Over 55% of security executives report that they have experienced a SaaS security incident in the past two years — ranging from data leaks and data breaches to SaaS ransomware and malicious apps (as seen in figures 1 and 2).
 |
| Figure 1. How many organizations have experienced a SaaS security incident within the past two years |
The SaaS Security Survey Report: Plans and Priorities for 2024, developed by CSA in conjunction with Adaptive Shield, dives into these SaaS security incidents and more. This report shares the perspective of over 1,000 CISOs and other security professionals and shines a light on SaaS risks, existing threats, and the way organizations are preparing for 2024.
Click here to download the full report.
SaaS Security Incidents Are on the Rise
Anecdotally, it was clear that SaaS security incidents increased over the last year. More headlines and stories covered SaaS breaches and data leaks than ever before. However, this report provides a stunning context to those headlines.
As seen in figure 1, an astounding 55% of organizations had a SaaS incident within the past 24 months. These incidents included data leaks (58%), malicious third-party applications (47%), data breaches (41%), and SaaS ransomware (40%), as seen in figure 2.
 |
| Figure 2. The types of security incidents organizations have experienced |
Current SaaS Strategies Aren't Going Far Enough
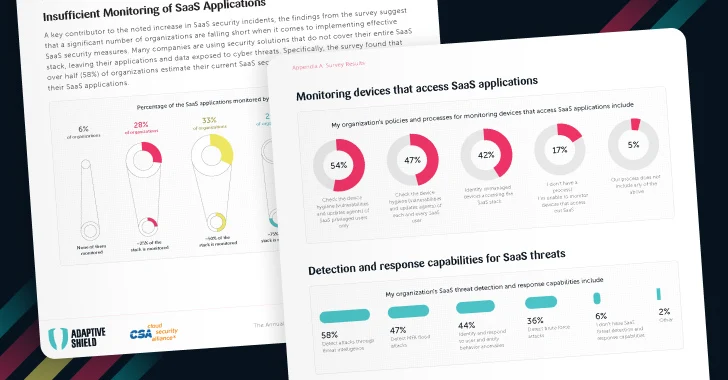
One reason for the increase in security incidents is that current solutions aren't being deployed broadly enough. 7% of respondents claimed to have 100% of their SaaS stack monitored with 68% reporting that they were monitoring less than half their SaaS stack.
The current SaaS security practices, like Cloud Access Security Brokers (CASB) and manual audits, are not enough to cover the SaaS stack. Unfortunately, these solutions are unable to meet the growing use and demands of the modern SaaS stack. Companies today have to secure hundreds of thousands of configurations and oversee thousands of user accounts while vetting thousands of third-party connected applications, which are beyond the capabilities of CASBs and overwhelm the resources of any manual effort.
 |
| Figure 3. Percentage of the SaaS apps being fully covered and monitored by CASB or manual audits |
App Ownership is Widespread
In response to increasing SaaS incidents, organizations report that they are now prioritizing SaaS Security. The survey shows that more executive-level leaders are involved in securing their SaaS stack and CISOs and security managers are seemingly transitioning from the role of controllers to that of governors in securing the SaaS stack.
There are layers of responsibility involved in securing each app as oftentimes the ownership of the app sits in different business departments throughout the organization, while it's the security team that is the one ultimately responsible.
 |
| Figure 4: More roles involved in SaaS security make it difficult to know who is responsible |
SaaS Security Plans for 2024
The report also shines a light on how organizations are creating policies and processes to deal with key SaaS security issues. While many have a way to go, they are building a strong foundation for these domains:
- SaaS misconfigurations
- Third-party connected apps
- User devices that are accessing SaaS apps
- Identity and access governance
- Threat detection
- Data loss management
Companies Are Increasing Investment in SaaS and SaaS Security
In addition to enhancing their policies and adding executive stakeholders, it's not surprising that organizations have increased their SaaS spending as well. Over the last year, 71% of organizations have increased their investment in SaaS security tools, while 63% have either hired more personnel or increased training for SaaS security.
 |
| (Left) Figure 5. Organization's change in investments over the past year | (Right) Figure 6. How many organizations are currently using or plan to use an SSPM platform |
One key area of investment has been SaaS security. A year ago, in the 2022 State of SaaS Security Report, 17% of respondents report having a SaaS Security Posture Management (SSPM) tool in place. That number has nearly tripled since, growing to 44%, with an additional 36% intending to add an SSPM to their SaaS security stack within the next 18 months. This brings the total of security executives already using SSPMs or planning to bring them on to 80%.
Among the reasons for this sudden increase is the reported need to mitigate SaaS threats (31%), improve their company's SaaS posture (29%), and save time in the management and maintenance of their SaaS stack (23%).
 |
| Figure 7. Top expected benefits from an SSPM solution |
A Picture of Challenges and Hope
Ultimately, the SaaS Security Survey Report: 2024 Plans and Priorities report reflects and quantifies many of the changes affecting this industry over the past year. Threat actors are tempted by the seemingly low-hanging, high-value fruit within the SaaS ecosystem. SaaS security cybersecurity incidents are up by 12% over one year ago, and the types of attacks — breaches, data loss, and ransomware — are significant.
However, organizations are rising to the challenge of defending their SaaS stack. Whether they were initially drawn to SaaS applications for the cost savings, ease of access, or collaborative nature of the tool, they now recognize the need to secure their assets and the data contained within.
It's not surprising that they have turned to the SSPM market. By helping organizations identify and secure misconfigurations, protect themselves from intrusive third-party app scopes, manage users and devices, and detect threats from across the SaaS stack, SSPMs offer hope that the sensitive and business-critical data stored within the SaaS stack can be tightly secured.
Learn how an SSPM can help you secure your entire SaaS stack.