Applying Service Accounts Security Best Practices with Silverfort
Managing service accounts can be a daunting task for organizations, as service accounts are scattered across different environments and are used by various business applications, and are typically forgotten about unsupervised. Meaning in most organizations nobody is tracking their use or validating that they are not compromised or used by malicious actors. On top of managing these accounts, organizations often lack full visibility into service accounts and how they’re being used, and are seen as low-hanging fruit for threat actors.
However, service account management is a critical task that should not be overlooked, as service accounts often have privileged access and are used by applications, scripts, and services to authenticate and interact with various systems and resources. If service account management is overlooked, it can lead to malicious actors with access to compromises service accounts carrying out malicious activities such as lateral movement.
In this post, we will explain how Silverfort enables you to manage your service accounts easily, through automated detection, monitoring, and protection. As a result, Silverfort is able to provide full visibility, risk analysis, and adaptive access policies for service accounts without the need for password rotation.
Best Practices for Service Accounts Protection
While service accounts can be associated with an owner and these accounts’ activities should be continuously monitored, they should not have the same privileges as a regular user account. This means that service accounts should not have interactive user interface privileges or the ability to operate as normal users. By implementing Silverfort’s Unified Identity Protection platform, organizations can apply best practices to get their management of service accounts under control.
This involves a three-step approach:
- Discover all service accounts
- Monitor activity and risk analysis
- Analyze and enable access policies
With these capabilities implemented, service account management is no longer a nightmare, and, at the same time, the risk of security breaches caused by mismanaged service accounts is dramatically reduced. Here are more details on Silverfort’s three-step approach:
Discovery
The first step to properly managing and protecting all service accounts is knowing exactly where they reside. Here are several key questions to ask:
- What service accounts do you have?
- What is the total number of service accounts?
- Which assets use those service accounts?
Silverfort’s Service Accounts screen displays the service account name, source, destination, number of authentications, risk score, and account info
This is done when an organization connects its domain controllers to Silverfort. Silverfort is then able to automatically identify all service accounts, providing complete visibility into their behavior patterns. This is because, as machine accounts, service accounts display predictable behavior patterns, allowing Silverfort to identify and categorize them automatically.
Silverfort identifies and categories three main types of service accounts:
• Service accounts – defined on Active Directory (AD) or another user repository
• Hybrid accounts – used by both users and machines
• Scanners – used by a few devices to communicate with a large number of resources inside a network
Silverfort can also quickly identifies any accounts that follow usual service account naming conventions (e.g. “admin” or “svc”), as well as any custom naming conventions that may be used by the organization.
Because Silverfort can detect all machine-like behavioral patterns, it can also flag whether an account is also being used by a human user and alert on this bad practice. Silverfort detects the erratic patterns associated with human user activities that do not correlate with the machine’s behavior patterns and alerts the irregular activity of the service account.
Monitoring & Risk Analysis
The next and continuous phase is monitoring all service account activity and associated risks. Now that there is a complete picture with full visibility into all service account details and behavior, Silverfort constantly monitors and audits their use.
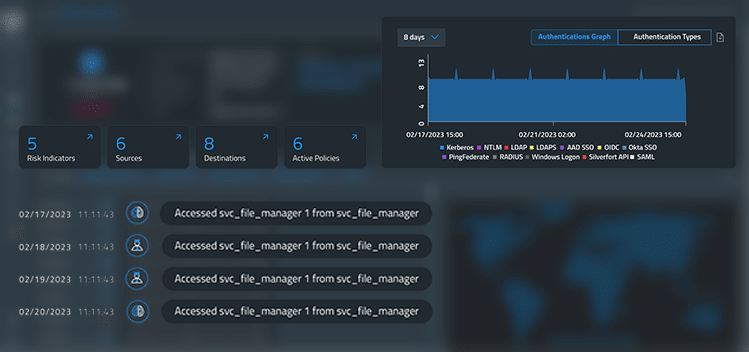
Silverfort’s Investigation screen shows various insights into a specific service account’s activity.
Silverfort can identify different configurations and behaviors of service accounts, such as high-level permissions, broad use, repetitive behavior, etc. Silverfort then adds risk analysis and level of predictability to each service account to enable administrators to better understand the degree to which specific service accounts are at risk.
By continuously monitoring all authentication and access activity, Silverfort can assess the risk of every authentication attempt and thus immediately detect any suspicious behaviors or anomalies, providing SOC teams with actionable insights into overall service account activity.
Analyze & Access Policies
Once full visibility and insight into all service accounts are achieved, the next phase is to analyze these insights and create access policies to provide a digital fence for these non-human accounts.
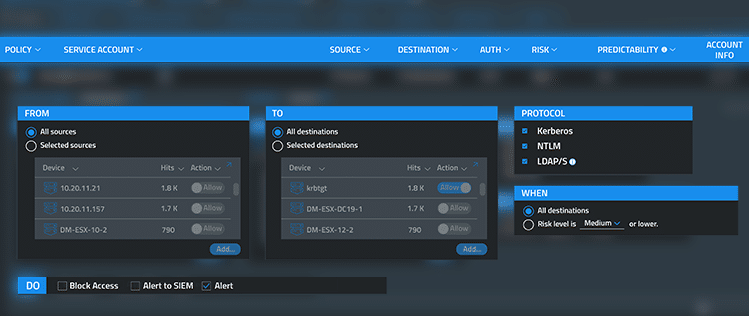
Silverfort displays a list of sources and destinations using the service accounts, as well as the number of hits (authentications)
Silverfort enables admins to analyze their service accounts’ insights to identify certain service account behaviors. Silverfort shows the number of hits per source and destination. This helps admins prioritize the different sources and destinations that their service accounts connect to, ensuring they are properly monitored and protected.
With the help of Silverfort, admins will examine the service account behavior, using one of the following methods:
1. Understand which users are used by the crown jewels applications and analyze these service accounts.
2. Analyze the critical risk level accounts and then go through the chain to the lower risk levels (from the risk levels provided by Silverfort).
3. Analyze and prioritize the service accounts with high privileges and then continue to the accounts that are broadly used and finish with accounts with interactive logins.
After analyzing the service accounts, Silverfort automatically recommends specifically tailored policies for each service account. Each security policy is formulated to lower the network risk level without blocking the traffic and tracking policy violations. This is focused on monitoring the traffic and allows the admin to make sure that the created policy is full without impacting the traffic.
Silverfort has three types of authentication policies for service accounts:
- Block access
- Alert to SIEM
- Alert
For each policy created with Silverfort, administrators can choose sources, destinations, authentication protocols, when policies should be applied, and what actions the system should take in case of a deviation.
In the case of an organization with a large number of service accounts, Silverfort allows admins to create general policies that can be assigned to multiple service accounts. This can be done by using Silverfort’s recommended policies.
Once policies have been created for all service accounts with Silverfort, admins can simply enable and automatically enforce these policies without the need to make any changes to applications, change passwords, or make use of any proxies. With complete visibility into these accounts and the ability to proactively protect service accounts with access policies ,organizations will now be well-equipped to reduce their attack surface area from compromised service accounts.
Learn More About Silverfort’s Service Account Protection
The alarming reality of service account compromises cannot be ignored, as they continue to occur regularly and have been instrumental in major, high-profile cyberattacks. These incidents serve as stark reminders of the critical importance of securing service accounts and implementing robust protective measures.
The compromised service accounts have emerged as a preferred target for malicious actors due to their elevated privileges and widespread access within organizations. These accounts often hold the keys to the kingdom, granting unauthorized malicious actors entry to sensitive data, critical systems, and confidential resources.
To address this organizations must prioritize the implementation of the service accounts security best practices such as strong authentication, regular monitoring, and deploying strict access policies. By prioritizing service account security, organizations can mitigate the risk of compromised service accounts being deployed by malicious actors in cyber attacks.
Interested in seeing how Silverfort can help you to discover, monitor, and protect service accounts? Request a demo here.
The post Applying Service Accounts Security Best Practices with Silverfort appeared first on Silverfort.
*** This is a Security Bloggers Network syndicated blog from Blog - Silverfort authored by Zev Brodsky. Read the original post at: https://www.silverfort.com/blog/applying-service-accounts-security-best-practices-with-silverfort/





