Contents:
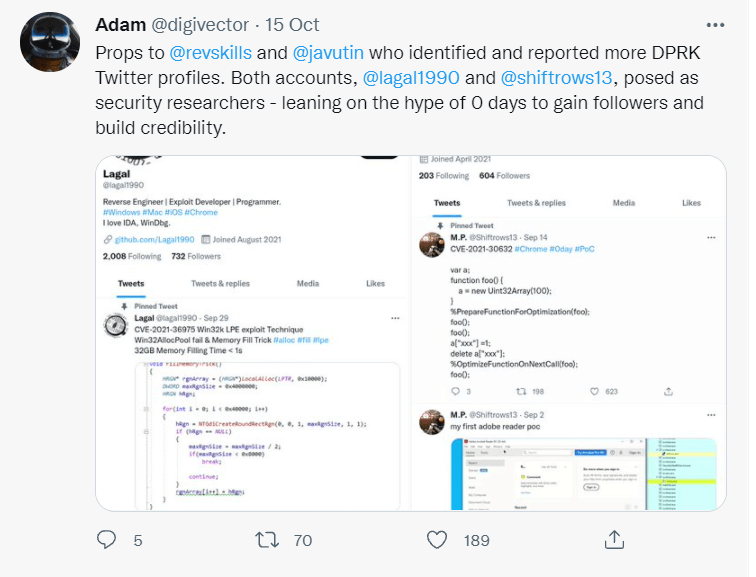
Two malicious accounts used by threat actors in a seemingly North Korean cyber-espionage campaign were suspended by Twitter. The accounts under discussion are @lagal1990 and @shiftrows13 working as bait for security researchers with the final goal to make them download malware.
The ones who initially discovered this campaign that is still developing were the TAG experts (Google Threat Analysis Group) back in January.
Detailing the Campaign That Used Malicious Accounts
Adam Weidermann, a Google TAG analyst, shared details on the campaign when the January analysis was published. According to his report, the hackers built up a research blog and the Twitter accounts represented basically their method to spread different links, like, for instance, links directing to their blog posts.
The actors behind this campaign, which we attribute to a government-backed entity based in North Korea, have employed a number of means to target researchers which we will outline below. In order to build credibility and connect with security researchers, the actors established a research blog and multiple Twitter profiles to interact with potential targets. They’ve used these Twitter profiles for posting links to their blog, posting videos of their claimed exploits and for amplifying and retweeting posts from other accounts that they control.
The campaign focused on security researchers and the lures used to trick them were none other than research and bugs. In order to build a sense of credibility, as the same researcher explains, the Twitter accounts impersonated security researchers. Threat actors also used the concept of collaboration as a social engineering tactic in this malicious campaign.
After establishing initial communications, the actors would ask the targeted researcher if they wanted to collaborate on vulnerability research together, and then provide the researcher with a Visual Studio Project. Within the Visual Studio Project would be source code for exploiting the vulnerability, as well as an additional DLL that would be executed through Visual Studio Build Events. The DLL is custom malware that would immediately begin communicating with actor-controlled [command-and-control, or C2] domains.
The Ones Behind the Malicious Accounts Used Zero-Days
According to ThreatPost, the systems the targeted security researchers used were updated, so being completely patched, meaning that zero-days were used to make the attack successful.
Following the January discovery of the campaign by the TAG experts, an Internet Explorer zero-day that threat actors were exploiting was identified by other experts from South Korea. This was depicted as a double-free bug placed in the DOM object, more specifically in its part associated with the attribute value release. The bug would only eventually let hackers execute malicious code and steal data.
The Threat Actors Built Also a New Site
According to the same researchers at Google TAG, on the 17th of March, there was identified that cybercriminals created a new website that was also related to different profiles on social media. The website was associated with a so-called enterprise “SecuriElite”. What this company did was to offer exploits, assessments related to software security, and pen tests.
Like previous websites we’ve seen set up by this actor, this website has a link to their PGP public key at the bottom of the page. In January, targeted researchers reported that the PGP key hosted on the attacker’s blog acted as the lure to visit the site where a browser exploit was waiting to be triggered.
It’s worth mentioning that the security research community was targeted by cybercriminals in this malicious campaign not only via Twitter but also via LinkedIn, Keybase, Discord, or Telegram.
Besides, it’s not the first time Twitter takes action against DPRK accounts, as in the month of August the platform suspended another one that was linked to the same malicious campaign.
Did you enjoy this article? Follow us on LinkedIn, Twitter, Facebook, Youtube, or Instagram to keep up to date with everything we post!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










