Contents:
The Women Political Leaders (WPL) Summit in Brussels, dedicated to the topics of gender equality and female leadership, became the target of a cyber-espionage campaign orchestrated by ‘Void Rabisu’. This group developed a replica of the official WPL site, leading attendees and those interested in the event to their deceptive platform.
The bogus website was ‘wplsummit[.]com’, and mirrored the official WPL site hosted at ‘wplsummit.org’.

Fake WPL summit website (Source)
Inside the Deceptive Tactics
Upon visiting the fake site, users were presented with a button labeled ‘Videos & photos’. This button seemingly offered genuine event images but sneakily included a malware downloader dubbed ‘Unpublished Pictures’.
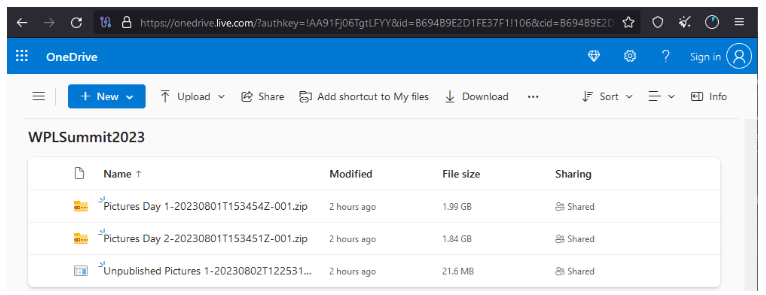
One Drive Files WPL Malware (Source)
This malware, once triggered, fetched an encrypted file from an external source. When decrypted, it turned into a DLL crafted to facilitate covert communication with the threat actor’s remote server.
The Evolution of RomCom 4.0
Cybersecurity researchers classified this new malware as RomCom 4.0, a more sophisticated successor to the previous RomCom 3.0 version.
This iteration operates with heightened stealth, exclusively functioning in-memory and reducing its command set to only ten, a sharp decline from the 42 seen in its predecessor.
- No action – Handling function returns zero; malware waits for the next command.
- Run command – Executes a command and sends back its output.
- Upload file – Uploads a file to the compromised machine.
- Download file – Retrieves a file from the infected machine.
- Run command – Executes a given command.
- Update interval – Modifies backdoor check frequency (default 60 seconds) and updates the system registry.
- Get system info – Retrieves RAM, processor, local time, and username.
- Update network component – Updates data for the network component in the Windows registry.
- Uninstall – Purges relevant registry keys and deletes associated files.
- Get service name from the Windows registry.
A standout characteristic of this malware variant is its stringent use of the Transport Layer Security (TLS) 1.2 version, aiming to reinforce its communication security. Read the complete analysis here.
A Cloudy Forecast
While Void Rabisu’s exact motives and strategies remain unknwon, what’s clear is their shift towards advanced cyber espionage, explains Bleeping Computer. Researchers predict a high likelihood that this group will set its sights on major conferences tied to specific interest groups in upcoming times. As such, attendees and internet users at large need to remain vigilent.
Recommendations for Safe Browsing
Here are a few steps users and organizations can take to improve their defense against malicious domains:
- Inspect URLs Carefully. Hover over links to see the actual URL, and be vigilant of any misspellings or suspicious domain names.
- Prioritize Secure Connections. Ensure sites have HTTPS and an SSL certificate, typically symbolized by a padlock in the address bar.
- Employ DNS Filters. Use a DNS filtering solution that block known malicious domains.
- Stay Updated. Regularly update browsers, firewalls, and security software to fend off new threats.
If you need a solution to protect your IT infrastructure from sophisticated cyber threats, Heimdal has you covered from endpoints and networks to emails and identities and beyond.

Heimdal® DNS Security Solution
- Machine learning powered scans for all incoming online traffic;
- Stops data breaches before sensitive info can be exposed to the outside;
- Advanced DNS, HTTP and HTTPS filtering for all your endpoints;
- Protection against data leakage, APTs, ransomware and exploits;
If you liked this piece, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










