
As the number of malware and ransomware attacks continue to become more prevalent, cybersecurity has become a focal point for many industries and individuals. Google’s email client is one that has been compromised by some of the malicious parties out there. It was recently found by cloud email security company Avanan that phishers have been exploiting Gmail’s SMTP relay service since at least April.
By taking advantage of the SMTP relay service, spoofers are able to work around users’ spam folders by allowing phishing emails to impersonate legitimate companies, thus making malicious emails seem authentic even though an attempted hack is taking place. Gmail allows some Google plans to send up to 4.6 million emails in a 24-hour period, allowing malicious parties to have extremely wide attack vectors when sending out phishing attempts.
“Cybercriminals and social engineers continue to utilize various techniques to mask their email addresses and pretend to be someone else. Their expectancy is that the user is unaware to check that the email is coming from the disguised email address, like a vendor, colleague or someone from upper management,” said James McQuiggan, security awareness advocate at KnowBe4. “By checking the email address and confirming the user to determine if the email is authenticated or not, users blindly accept the name in the ‘From’ field and should take the necessary steps to protect their email account and the organization.”
SEE: Password breach: Why pop culture and passwords don’t mix (free PDF) (TechRepublic)
Making phishing attacks seem genuine
Hackers are able to take advantage of this email exploit by DMARC=reject not being set up properly, according to Avanan. DMARC is a standard email authentication method that assists a company’s IT administrators in preventing attackers from spoofing an organization’s server and domain. With the ‘DMARC=reject’ command not properly implemented, phishers can make it appear as though emails are coming from real sources.
“Threat actors are always looking for the next available attack vector and reliably find creative ways to bypass security controls like spam filtering,” said Chris Clements, vice president of solutions architecture at Cerberus Sentinel. “There has been a recent uptick in attackers leveraging ‘trusted’ sources to increase the odds that are often allow-listed by their targets. As the research states, this attack utilized the Google SMTP relay service, but similar attacks come from compromising an initial victim’s email systems and then using that to send further attacks to secondary targets.”
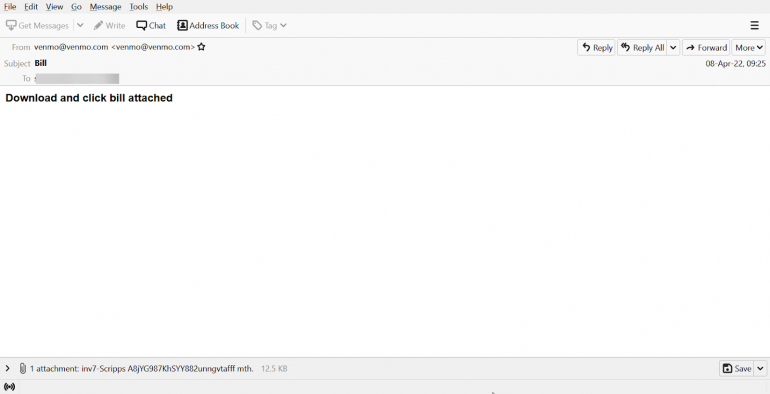
The method hackers are employing to do this is by using smtp-relay.gmail.com as the SMTP service. Once this is in place, phishing attacks can happen by seemingly real sources, like Venmo in the example above. Because this email is seemingly from a legitimate company and domain, it will bypass Gmail’s spam filter and end up in users’ inboxes as appearing to be from a valid site.
How to prevent these phishing attacks
From the organization’s perspective, successful implementation of setting DMARC to reject can prevent malicious sources from using company servers to send out phishing emails. Most well protected companies already have this in place, but on the heels of this exploit, all enterprises should seek to patch over the potential to capitalize on email manipulation.
“Organizations should implement verification of domains by using DMARC configuration in the mail server, allowing the organization to request the domain to be checked for validation before allowing the email into the inbox,” McQuiggan said. “The Sender Policy Framework configuration in the mail server authenticates the sender’s email address. Finally, using encryption of the headers prevents man-in-the-middle attacks with the DKIM or Domain Key Identified Mail. While the DMARC is slowly rising, organizations can quickly implement this configuration within fifteen minutes and reduce their risk of a spoofing email attack by a doppelganger domain.”
From the end-users point of view, employing best practices is always advised. The three points below outlined by Avanan are advised to help prevent attacks such as these:
- Check sender address before interacting with any email
- Always hover over any link to see the destination URL before clicking on it
- Ensure your email authentication standards are up to par
By following these tips, users can prevent themselves from being the victim of the next big cyberattack through protection of their sensitive data and saving the individual headaches in the process.
Master all things cybersecurity with these resources from TechRepublic Academy:
