experiencing critical vulnerabilities in its core. Coincidently, these are also the platforms that have security obligations set forth by the Payment Card Industry (PCI) Data Security Standards (DSS), one if which includes keeping software up-to-date (requirement 6).
PCI Requirement 6.2 Ensure that all system components and software
are protected from known vulnerabilities by installing applicable
vendor supplied security patches. Install critical security patches
within one month of release. - 2018 Payment Card Industry (PCI) Data
Security Standard, v3.2.1
Another theme you’ll find with this cohort is that they are also the platforms whom struggle with backwards compatibility. This speaks directly to the complexities associated with these platforms to upgrade, which when coupled with human behavior, is a recipe for disaster.
Common Issues & Threats
While the report does show an increase of WordPress sites year over year, it’s not indicative of the platform being more or less secure. The leading contributions to websites hacks, holistically speaking, can be boiled into two key categories:
- Credential Stuffing (Brute Force Attacks)
- Exploitation of Vulnerabilities in Third Party Ecosystems
I won’t spend much time talk to credential stuffing, the act of stuffing access control access points with different username / password combinations; instead I want to focus our discussion on the third party ecosystems.
The accompanying webinar did peal the layers back on the threats posed by the third-party ecosystem (e.g., plugins, modules).

Of the 116 WordPress vulnerabilities Sucuri identified, 20 were categorized as severe (17%), and another 28 in Joomla! (50%). Of the 196 total vulnerabilities, 35 had an installation base over 1 million users. 2019 has seen a spike in the number of vulnerabilities hitting the market; to date, WordPress severe vulnerabilities are 50% of the total identified in 2018.
The one platform you don’t see in this analysis is Magento. For that, I would leverage insights from Willem’s Lab. His insights on the platform and its ecosystem are spot on; unlike WordPress, Magento has predominantly been plagued with issues from core vulnerabilities (e.g., ShopLift crica 2015), but the end of 2018 and beginning of 2019 is seeing a shift in which the platform’s third-party ecosystem is becoming the attack vector of choice.
Note: If you’re a Magento operator, I encourage you to leverage the new central repository of insecure modules released by a group of Magento professionals. A similar repository exists for WordPress.
BLACKLIST ANALYSIS
The report highlights the distribution of blacklisted and non-blacklisted sites at the point of infection. This illustrates a) the different indicators of compromise and b) the effectiveness and reach of blacklist authorities.
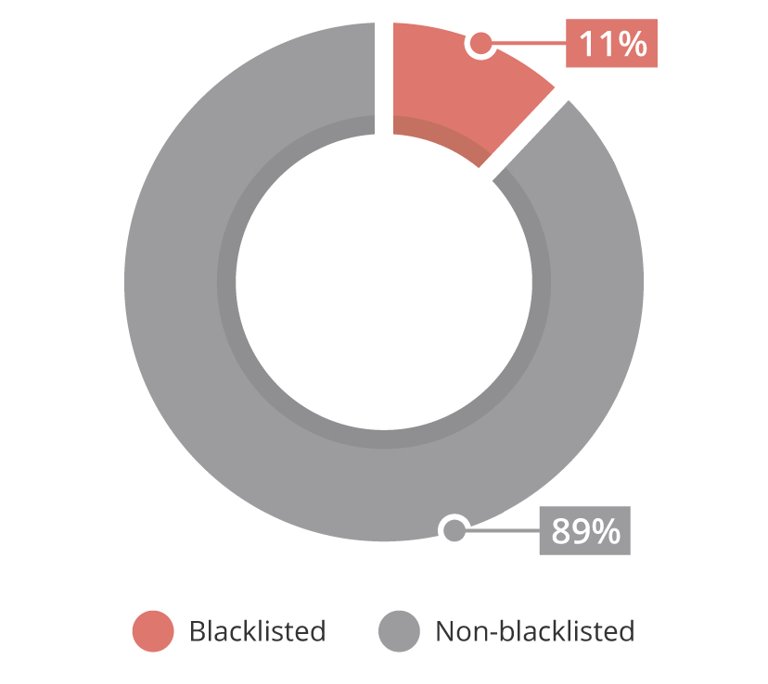
This year we saw a 6% drop (17% -> 11%) in the blacklist state of the sites worked on. It’s difficult to say exactly why this is, but it’s likely related to how these blacklists operate. It does highlight the need to have a comprehensive monitoring solution set as part of your security controls, depending solely on authorities like Google, Norton, and McAfee is not enough.
