
A Beginner's Guide to 2FA and MFA
A Beginner's Guide to 2FA and MFA
Category
Cybersecurity Fundamentals
Risk Level

Everyone is talking about 2FA and MFA these days as the best way to stop hackers and cybercriminals. But what’s the difference, and what are the best options when enabling it? Let’s dive in!
“What is Multi-factor Authentication (MFA)?”
To describe what MFA is, let’s first start with what it isn’t. Today, many people when they sign up for a new account for an internet-based service are asked to pick a password to help secure their account from unauthorized access. In most cases (though really it should be *all* cases) the service requires that you pick a password that conforms to their complexity requirements to ensure it is safe. In many cases, a strong password of sufficient length and complexity is good enough to protect you from most common attacks such as password guessing or bruteforcing, but in some cases it is not. That is where MFA comes in.
MFA is pretty straight forward if you think about it. A password is one “factor” or step for authenticating or proving your identity as the owner of an account, and while password-based authentication alone is a good start, you should opt for an additional layer of protection where available. For instance, in securing your high risk accounts like banking or personal finance accounts, healthcare accounts, government services accounts (DMV, IRS, etc.), email accounts, utility accounts, social media accounts, and other accounts for services where you may provide personal information, health information, credit card or payment information or where you generally want to be a bit more cautious even if the account is not particularly important . That’s where a second factor (also called two-factor authentication or 2FA) or even third factor may be used to provide that peace of mind. We’ll use the two terms, 2FA and MFA, interchangeably in this post, but the main difference comes from if you choose two options (2FA) or more than two options (MFA).
A password is considered “something you know”, a secret more or less that shouldn’t be shared. Other examples of “something you know” may include a PIN (like for your ATM card) or the answer to a security question (“What’s your mother’s maiden name?”). A second factor or third factor may be “something you have”, such as a mobile device (smartphone) or hardware device specifically designed to authenticate you (smart card, RSA Token, RFID badge, credit card with an RFID chip embedded) or “something you are”, which can include biometric features used to identify yourself such as a fingerprint, your iris or retina, voice pattern, or facial features for facial recognition (FaceID anyone?). Multi-factor authentication combines the “something you know” factor, with the “something you have” and / or “something you are” factors to add additional layers of identity verification before granting you (or someone else) access to your 2FA/MFA-enabled accounts.
“Okay, but what do these additional factors protect against if I’m already using a long, complex password? “
Well for one, they protect you in the event that one of the service providers you happen to have an account with is compromised, and your password (or personal information that could be used to obtain or reset your password elsewhere) is cracked or leaked. This is especially true if you like to reuse the same passwords (or similar passwords) for convenience, since once that password is compromised anywhere, it should be assumed it is compromised everywhere.
Imagine your social media account is hacked, and they notified everyone that they lost the passwords to all their customers’ accounts. If you used the same password, a hacker now has access to your Facebook, Twitter, or Instagram accounts and can post on your behalf, or do more nefarious things. Beyond that, if you reuse passwords for convenience, that hacker may now be able to access your other accounts that happen to use that same password. NOT GOOD!
2FA/MFA adds an additional layer(s) to the accounts where it is enabled such that even if a hacker guesses or cracks your password, they won’t be able to get into your account without providing the “what you have” or “what you are” factors. That should give you some time to go through and update your passwords and practice a little better password hygiene.
“So then are all 2FA/MFA options created equal?”
Unfortunately, no, but remember any 2FA/MFA is stronger than just a password alone. Certain methods of authenticating for 2FA/MFA have their own security issues as well and should be avoided for very important accounts such as personal finance, healthcare, or email accounts. Remember your email probably is where you send things like password recovery / reset emails, bank statement emails, personal emails, maybe sensitive business email, and probably much more stuff that if exposed to a hacker could leave you very, very vulnerable to further attacks or damage, so email accounts are amongst the most critical accounts to protect.
So what are your options? Below we’ll break down some common 2FA/MFA second and third factors used for authentication, and let you know if there’s any risks you should consider before choosing those, if you have such an option. If you don’t have an option, it’s still better to enable 2FA/MFA regardless.
