Tens of thousands of applications that are critical to the operations of data centers around the globe are exposed to the internet, with many secured with default factory passwords, posing a significant cyber risk to enterprises worldwide.
Researchers with cybersecurity firm Cyble this week said that along with the public-facing data center infrastructure management (DCIM) software, they also found intelligent monitoring devices, thermal cooling management and power monitors for racks vulnerable to cyberattacks.
The discovery of the more than 20,000 DCIM software instances and products exposed to the internet makes it highly likely that there will be “increasing cyber threats towards data centers worldwide,” investigators with Cyble Research Labs wrote in a blog post.
“Globally data centers are becoming faster, smarter, and highly scalable but this development comes at a price, as with great power comes significant responsibilities and greater risks of cyberattacks,” they wrote. “As data centers work with the collaboration of multiple technologies and software, vulnerabilities and loopholes can be easily found by malicious hackers. Moreover, data centers are rapidly upgrading. Hence hackers are exploring new vectors to bypass the security parameters.”
See also: Top Vulnerability Management Tools
Growing Presence of DCIM Software
DCIM is becoming an increasingly important part of data center management. The software tools address both IT and facilities operations, managing and controlling such data center components as servers, storage, routers and switches, along with heating, ventilation and cooling (HVAC) systems, uninterruptible power supply (UPS) systems, sensors, transfer switches – used to redirect a power load to an alternate source – and server rack monitoring solutions.
According to market research firm KVB Research, the global DCIM market is expected to grow an average of 21.7 percent a year through 2026, when it will hit $4.4 billion. The analysts wrote that the rising demand for data center virtualization, the ongoing migration of business into private clouds and the drive to improve cost efficiencies within the data center are helping to fuel the market growth.
Because of the reach DCIM software has in data centers, it is getting the attention of threat actors, according to the Cyble researchers. For example, hacktivists could launch an attack on a specific data center’s HVAC system in retaliation for some actions by a person or group connected to the facility. Ransomware gangs could block IT and facilities managers from DCIM applications and demand money to regain access, and hackers could get access to highly sensitive data.
State-sponsored groups could disrupt power to critical data center components and cause a shutdown of the site, they wrote.
“Data centers are the most important critical infrastructure for the nation and the organization using the data center facilities,” the researchers wrote. “A successful attack on this vital sector can lead to the loss of a considerable amount of money. The data stored and processed in the data centers can be corrupted and destroyed, which can cause a severe impact on the organization’s brand reputation. Hackers can even delete the traces of their attack by deleting the logs from … web consoles.”
Also read: Critical Infrastructure Protection: Physical and Cyber Security Both Matter
Public-Facing Software a Threat
Data centers also use many products from various vendors, which increases the scope of attack for cybercriminals. Security professionals told eSecurity Planet that allowing these applications to be exposed to the internet is a dangerous move by data center operators and vendors alike.
“There can be no real security if physical security of a system is compromised,” said John Bambenek, principal threat hunter for cybersecurity company Netenrich. “These systems provide attackers a good deal of insight into the physical layer of data center operations and, in some cases, allow them to make changes that can compromise the underlying systems. It’s been a best practice not to put things on the Internet, accessible to the world and protected by default credentials since the ’90s. This is laziness at its worst.”
‘Exposing that to the public internet is like allowing terrorists to direct air traffic control’
Sounil Yu, CISO for cybersecurity vendor JupiterOne, said that “It’s easy to lose sight of these applications without a good asset management program. It’s worse with DCIM tools, since they are part of one’s control plane. Exposing that to the public internet is like allowing terrorists to direct air traffic control.”
See also: Top IT Asset Management Tools for Security
APC by Schneider, Sunbird, Liebert on List
Cyble’s researchers said they detected instances of software from Sunbird, Liebert, APC by Schneider, Vertiv and Device42 that could be accessed by threat actors on the outside. APC by Schneider accounted for more than half the public-facing instances found by the researchers.