This becomes even more evident when you look at the detection effectiveness across the different authorities.
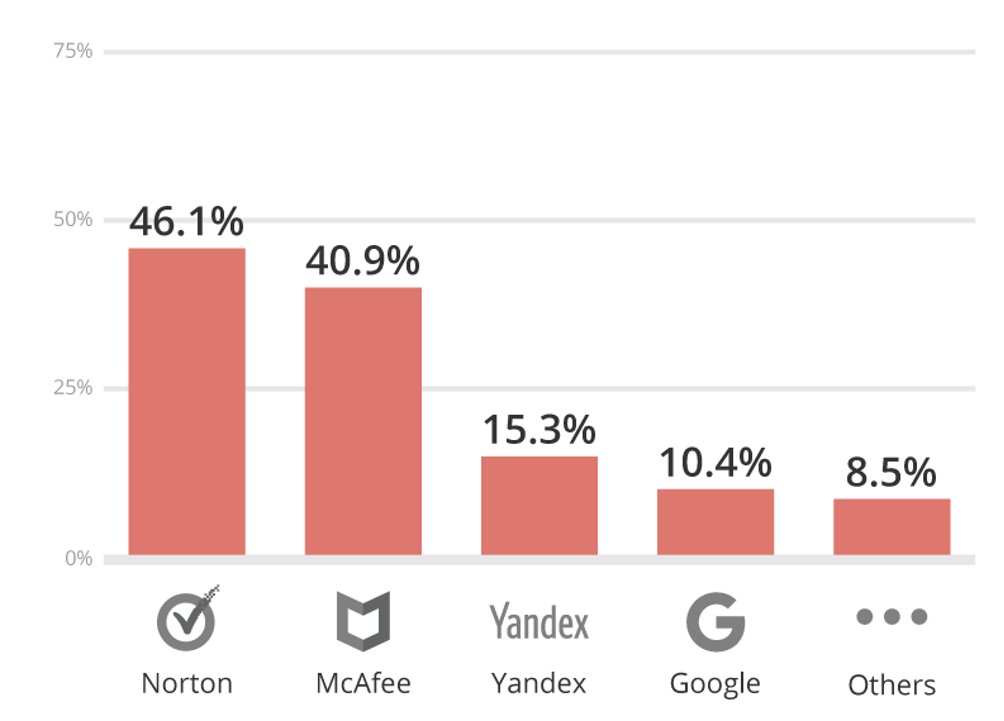
This year we saw Google drop from 12.9% to 10.4%, and we also saw Yandex join the the top 4 (previously it was not material enough to rank). We also saw McAfee drop about 4% and Norton continue to lead the detection rate at 46.1%.
Not all blacklist authorities are the same.
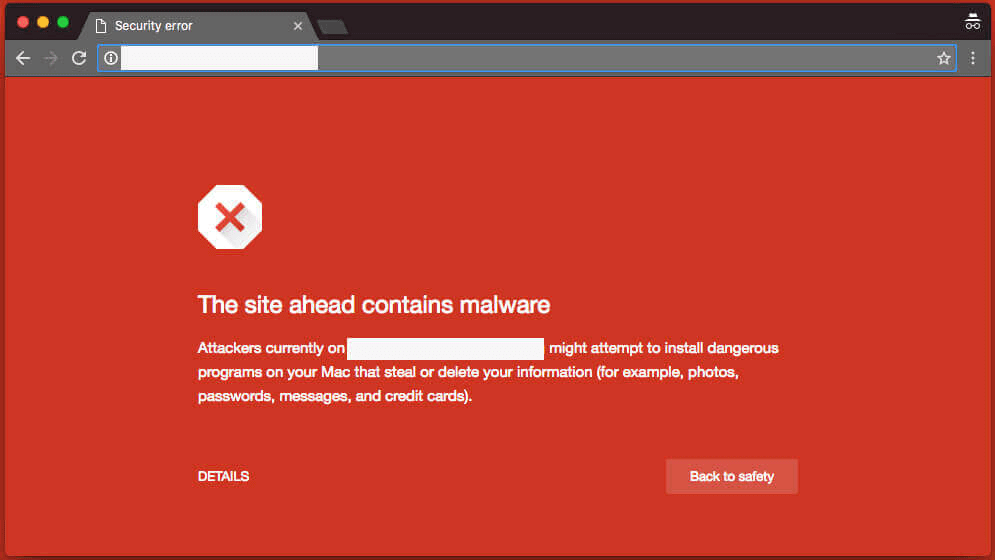
Google is the most prominent because it’s the one that most browsers leverage, most commonly Chrome. The Sucuri team put together a great guide to understand the different Google warnings. When it detects an issue it presents the users with a red splash page – stopping a visitor dead in their tracks.