Option 1: SMS Text-based One-Time-Passcodes
Most services today allow you to enable 2FA as a SMS text-based one-time-passcode to provide additional verification you are the account owner. What happens here is, you provide your mobile phone number to the service, and they register it and associate it with your account. Each time you login with your username and password, it then prompts you to enter a passcode that has been texted to the phone number you provided. This code usually expires after a short period of time so if you don’t enter it fast enough it may expire and not work. The code is also only one time use, meaning you cannot use a previous code texted to again once it has been used or expired. Each time you login, a new passcode will be sent to you. If you don’t provide the code sent to you, you can’t get in, even if you entered your account password properly!
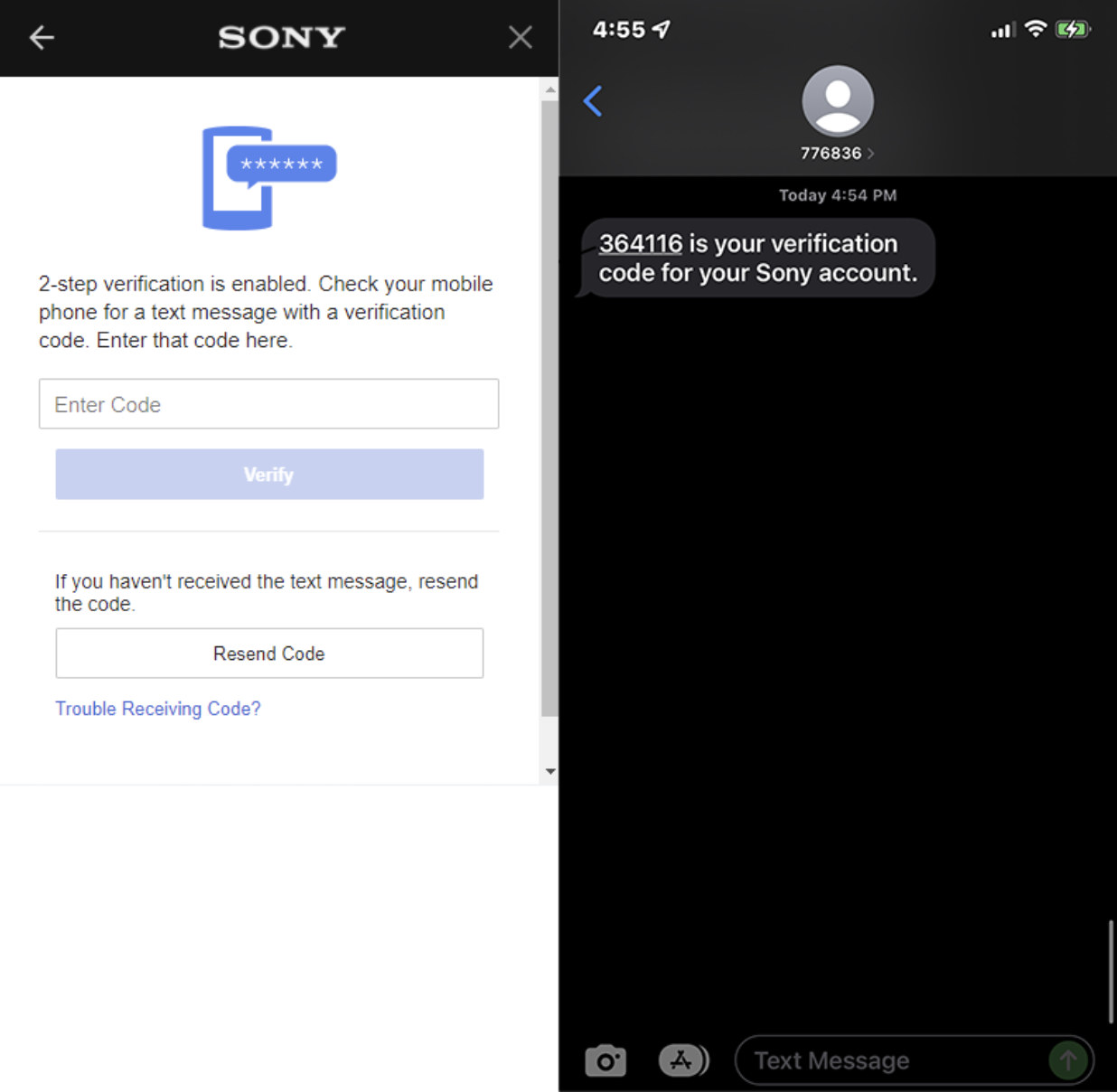
Example of SMS based 2FA
SMS text-based one-time-passcodes are good enough for most accounts, but may not be such a good idea for your highly valued and important accounts like your bank account, financial accounts, email accounts, or healthcare related accounts. That’s because hackers have become increasingly better at gaining unauthorized access to mobile phones. In many cases, the hackers can call your cell phone service provider, impersonate you with a few details they gathered through other means, and execute what is known as a “SIM swap” - check out our ACT post about this here. A SIM swap basically means the hacker was able to convince your carrier to switch the device associated with your account and phone number to a phone or device they control. Thus, when you (or they) attempt to sign into an account with SMS text-based one-time-passcode authentication enabled, the one-time-passcode is sent to their device now registered to the phone number, rather than your phone. With that code, the hacker can then login to your account, even though you had 2FA/MFA enabled.