They also found instances of public-facing software from Device42, Liebert’s CRV-iCOM cooling solution and smart UPS still running factory default passwords. They were “able to find several instances exposed over the internet while investigating the scope of attacks on data centers all over the globe. Default passwords protected these data centers. Some of the products found were outdated, allowing hackers or malicious groups to exploit the data center’s systems further.”
In addition to building and room security, monitoring server racks are critical as data storage, and processing equipment are installed in racks, the researchers noted. “A change in external parameters could cause severe damage,” they said. “For example, an increase in temperature might cause the chips inside to melt and bring the entire system to a halt. Furthermore, the chips’ processing power slows down and loses efficiency if they run too cold.”
They found multiple exposed web interfaces used for rack monitoring, with the interfaces using default passwords, “making it easy for a hacker to gain insights into a data center. As there are multiple sensors, power units, networking devices, CCTV cameras connected to these portals, there is a lot of scope for a hacker to gain sensitive information about the components within the data center and their working.”
Reconsider Web Exposure
The Cyble researchers noted that even organizations that are already spending millions of dollars to protect their data centers and ensure there are no downtimes or security breaches need to take a holistic view of their facilities and look for openings that threat actors could exploit.
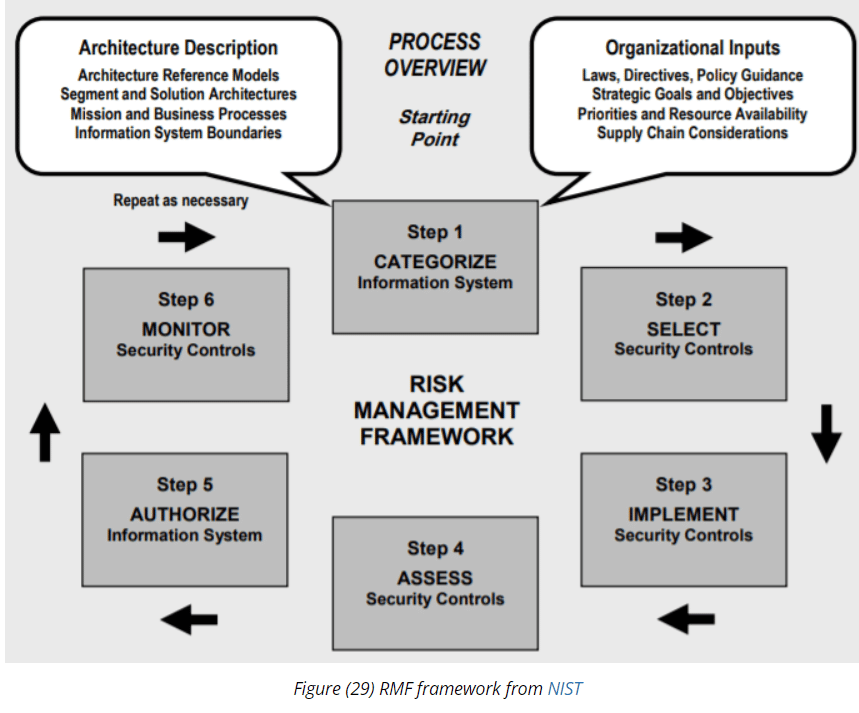
Enterprises need to adopt a risk management framework, such as the RMF framework from NIST, as well as embrace security awareness programs, path vulnerabilities, implement access controls on connected systems, launch network segmentation efforts and run regular audits. The researchers also urged strong password policies, vulnerability assessment programs and using threat intelligence.
And reconsider using applications and instances exposed to the internet.
“Public-facing web instances are a significant threat for the critical sectors which go unaddressed by the security teams,” they wrote. “Doing so puts the complete environment at risk of cyber-attack. Checking assets exposure is very important in these sectors.”
Read next: How to Use MITRE ATT&CK to Understand Attacker Behavior