Other entities however are effective for a different reason; for instance, when Norton and McAfee flag you this implies anyone using their desktop AV client will be prevented from visiting the site or at least notified of an issue. These entities also share their API’s with a number of different services and products, great example is the use of McAfee in Facebook to parse malicious domains.
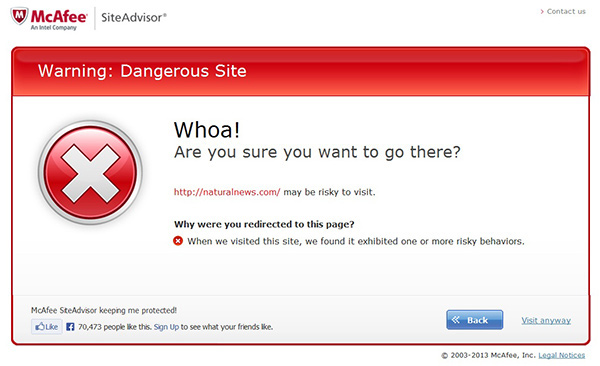
Being blacklisted by one doesn’t necessarily mean the other will, and being removed from one doesn’t mean others will respect this state change. This introduces a lot of stress and frustration with website owners. The best approach managing this is to register with as many of them as possible so that you can maintain direct relationship with each:
- McAfee Site Advisor: http://trustedsource.org/
- Norton SafeWeb: https://safeweb.norton.com/tags/show?tag=WebMaster
- Yandex Webmaster: https://webmaster.yandex.com/
- Google Webmaster: https://www.google.com/webmasters/#?modal_active=none
- Bing Webmaster: https://www.bing.com/toolbox/webmaster
MALWARE FAMILIES
This section shows you what attackers are doing once they have access to your environment. It helps shed light on “intent”.
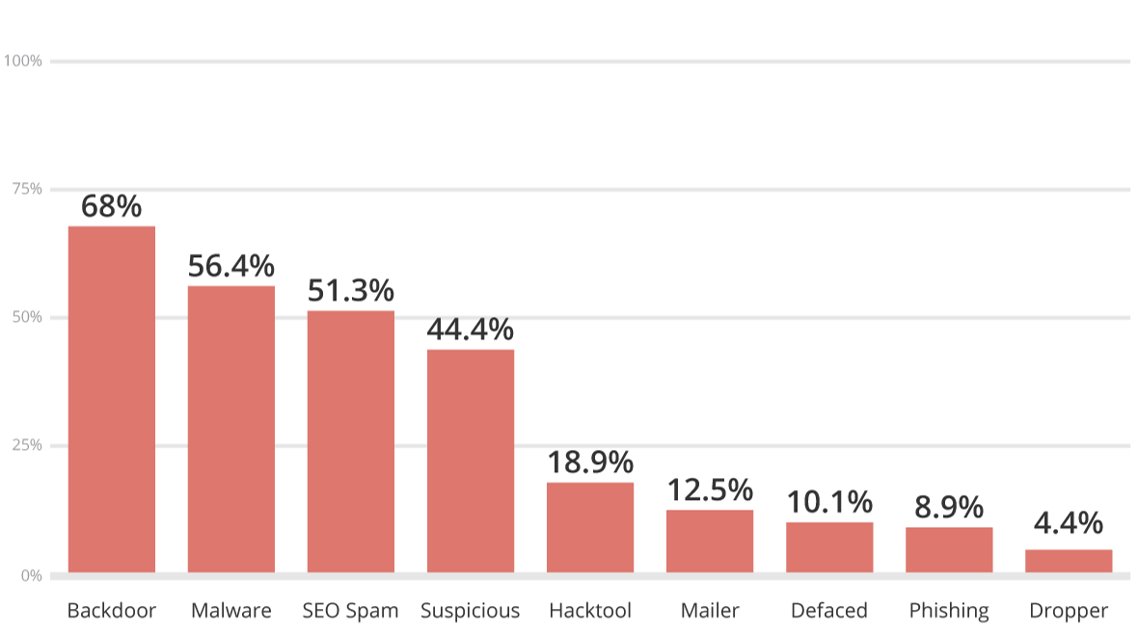
It is very common to have sites with more than one payload, which is why the report represents sites with multiple malware families. Backdoors are a great example of the type of thing you can expect to find in any compromise.
Backdoors are payloads that are designed to give attackers continued access to an environment, bypassing existing access controls. They were found in 68% (modest 2% drop from 2017) of the infected sites analyzed. Backdoors will be one of the first things an attacker will deploy to ensure that even if their actions are found, they can retain access and continue to use the site for nefarious actions. It is one of the leading causes of reinfections, and the most commonly missed payload.
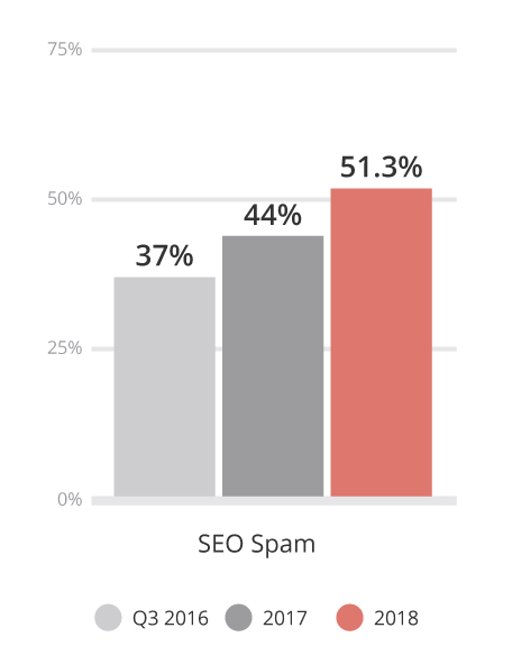
Last year I called out the continued rise of SEO Spam, this year was no different.
This is the result of a Search Engine Poisoning (SEP) attack in which an attacker attempts to abuse the ranking of your site for something they are interested in. Years ago this would be almost synonymous with the Pharma Hack, but these days you see attackers leveraging this in a number of other industries (e.g., Fashion, Loans, etc..). You can expect this in any industry where impression based affiliate marketing is at play.
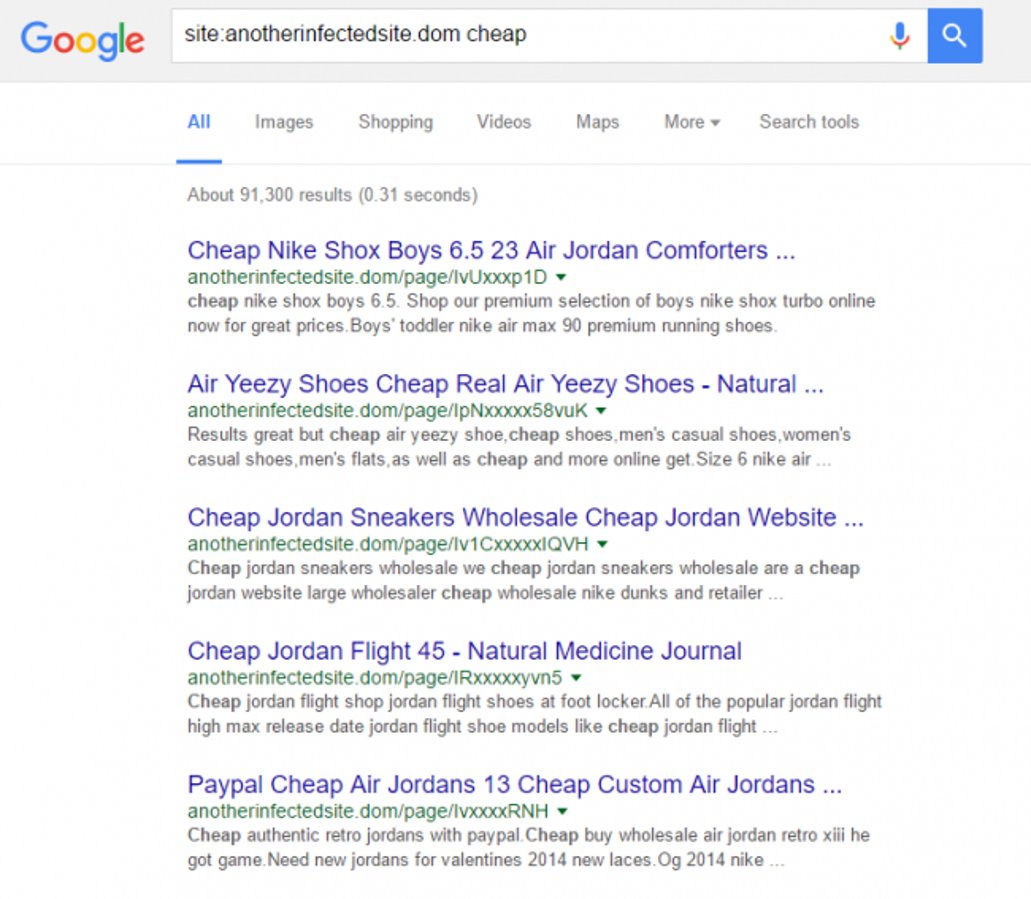
The teams analysis highlighted an impressive increase (78%) in the number of files being cleaned in every case. This shows the pervasiveness you should expect after every compromise.