These SIM Swap attacks have increased significantly in recent years, which is why SMS text-based one-time-passcodes are no longer recommended for your most important accounts, unless it is the only option of course.
Option 2: One-time-passcode Mobile Apps (i.e. Authenticator Apps)
In addition to SMS text-based one-time-passcodes, many services are now offering 2FA/MFA with authenticator apps. Authenticator apps generate random passcodes on timed intervals that are only valid and accepted within those time frames by the service provider when you are attempting to login to your account. Generally, when these are enabled, you will need to install an Authenticator app such as Google Authenticator, Microsoft Authenticator, or LastPass Authenticator. Once installed, the service will provide you with a long text string to copy and paste into the Authenticator, or present you with a barcode like image called a QR code which you can scan from within the authenticator app to automatically add the specific one-time-passcode to that authenticator app. You can add multiple accounts to the same authenticator app, as each will utilize a different, unique rolling passcode. These passcodes are synchronized with a server utilized by the service provider and rotate usually on a 30-second timer.
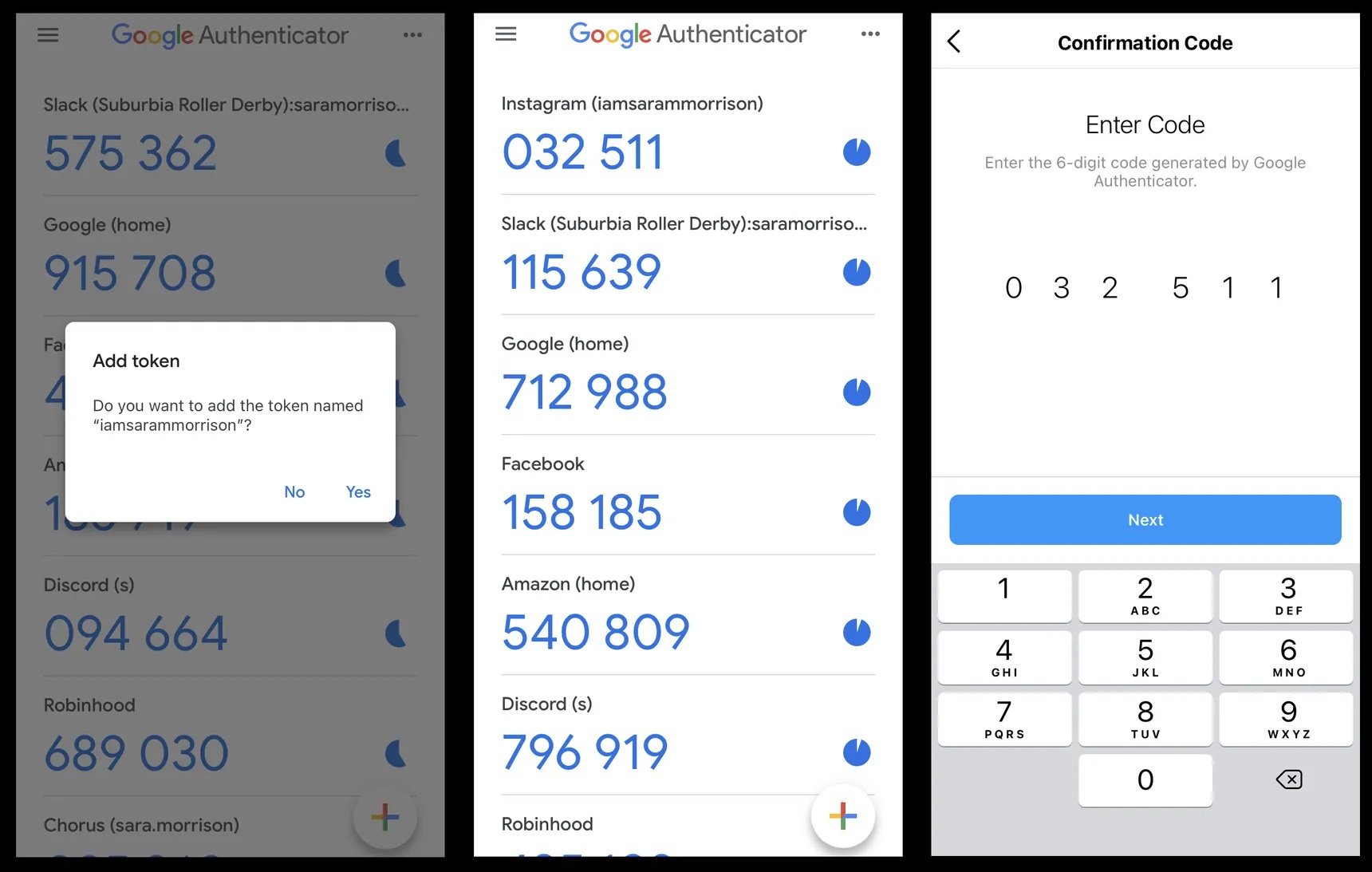
Example of an authenticator app based 2FA
When you put the passcode from the authenticator app into your service provider site or application, it will verify this code against the code from the server and if they match you will be granted access. Again, this prevents a hacker who has your password from gaining access to your account without also having the smartphone/device with the authenticator app on it. Today, this is the preferred method of 2FA/MFA for your critical accounts. It provides the “what you have” factor with your password, and is not susceptible to compromise as easily as the SMS text-based one-time-passcode option.
However, there are some drawbacks to this method. Specifically, they’re a real pain when you change devices. The authenticator apps tie the rolling passcode to the smartphone or device it is initially added to, and there isn’t really a backup method that supports migrating the codes from one device to another easily, as that would create a security weakness in the method. Instead you must re-initiate the process to add the account to your authenticator app on the new device. This can sometimes prove problematic if you forget to do this before you get rid of, or if you no longer have access to, the initial device; like when you lose your phone. In such cases, service providers generally offer a “fallback” method such as SMS text-based one-time-passcode verification to get you into your account so you can re-initiate the authenticator app registration process.
Option 3: Push Notification (In-App Approve / Deny)
A third, and very common method of 2FA/MFA offered by many services and applications for additional account security is Push Notification based authentication. This method requires you to download an app and register your phone, which then can be used by the service provider to send Push Notifications through an installed application to verify your identity and authentication request. Under the hood, push authentication uses public key cryptography to generate a public and private key pair on the registered device. That private key is securely stored on the smartphone or device where it cannot be compromised, but the public key is sent to the service provider’s servers and stored. When a Push Notification is sent to the device that is registered (usually a pop up that shows up at the top of your mobile phone), and the user trying to authenticate responds by pressing “Approve”, the private key signs a message that is sent back to the server and the service provider, with the public key, can verify it originated from your device only proving your identity and authenticating you in the process.
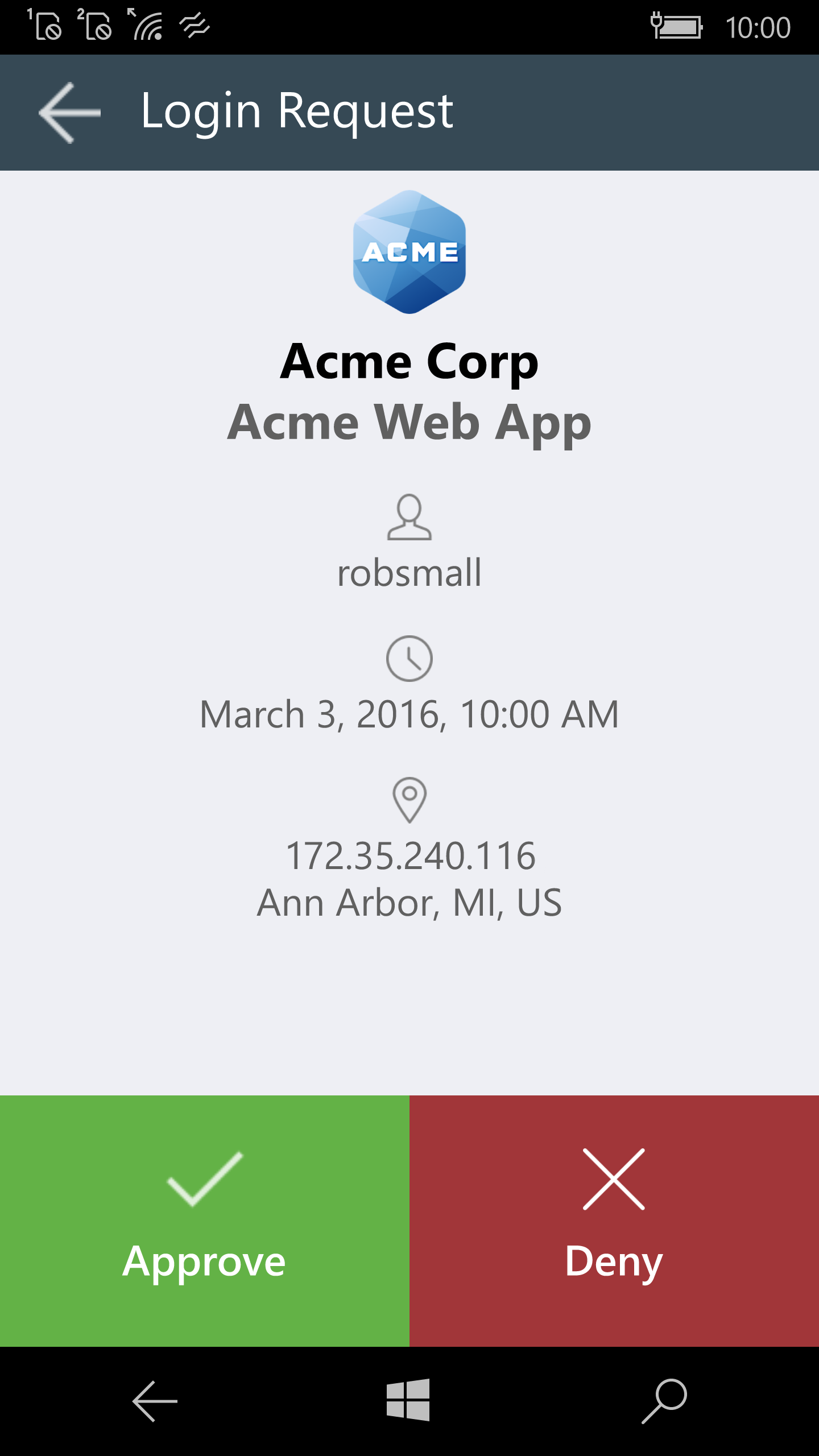
This is the most secure of the three most common methods of 2FA/MFA available as the strong public key cryptography provides a very high level of security over the prior two methods. It also allows you to glean a bit more information about the login attempt in the event it wasn’t you since service providers can include that information in the Push Notification sent to you (at a lower cost to them than a text message), so you can see if maybe it was an actual hacker or an errant family member or friend who is simply trying to mooch access to your Netflix account. However, Push Notification-based authentication isn’t as widely supported as the prior two methods, primarily because it requires the user to take more steps in downloading an app if they don’t already need one, requires more infrastructure for service providers to implement, or requires them to integrate with a third-party to offer it to customers, such as with Okta, Duo Mobile, Microsoft, Google, or LastPass to name a few which provide Push Notification capabilities to services leveraging their authentication mechanisms.
Option 4: Hardware Authentication
Hardware Authentication is one of the oldest forms of 2FA / MFA, but also, one of the most secure. Hardware Authentication is provided by a standalone hardware device such as a USB key or SmartCard. When plugged into your computer or device, this key or card provides verification to a login service of your identity for authentication purposes. Like Push Notifications, these types of hardware authenticators use public key cryptography. When you set up the device, a key pair is created (public key and private key). The private key is securely stored on the device, and the public key is registered with the service provider where you are linking the device to your account to support authentication. By registering the public key with the service provider, they can verify your identity from the digital signature sent from your USB key or SmartCard used during the authentication process.

These are amongst the most secure forms of authentication available, and compromising an account with hardware-based 2FA/MFA requires a hacker to possess or acquire the hardware authenticator from you before they can gain access. Unfortunately, these devices are not very highly supported as a second or third factor due to the infrastructure costs of enabling them by service providers, and the added friction of requiring a user to then buy a standalone device just to authenticate. In most cases organizations opt for Authenticator App or Push Notification-based authentication as a second or third factor because the cost to the organization and the user is advantageous.
If there are specific accounts that you deem absolutely critical and Hardware Authentication is available from the service provider as a second or third form, you may want to consider using it - as long as you don’t mind having to carry around a USB key, SmartCard, and/or possibly an adapter for your mobile devices to be able to utilize them. However, in most cases, the Authenticator App or Push Notification options will provide adequate security for your needs, without needing to worry about losing a tiny USB fob or a SmartCard to the depths of the tiny space between your driver’s seat and center console.
Option 5: Biometric Authentication
Biometric Authentication utilizes unique biological features to verify the identity of an individual authenticating to a service. This method most commonly uses a set of static features such as a fingerprint, palm print, facial recognition, or iris or retina scan to uniquely identify the individual and verify them.

From a cybersecurity perspective, biometrics are only as strong as the technology used to identify the biometric features. That’s not to say biometrics aren’t secure, it’s just that some technology is better than others at preventing things like spoofing, or fooling the mechanism, or preventing false acceptance and your mileage may vary. For example, you wouldn’t want to use facial recognition as a second factor if you had an evil, identical twin running around.
Beyond that, Biometric Authentication isn’t all that widely used. You may notice you can login to your Windows or Mac laptop with the thumbprint reader, or use the fingerprint scan or facial identification feature of your iPhone or Android smartphone, but most web-based services do not support biometrics yet. Many mobile apps do allow you to “pass through” thumbprint or FaceID from the smartphone to the app to prove identity, but that generally comes after you’ve already authenticated at least once to enable it. It is also expensive for service providers to implement, and creates privacy and compliance burdens for them most aren’t willing to take on. For that reason Biometric Authentication is still primarily used only to support device authentication (to Windows, MacOS, iOS, Android devices), or physical, in-person access authentication to things like sensitive facilities (e.g. data centers, Sensitive Compartmented Information Facility).
We should also note that just using something like FaceID does not actually mean you’re using 2FA/MFA. Unless you enter your password and THEN use FaceID, you’re technically only using one form of authentication; not two or more!
“That’s a LOT of options. So which should I use?”
We know we sound like a broken record, but again two (or more) factors are always better than one. We’ve provided you with some information on your options, but really it depends on what your service providers offer to protect your accounts, and what your own personal risk tolerance is. In most cases, Authenticator App one-time-passcodes will be your best bet as a second factor, since it is more ubiquitously offered than Push Notification or Hardware Authentication, and somewhat easier to use if you don’t mind having to jump back through the hoops each time you upgrade your phone.
That’s not to say we are trying to scare you away from SMS text-based one-time-passcodes as a second factor. While the other methods are generally an improvement over the SMS text-based one-time-passcode from a security perspective, if that is your only option then we’d advise you to use it, and in many cases, you may find that you are comfortable with the tradeoff of convenience SMS text-based one-time passcode 2FA/MFA provides over the potential risk.
Follow us - stay ahead.
Read more of the ACT
After Firefox was targeted at Pwn2Own 2025, Mozilla responded with same-day patches - a textbook example of proactive cybersecurity. Learn how tabletop exercises, vulnerability testing, and team communication can keep your organization ready for real threats.
The DoD has officially shut down DIBNet, the portal for reporting cyber incidents under DFARS 252.204-7012. This ACT post explains what’s changing, where incident reporting now goes, and how to stay compliant with the new DCISE process.
Data breaches are expensive but smart preparation can make them survivable. We break down how small businesses can reduce cyber risk with simple steps like training, planning, and response readiness.