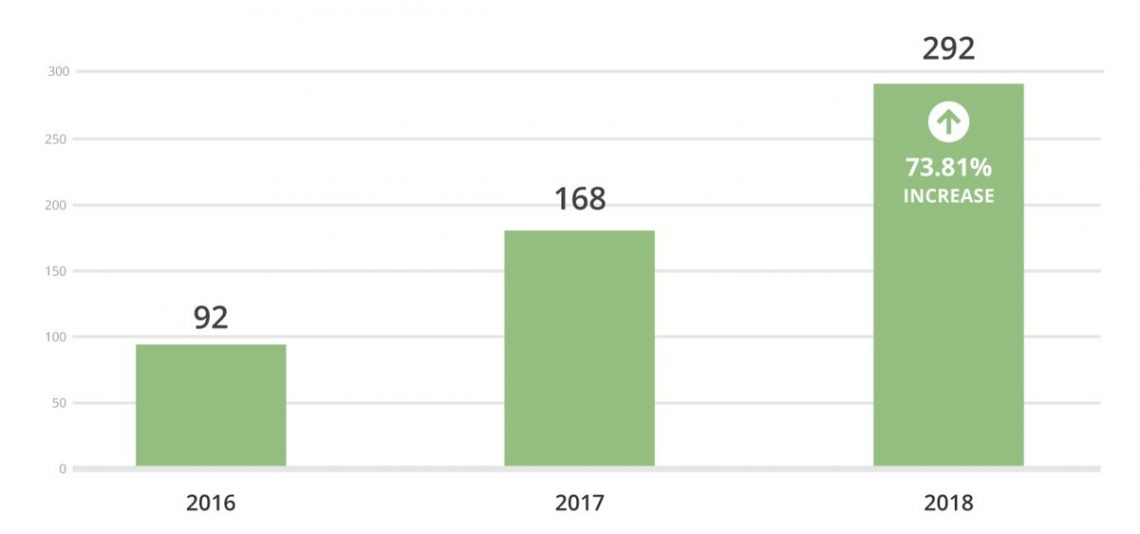
It’s not enough to clean the file you see, but instead perform a deep scan across files and databases to ensure everything has been removed.
Of the files affected, there were some trends in the file types targeted. The Top 3 modified files were the index.php (34.5%), functions (13.5%), and wp-config.php (10.6%) file.
Every file saw an increase over 2017, and there was a change in the top three – .htaccess dropped to make remove for wp-config.
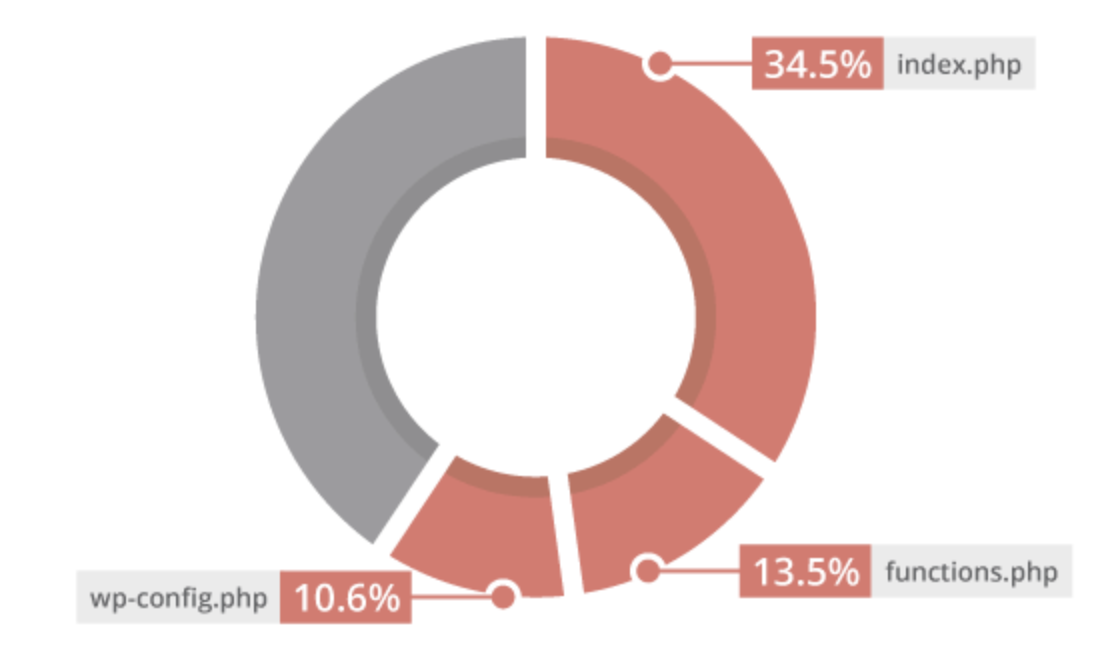
The report outlines how each of the files are being leveraged, specifically for what malware families. These three files are not a surprise, they are popular because they load on every site request, belong to core files, and are often ignored by integrity monitoring systems.
Great details by Fio Cavallari & Denis “Unmaskparasites” Sinegubko on what attackers are using these files for.
Index.php
- Approximately 34.5% of sites had their index.php files modified after a compromise.
- The index.php file is modified by attackers for a variety of reasons including malware distribution, server scripts, phishing attacks, blackhat SEO, conditional redirects, and defacements.
- 24% of index.php files were associated with PHP malware responsible for hiding a file inclusion.
- This malware calls to PHP functions like include and include_once by replacing the file path characters with corresponding Hexadecimal and mixed up alphabetic characters.
- 15.8% of index.php files were affected by malicious PHP scripts disguised using absolute paths and obfuscated characters and hidden within seemingly innocent files.
- Instead of injecting full malware code into a file, this method makes the malware more difficult to detect by using PHP includes and obfuscation.
Functions.php
- 13.5% of compromised sites had modified functions.php files, which are often used by attackers to deploy SEO spam and other malicious payloads, including backdoors and injections.
- Over 38% of functions.php files were associated with SEO spam injectors:
- Malware that loads random content from a third-party URL and injects it on the affected site.
- Able to update configurations through a remote command.
- Doesn’t explicitly act as a backdoor but can use the function to load any kind of code – including a backdoor.Usually found on nulled or pirated themes and plugins.
- 8.3% of functions.php files impacted by generic malware.
- 7.3% of files associated with PHP.Anuna, which injects malicious code into PHP files.
- Malicious payloads vary from spam injection, backdoors, creation of rogue admin users, and a variety of other objectionable activities.
WP-Config.php
- wp-config.php was the third most commonly modified file (10.6%).
- Contains sensitive information about the database, including name, host, username, and password. It is also used to define advanced settings, security keys, and dev options.
- 11.3% of wp-config.php files were associated with PHP malware responsible for hiding a file inclusion, also commonly seen with index.php.
CryptoMining and Ransomware
As we talk about what attackers are doing post-compromise, it’s worth spending a few minutes on Cryptomining and Ransomware.
In 2017, we saw the rise of Ransomware across the entire InfoSec ecosystem. It’s impacts on websites, however, were marginalized because of its ineffectiveness; mitigating a ransomware attack on a website is relatively straight forward, have a backup.
Cryptomining, however, is a bit of a different story.
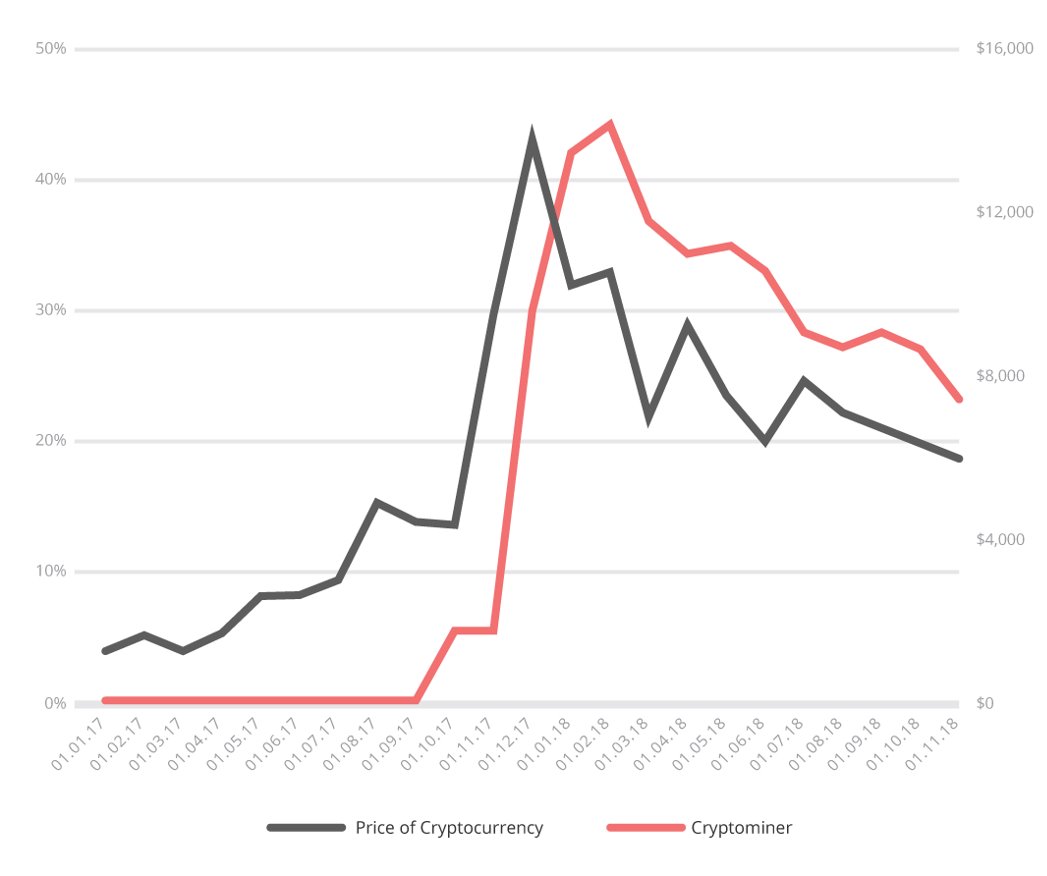
Cryptomining, the act of verifying and adding different forms of cryptocurrency transactions to the blockchain ledger. This process is the necessary step to adding to the ledger, and under this model the spoils belong to the group that processes the request the fastest. To achieve this you need processing power, this is where sites and their associated hosts come into play.
Although we saw a decrease in cryptomining activity in 2018, it’s an interesting payload to pay special attention to.
What you see in CheckPoints report is the correlation between the “value” of a coin, and cryptomining activity. In other words, as the price of cryptocurrency increases (think back to the 1: $19k) so did the cryptomining activity.
Analyzing this behavior (Thanks Thiago), you also find the following actions:
- 67% of all Cryptomining signatures were related to client-side infections with JavaScript based miners like CoinHive.
- This means these payloads are abusing your browsers processing on your users local machines (ever go to a site and your browser dies? or it starts chewing up a lot of local resources?)
- Remaining 33% of Cryptominers were server-side and used PHP to mine digital currencies.
- This means these payloads are abusing your host server, the server housing your website. This can lead to your hosting provider shutting down your site or you might experience degraded performance on your site.
I am particularly fond of this payload because it’s a great example of what we can expect form attackers when incentives are aligned. While I don’t really expect to see much activity with website ransomware, I do expect to see more with cryptomining when the incentive increases (e.g., value of cryptocurrency increases again).
I encourage you to read through Sucuri’s Hacked Website Report for 2018. It’s perfect for a website owners to understand the threats they face as they get their ideas online.
If you’re an online consumer and wondering how you can protect yourself from falling victim to hacked websites, then I encourage you to spend some time learning more about how DNS resolvers, like CleanBrowsing, can help keep infected websites from reaching your devices.
Watch Sucuri’s webinar, with yours truly, below:
