
When U.S. consumers have their online bank accounts hijacked and plundered by hackers, U.S. financial institutions are legally obligated to reverse any unauthorized transactions as long as the victim reports the fraud in a timely manner. But new data released this week suggests that for some of the nation’s largest banks, reimbursing account takeover victims has become more the exception than the rule.
The findings came in a report released by Sen. Elizabeth Warren (D-Mass.), who in April 2022 opened an investigation into fraud tied to Zelle, the “peer-to-peer” digital payment service used by many financial institutions that allows customers to quickly send cash to friends and family.
Zelle is run by Early Warning Services LLC (EWS), a private financial services company which is jointly owned by Bank of America, Capital One, JPMorgan Chase, PNC Bank, Truist, U.S. Bank, and Wells Fargo. Zelle is enabled by default for customers at over 1,000 different financial institutions, even if a great many customers still don’t know it’s there.
Sen. Warren said several of the EWS owner banks — including Capital One, JPMorgan and Wells Fargo — failed to provide all of the requested data. But Warren did get the requested information from PNC, Truist and U.S. Bank.
“Overall, the three banks that provided complete data sets reported 35,848 cases of scams, involving over $25.9 million of payments in 2021 and the first half of 2022,” the report summarized. “In the vast majority of these cases, the banks did not repay the customers that reported being scammed. Overall these three banks reported repaying customers in only 3,473 cases (representing nearly 10% of scam claims) and repaid only $2.9 million.”
Importantly, the report distinguishes between cases that involve straight up bank account takeovers and unauthorized transfers (fraud), and those losses that stem from “fraudulently induced payments,” where the victim is tricked into authorizing the transfer of funds to scammers (scams).
A common example of the latter is the Zelle Fraud Scam, which uses an ever-shifting set of come-ons to trick people into transferring money to fraudsters. The Zelle Fraud Scam often employs text messages and phone calls spoofed to look like they came from your bank, and the scam usually relates to fooling the customer into thinking they’re sending money to themselves when they’re really sending it to the crooks.
Here’s the rub: When a customer issues a payment order to their bank, the bank is obligated to honor that order so long as it passes a two-stage test. The first question asks, Did the request actually come from an authorized owner or signer on the account? In the case of Zelle scams, the answer is yes.
Trace Fooshee, a strategic advisor in the anti money laundering practice at Aite-Novarica, said the second stage requires banks to give the customer’s transfer order a kind of “sniff test” using “commercially reasonable” fraud controls that generally are not designed to detect patterns involving social engineering.
Fooshee said the legal phrase “commercially reasonable” is the primary reason why no bank has much — if anything — in the way of controlling for scam detection.
“In order for them to deploy something that would detect a good chunk of fraud on something so hard to detect they would generate egregiously high rates of false positives which would also make consumers (and, then, regulators) very unhappy,” Fooshee said. “This would tank the business case for the service as a whole rendering it something that the bank can claim to NOT be commercially reasonable.”
Sen. Warren’s report makes clear that banks generally do not pay consumers back if they are fraudulently induced into making Zelle payments.
“In simple terms, Zelle indicated that it would provide redress for users in cases of unauthorized transfers in which a user’s account is accessed by a bad actor and used to transfer a payment,” the report continued. “However, EWS’ response also indicated that neither Zelle nor its parent bank owners would reimburse users fraudulently induced by a bad actor into making a payment on the platform.”
Still, the data suggest banks did repay at least some of the funds stolen from scam victims about 10 percent of the time. Fooshee said he’s surprised that number is so high.
“That banks are paying victims of authorized payment fraud scams anything at all is noteworthy,” he said. “That’s money that they’re paying for out of pocket almost entirely for goodwill. You could argue that repaying all victims is a sound strategy especially in the climate we’re in but to say that it should be what all banks do remains an opinion until Congress changes the law.”
UNAUTHORIZED FRAUD
However, when it comes to reimbursing victims of fraud and account takeovers, the report suggests banks are stiffing their customers whenever they can get away with it. “Overall, the four banks that provided complete data sets indicated that they reimbursed only 47% of the dollar amount of fraud claims they received,” the report notes.
How did the banks behave individually? From the report:
-In 2021 and the first six months of 2022, PNC Bank indicated that its customers reported 10,683 cases of unauthorized payments totaling over $10.6 million, of which only 1,495 cases totaling $1.46 were refunded to consumers. PNC Bank left 86% of its customers that reported cases of fraud without recourse for fraudulent activity that occurred on Zelle.
-Over this same time period, U.S. Bank customers reported a total of 28,642 cases of unauthorized transactions totaling over $16.2 million, while only refunding 8,242 cases totaling less than $4.7 million.
-In the period between January 2021 and September 2022, Bank of America customers reported 81,797 cases of unauthorized transactions, totaling $125 million. Bank of America refunded only $56.1 million in fraud claims – less than 45% of the overall dollar value of claims made in that time.
–Truist indicated that the bank had a much better record of reimbursing defrauded customers over this same time period. During 2021 and the first half of 2022, Truist customers filed 24,752 unauthorized transaction claims amounting to $24.4 million. Truist reimbursed 20,349 of those claims, totaling $20.8 million – 82% of Truist claims were reimbursed over this period. Overall, however, the four banks that provided complete data sets indicated that they reimbursed only 47% of the dollar amount of fraud claims they received.
Fooshee said there has long been a great deal of inconsistency in how banks reimburse unauthorized fraud claims — even after the Consumer Financial Protection Bureau (CPFB) came out with guidance on what qualifies as an unauthorized fraud claim.
“Many banks reported that they were still not living up to those standards,” he said. “As a result, I imagine that the CFPB will come down hard on those with fines and we’ll see a correction.”
Fooshee said many banks have recently adjusted their reimbursement policies to bring them more into line with the CFPB’s guidance from last year.
“So this is heading in the right direction but not with sufficient vigor and speed to satisfy critics,” he said.
Seth Ruden is a payments fraud expert who serves as director of global advisory for digital identity company BioCatch. Ruden said Zelle has recently made “significant changes to its fraud program oversight because of consumer influence.”
“It is clear to me that despite sensational headlines, progress has been made to improve outcomes,” Ruden said. “Presently, losses in the network on a volume-adjusted basis are lower than those typical of credit cards.”
But he said any failure to reimburse victims of fraud and account takeovers only adds to pressure on Congress to do more to help victims of those scammed into authorizing Zelle payments.
“The bottom line is that regulations have not kept up with the speed of payment technology in the United States, and we’re not alone,” Ruden said. “For the first time in the UK, authorized payment scam losses have outpaced credit card losses and a regulatory response is now on the table. Banks have the choice right now to take action and increase controls or await regulators to impose a new regulatory environment.”
Sen. Warren’s report is available here (PDF).
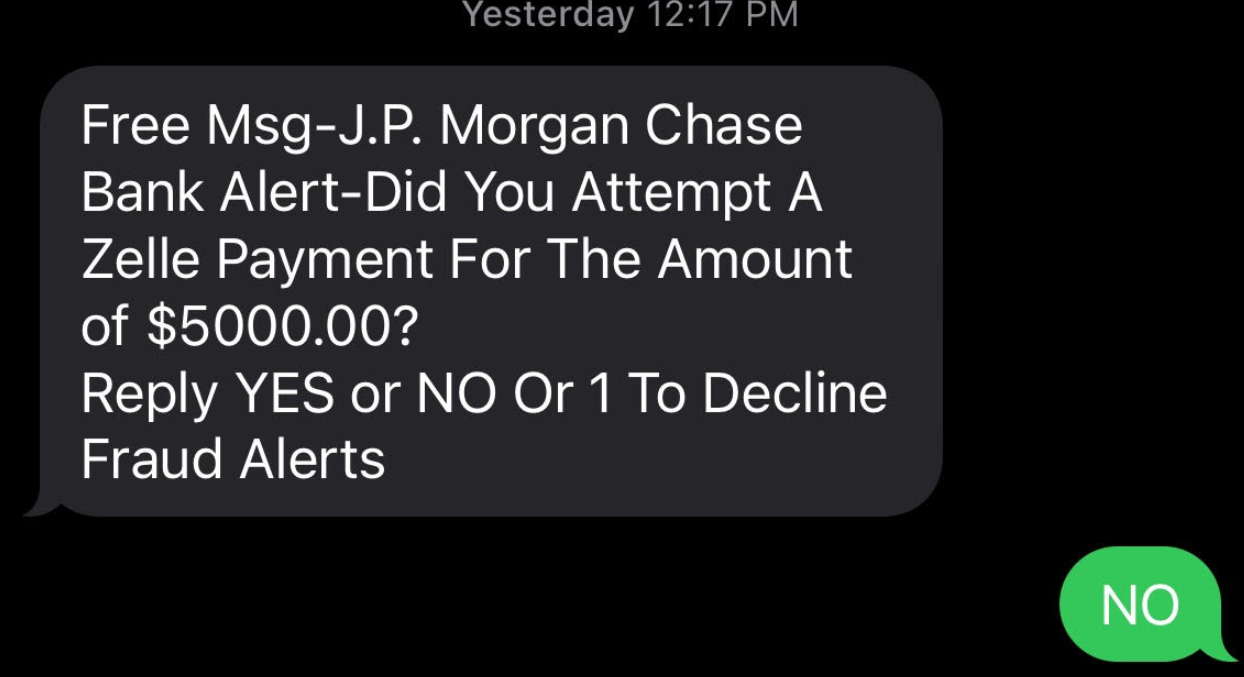
There are, of course, some versions of the Zelle fraud scam that may be confusing financial institutions as to what constitutes “authorized” payment instructions. For example, the variant I wrote about earlier this year began with a text message that spoofed the target’s bank and warned of a pending suspicious transfer.
Those who responded at all received a call from a number spoofed to make it look like the victim’s bank calling, and were asked to validate their identities by reading back a one-time password sent via SMS. In reality, the thieves had simply asked the bank’s website to reset the victim’s password, and that one-time code sent via text by the bank’s site was the only thing the crooks needed to reset the target’s password and drain the account using Zelle.
None of the above discussion involves the risks affecting businesses that bank online. Businesses in the United States do not enjoy the same fraud liability protection afforded to consumers, and if a banking trojan or clever phishing site results in a business account getting drained, most banks will not reimburse that loss.
This is why I have always and will continue to urge small business owners to conduct their online banking affairs only from a dedicated, access restricted and security-hardened device — and preferably a non-Windows machine.
For consumers, the same old advice remains the best: Watch your bank statements like a hawk, and immediately report and contest any charges that appear fraudulent or unauthorized.




Not to mention, online banking in the US is hopelessly insecure. Authentication still based on SMS. My bank now allows the use of RSA Securid, for a $25 charge for the device, because apparently their IT staff is too incompetent to handle a mobile phone app like Google Authenticator (please don’t ask about FIDO)……but you can’t disable authentication with SMS! And this is advertised as a courtesy!
You keep recommending using a non-Windows OS for online financial sites, but how much safer is Apple, Android, or Linux (two or three of which share the same foundation as I understand it) actually? The past year has revealed a multitude of vulnerabilities in those OSs too, some of which apparently existed for years. Moreover, if substantially more people gravitate to non-OS operating systems as daily drivers, namely for laptops/desktops, how “safe” will those OSs be when criminals start directing their energies to the market share leaders? It’s good to continually emphasis best online practices for individuals, but the discussion in your second to last paragraph is not germane to the gist of the article. The problem with Zelle is not its IT infrastructure (for now), but the fact that so many people are gullible and believe almost everything they see in “print” in texts and emails. Frankly, I do not understand why so many people fall for Zelle scams since I have never received a “fraud” call from any of my financial institutions or any type of call other than marketing call. Moreover, I question the mental competency of people who believe that they will be arrested the next day for non-payment of a fine or back taxes, having their utilities shut off the next day due to non-payment without any prior paper-based written notification, or really believe that any government/non-“mom and pop” business entity will only accept Zelle payments or “gift” cards as payment (the gift card as payment scam should be rejected on the basis of common sense alone). It seems to me that more people need to be made aware of how banks, brokerages, governments, utilities, etc. operate or basically made aware of their rights under the law when dealing with these entities so that they do not fall for scammers.
Brian is trying to point out Business accounts don’t have the same protections and so are more susceptible to these kind of tactics.
A non-windows based device (as of today) has fewer security issues so is another step small businesses can take.
That all said, you’re spot on — training and constant awareness I think is the single biggest thing anyone can do to protect themselves.
Thanks. I understood it as part of entire article, not a subpart of the business protection section. My understanding could be incorrect.
Yes, non-Windows OSes have vulnerabilities. They are less likely to be exploited, because most users (and especially most unsophisticated users) use Windows. You are correct that if everyone migrated to a different platform, it would be targeted and Krebs’ advice would need to change. If you thought said advice was graven in stone, I’m sorry to have disappointed you.
And then we come to the reliable “if only everyone were as clever as me” rejoinder. Regarding “mental competence”, have you ever been credibly threatened with severe consequences for non-payment? I’m going to guess not, because I suspect you’d be a bit more sympathetic someone who regularly has to confront such (legit) threats.
Concur with your first section. Disagree with your second section–the part about consequences of non-payment. You are correct, I have never been threatened due to non-payment since I pay my bills and live below my means. However, I sympathize with many people who incur large medical debt. Regardless, most people are contacted numerous times about actual debts, usually many times by the primary creditor, then multiple times by a bill collector, and then a couple of times by the courts. So if a person hasn’t paid the debt before the Zelle scammers contacted them, why did they all of a sudden have the funds then or all of a sudden had a change of heart? Of course, few who owe money ever receive prior notice, so they claim. Yet, few don’t receive and act on notices when they are the recipient of money. Gimme me break.
it is fear that moves people to react thoughtlessly. Especially for people who have never before experienced such things. do you understand fear?
I agree with your first section. I disagree with your second section. You are correct, I have never been threatened because of non-payment since I pay my bills and live beyond my means. That said, I sympathize when life events results in a change in financial position. Regardless, most debtors are contacted numerous times by the original creditor, buy bill collectors, and then by the courts. If the debtors did not pay or could not pay before the Zelle scammers contacted them, why did they all of a sudden believe that the consequences of non-payment would be real? Of course, most people who owe money claim that they’ve never received prior notice of the debt. It’s interesting how scammers were able to find the debtors that the legitimate creditors could not . Give me a break.
I am replying to the second of two replies that you seem to have posted in succession that are nearly the same but obviously the second is a revised version… The first reply starts with ‘Concur with your first section.’ and this second reply that I am replying to now begins with ‘I agree with your first section.’
The reason I am bringing this up is because I have been experiencing some problems trying to post on Brian’s previous article about LinkedIn bots and I didn’t know if it was me (my writing style can be a bit um… over the top and sometimes the approval bots don’t know what to do – particularly when they encounter an unusual amount of ellipses…), Chrome (because it’s Chrome), Android (because it’s Android), the approval bots that Brian’s site are running (because they’re bots) or Brian himself (sick of seeing so many ellipses…)…
Have you and/or anyone else reading this experienced problems replying to articles on Brian’s site (long delays, notifications that the approval bots are working on it for an inordinate amount of time, replies disappearing, etc.)…?
I’m gonna write Brian too but I just wanted to first make sure that it wasn’t just me that he’s mad at (LOL just kidding CyberHero Krebs we know you’re not like that – just your bots are 😀 😀 :D)…
Thanks
P.S. I’m seeing just now that “Thomas Leahy” seems to be experiencing the same thing to the point of actually changing his display name to “Armorlog” n the third of 3 consecutive nearly identical entries… I had tried the same thing in case I was being rejected by display name after having pissed off the bots one time too many already LOL…
P.S.S This is now the second time I’ve sent this reply. This text is to see if making enough of a change to a reply will still be flagged as duplicate…
Mostly not, dupes stay up, everything takes time to change if it will.
The trick is not to worry about it. 😀
The scammers use automated systems to contact a large amount of people. Most of them will ignore the contact but some will respond. Some of the responders won’t even actually owe money to anybody, but have memory lapses and can panic.
I so agree! I worked for the federal government for 20 years dealing with PII which was always kept secured and if you let any of it get compromised, you faced prison because that’s a felony in those days. As a hobby I’ve shut down frauds and scammers for 25 years. I’m always advising people on how to be safe on the internet or their phone or in general when doing business. I’m in my late 50s but it is insane how many people from all age ranges going from 20 to my own age to 80 don’t know to use common sense on these issues, to never take a call from a number they don’t recognize, and don’t have sense to ask the caller for their name and number and ask to call them right back. Simple common sense would stop a lot of these frauds and scams but people don’t have that anymore. SAD!!!!
OTOH, why isn’t there a public script / checklist for people to evaluate?
A list of instructions for evaluating a given call, text or email. Steps 1-5.
Step 1, do you recognize the number, etc. Keep it simple. Does this exist?
The public could be served given the % that might actually read / use that.
You could put law enforcement contact info on the card and everything.
Mail it to everybody, PSA’s on how to use it, the whole thing.
This information does exist, people have published lists, etc., but rarely are they used and they soon get buried in the noise. It’s not something most people and institutions truly care about for whatever reasons.
I agree it exists in a nubulous quasi-form somewhere, my point is it needs to be structured, strategically coordinated and disseminated to everyone and everyone’s grandmother and grandpa and neighbor. It’s worth much less if the people most likely to be conned don’t have ubiquitous ready access to it. It needs to be a fuction of civil society, something you complain about the limitations of rather than being able to avoid. We get hundreds of political ads in the mail every election cycle and less than a single anti-fraud informational checklist. We need to codify the best practices and eliminate the noise, exactly for that reason.
*Nebulous. Finger fell asleep.
The OS of your device is not the issue here with the Zelle scam that Brian has described. It is not about exploiting vulnerabilities but is a social engineering attack.
Yes, better OS “security” will be good to have but don’t get too hung up on it. The vast majority of the frauds discussed herein are social engineering schemes. No amount of OS security enhancement are going to alleviate those scams.
“This is why I have always and will continue to urge small business owners to conduct their online banking affairs only from a dedicated, access restricted and security-hardened device — and preferably a non-Windows machine.”
Where does a small-to-medium size business aquire such a secure device? And does such device also require occasional updates from non-local sources?
The way this is done in 2022 is to get a Linux LiveCD Kiosk software, such as porteus to name one, and create a landing HTML page on the LiveCD that links to your banking sites via IP Address. You can also do things like directly load the banks certificates in there rather than using web certificates. From there you load it up on and boot from a USB Thumb drive. Literally get some post-refresh gear and a SOHO Firewall that has an anti-phishing web filter, give the SOHO Firewall a public IP, hook the computer into it via NAT, and go to town. It requires some setup and config. Far better is to do one-time-pad and a callback. You setup the transactions on the bank website, input a one time pad value, and you then call the bank, and then the bank calls you back for confirmation and an additional one time pad value. There are various ways banks provide the one time pad booklet depending on how the banking contract is setup. My preference is to have the company notify the bank that someone will go to a location at a time and date to physically pick up the OTP, then present 2 forms of government ID, have themselves photographed, then they get the booklet. You pair that with a RSA SecureID and you have 2 or 3 layers of CIA which is very hard to break.
These static and pre-printed one-time pads do not however address the issue that they do not allow the user to see what they actually sign/authorize? The same OTP could be used for 1 USD or 1M USD.
In my (European, PSD2-reglated) opinion it takes devices or applications that clearly display what it is the user authorizes (amount, currency, recipient) an dthen signs only this information with a signature matching only this transaction and timestamp.
Chromebooks. Cheap, reliable, built in security. Would the security mavens agree?
Worth thinking about, as long as the Chromebook was still updated by Google (the device’s Auto Update Expiration data has not passed). See https://support.google.com/chromebook/answer/9367166?hl=en
Considering you can get a Chromebook for well under $200, it is actually a decent choice. In terms of security, a machine designed to browse the web is going to be more secure than one designed to do everything.
That’s nonsense. It’s all about the user.
I got scammed with zelle this way years ago before I even knew what zelle was or that my bank auto enabled it. (Wells Fargo). They called me and unfortunately I was very high at the time and I got smooth talked into giving them the sms code thinking it was legit. At the end of the call after they made the transfer the ver well mannered nice person I was talking to said “thanks for the money b1tch) and hing up on me. Wells Fargo refunded the $2000.
Bank interfaces are defective they should not be relying on interpretation on user devices for security.
“non-windows” before Windows 10 would be accurate. Windows 10 or 11 with the latest updates is secure enough. It’s not Windows you have to worry about, but what other software are installed. You’re accessing the banking services using a web browser, and that’s the primary point of failure. Make sure you don’t have any browser add-ons that are suspect. The latest version of Firefox is secure, with only ad-block and tracking blocker add-ons. Have a dedicated computer for only business, with only limited software installed, and not used for web surfing, and you’ll be less likely to get trojaned, phished, etc.
Don’t ever use cell phones to conduct online transactions, they are the least secure devices. Don’t ever trust SMS or any other messages you receive on your cell phones regarding banking or any other financial transaction. Never reply to unsolicited texts. Always call back the business customer service line of the bank to confirm. Don’t give out your banking information to apps or any fin-tech services, etc.
The banks interfaces are defective they should not be using interpretation on customer devices in security routines.
The banks interfaces are defective they should not be using interpretation on customer devices for security routines.
Hi Louis Leahy I just posted the following to Ludivic Lalo, please read:
Hi Ludovic Lalo this is off-topic but relevant:
I am replying to the second of two replies that you seem to have posted in succession that are nearly the same but obviously the second is a revised version… The first reply starts with ‘Concur with your first section.’ and this second reply that I am replying to now begins with ‘I agree with your first section.’
The reason I am bringing this up is because I have been experiencing some problems trying to post on Brian’s previous article about LinkedIn bots and I didn’t know if it was me (my writing style can be a bit um… over the top and sometimes the approval bots don’t know what to do – particularly when they encounter an unusual amount of ellipses…), Chrome (because it’s Chrome), Android (because it’s Android), the approval bots that Brian’s site are running (because they’re bots) or Brian himself (sick of seeing so many ellipses…)…
Have you and/or anyone else reading this experienced problems replying to articles on Brian’s site (long delays, notifications that the approval bots are working on it for an inordinate amount of time, replies disappearing, etc.)…?
I’m gonna write Brian too but I just wanted to first make sure that it wasn’t just me that he’s mad at (LOL just kidding CyberHero Krebs we know you’re not like that – just your bots are 😀 😀 :D)…
Thanks
P.S. I’m seeing just now that “Thomas Leahy” seems to be experiencing the same thing to the point of actually changing his display name to “Armorlog” n the third of 3 consecutive nearly identical entries… I had tried the same thing in case I was being rejected by display name after having pissed off the bots one time too many already LOL…
That’s not how it works. You have to wait.
I had my life threatened over zelle scammers trying to get money to get it from me and account hacked and my identity compromised. And bank i had refused to help. And I am disabled. They said it wasn’t fraud and refused because of my communication barriers to offer anyone to help with me understanding them or for me to explain the situation better
Please look up the ADA laws or Google ADA attorney and get them on the case. Disabled Americans have many rights and how you communicate should never be an issue with any Bank financial institution utility company or vendor.
In the section describing the reimbursements, the PNC reimbursement should be $1.46 million, right?
Makes sense now. I have had problems with Wells Fargo for. Almost 2 year’s. Most of which has caused me so much hardship the biggest of since March 2022 today I received my 8th new debit card. My account has been compromised so much. The biggest one 4th of July weekend I started playing Coin Master and used Google Pay from my debit card.on the sixth I checked my balance only to find over $700 missing I mean there must of been 60+ charge’s to Google Pay I only received half back from Wells Fargo but 2 weeks ago letter from Google came my Google account was suspended until further notice. They also took my platinum points about $350. Worth. I’m sick over this I looked into old statements back to September 2021 and there’s recurring charges to consumer cellular avg. $40 was coming out don’t have clue who’s bill I paid and it’s to old for WF to handle whole thing probably totalsfew thousand dollars and it partially has to be zelle. They are attacking my cash app now. Yeah I just got new card Monday and Thursday 2:30 am text came from WF suspicious activity someone charged, $60 and $9 I have not slept since another new card arrived this morning I love barely on $1000 SSDI and I would like my money back and apologized to for the scam WF has done to me I don’t know where or who to go to please help me.
Michele Myers
Bakersfield CA
You are not the only one to have issues with Google messing up debits for coin master so perhaps we can find a third and launch a class action suit against Google for that. They won’t let me make an app purchases without my giving them a copy of a bank statement or my ID and I’m not dumb enough to do that. As I stated to another poster above please Google the term ADA attorney, contact them and explain the situation and they can get you started or refer you to an attorney that handles fraud and deals with disabled people. As a disabled American you have rights and I know this well because I’m a disabled American myself. When in doubt always seek an attorney because many of them will work pro bono and charge you only based on what they get for you.
Do yourself a favor, get away from WFB. Any credit union is better.
Do not use debit cards for random online purchases, but 1-time credit card service.
http://www.investopedia.com/financial-edge/0511/a-look-at-single-use-credit-cards.aspx
(aka “virtual” credit cards, a brief basic introduction, not the end of your research)
Don’t give your digits away to random online anything, that includes games.
Bryan says Zelle is enabled by default by many banks. If we asked, would they deactivate the account? Wouldn’t that be a good security measure?
At some banks you actually have to apply to be able to use zelle and I know this is correct because my credit union required me to sign up and I believe BB&t originally required the same. You’re a consumer call your bank and tell them you don’t want Zelle on your account if that is the case & see what they say. The best answer to those types of questions are going to come from your financial institution.
I bank with TD Bank and they deactivated Zelle for me immediately upon my asking them to.
PNC disabled it when I asked via the messaging system. I have never actually had someone want to be paid by it and I hire a lot of freelancers. It’s always paypal, venmo, or transferwise for not-usd.
Should really be a self service button and offer to disable if it isn’t used for 6+ months. Every bank could drastically reduce their risk surface if they auto disabled for non-use.
If you want to disable it, you can go to your bank app and clear out the settings.
Identity theft/fraud protection has become a standard offering on homeowners policies. How many times might banks have declined reimbursement because clients were protected by insurance?
Will do, Kim.
Thank you.
I have to say I see the banks’ POV here. If someone scams me and I hand them $100 cash, I don’t go to my bank and ask them to pay me. How (in most of the cases cited) is it any different that I did it with Zelle? If we have to create some sort of insurance against being scammed, then someone’s going to have to pay for it.
Well done!
…and Warren strikes again! Kudos to her and Brian for ripping the sheet off the face of these rotten banks.
“FDIC Insured to $300,000”; yeah-but only if the bank fails. If you screw up in a weak or non-lucid moment (ever have a car crash concussion? You’re goofers for days) and fall victim to these dogs, your life savings could go.
Damn. Digging a hole in the middle of the forest and burying a watertight and fireproof safe with your savings would be more secure.
We need some new laws to keep these baboons from shrugging their shoulders and saying, “You authorized it, pal. Tough bananas.”
Predatory Capitalism at it’s finest, the crooks AND the banks.
“Quis nos custodiet a custodibus?”
Election day is coming up-vote for who has your interests front and center, NOT for the ones who enable this BS while whining “Too many regulations! Oh, our poor banks, boo-hoo!”
The challenge is, how will a bank know when you intended to send money to Bob Smith and when Bob Smith scammed you into sending you money? Checks have the same problem, and ACH. But Zelle is instant payments so the payment is cashed out.
I don’t understand why banks are so reluctant to reverse Zelle payments. They’re all from one US bank account to another, and they know exactly which account to debit to return the money, not unlike bouncing a check. It’s not like an international bank wire.
Perhaps the current Zelle terms of service don’t let them do that but they could fix that. Yes, it would enable another kind of fraud where you pay someone and then disclaim it, but again, how different is that from bouncing a check?
“They’re all from one US bank account to another,” not accurate in the scam. Often once money is transferred initially, the funds are immediately auto transferred to other banks multiple times, including international.
That’s not how it works. When a person sends a payment to a registered phone # or email, it goes to the exact bank account registered. They then move the fund elsewhere and it’s not automated.
I know because I use Zelle to move money around.
I guess the gist of it is that you should not be using Zelle to pay or get paid by anyone besides close family and friends, never to pay or get paid for merchandise or services. I’ve used Zelle to give close family gifts for birthdays and special occasions but would never use it to pay for goods or services. Unfortunately there are lots of people lacking the smarts to pinpoint scams.
Scamming the customer into making fraudulent transfers themselves is the latest scourge in many a European market as well. Depending on the regulator, and indeed the processes banks have implemented to the customer authentication side, outcomes are somewhat different. And these are market which by regulation (PSD2) had to adopt strong 2FA for all electronic transfers as far back as fall 2019.
In one market, the UK where a report about this is publicly available, the ombudsman seems to rule against banks consistently when frankly they had little leverage to notice the customer was led to believe he was paying for some sort of service completely outside of the banking system and assisted the fraudster in initiating the transfer.
In other markets, the claim of lack of care on part of the customer -when they authorize a payment to a named merchant (EMV 3DS card payments) or a IBAN account number that was fed to them and which they did not verify- still holds up for the banks.
From my point of view, working on the fringes of the payments sector, I see the banks responsible for robust processes and displaying clearly to the customer what they are about to initiate (and this is also part of the regulation). What story the customer has been fed beforehand that leads to them making this transfer is outside of the control of the banks and I don´t really see how they could reasonably be held responsible for that. Of course, many blacklist IBANs of the fraudster as they become known, in Germany some banks wholesale-blacklisted N26 bank when they became the bank of choice for scammers due to their weak KYC/AML onboarding. But you can hardly block a whole prepaid-issuing bank without hitting legitimate cardholder top-ups as well.
Just look at the profiles of these CISOs and other executives in the cybersecurity. It’s a joke. None have any real background in security engineering and more. US doesn’t have any real talents anymore when it comes to core technology domains including cybersecurity.
Anyone with some useless certifications and connections get hired as a CISO!
Like that Target CEO once said he felt secure because his company was PCI compliant! Obviously, he was guided by an incompetent CISO.
Regarding the common Zelle fraud thing… I it will help a lot if banks add the following wording to their verification texts: A BofA REPRESENTATIVE WILL NEVER ASK YOU FOR THIS PIN. IF ANY PERSON ASKS YOU FOR IT THEN YOU ARE BEING SCAMMED.
Security by obsolescence ,I use an old Windows 6.5 mobile device for online finance.
Who targets winmo 6.5 today ?
With a bit of common sense as well,I seem to avoid 99% of fraud etc attempts.
Not keeping large amounts in accounts reachable online is just asking for trouble,every 14 days,I go in to my branch and physically fill out paper work to transfer what funds I’m going to need,the bulk is untouchable except by turning up in person,with the right identity proof,and electronic key,even though staff know me very well now,they HAVE to go through the rigeramole to access account.
Do you want convenience with high risk or zero risk and a bit of inconvenience ?
Its YOUR money,don’t expect banks etc to protect it properly,do it yourself.
Security by obsolescence is a terrible idea. Windows 6.5 mobile phones still use vulnerable software. There is no need for a hacker to “target” your specific Operating System, if it just uses an old and common browser like Internet Explorer.
You don’t necessarily need to be targeted specifically, and now even script kitties with 10-year-old exploits will work on your obsolete system.
It’s script kiddies. That makes one question the rest.
Haha, oops. Yeah speech to text hasn’t caught up to the lingo. Definitely feel free to question and learn about cyber security. There’s no expert that will disagree that security by obsolescence is bad.
You’re saying you comment with s2t to avoid a typo, I’m saying bruh.
Not to avoid a typo. Just for convenience when commenting from a smartphone.
Didn’t expect grammar natzys to ignore the content of the comment just to troll me. Although I do have a cyber stalker here that feels compelled to harass me, and typos often grant him the opportunity.
You can just say mealy is your stalker.
Yeah its insane that Ted Leaf suggests security through obsolescence. Maybe laymen like him seriously think that hackers do everything manually from targeting to exploit development. The reality is that hackers automate most tasks and simple vuln scanner would light up like christmas when it sees such an old device running such a legacy web browser. The hacker will have dozens of exploits to choose from.
thank you
This is not just a US issue. Many countries stiff victims unless the law states explicitly the bank is responsible.
The banks in question have to understand that by not refunding what is really a pittance for multi billion $ corporations, they are damaging the brand that they are placing a a competitor in the marketplace. I have had too many people try the Zelle scam on me in Face Book Marketplace. As a result I place in the text of the add I will not use Zelle.
The vendors of Zelle have to ask themselves one thing…
“Am I willing to lose market place traction because people no longer trust my system?”
I find it interesting that the Automated Clearing House has existed since the mid-1970s and one rarely, if ever, hears about issues with regard to reimbursement to consumers for unauthorized ACH debits to their accounts. These problems with Zelle P2P payments seem to involve the same banks that routinely refund consumers for unauthorized ACH debits but for some reason these banks are not automatically refunding consumers that use the Zelle platform. More data is needed about the reasons for the banks’ reluctance to reimburse consumers in these cases.
ACH fraud is significant if you look for it.
Consumers are usually reimbursed if the ACH fraud is reported within 60 days. For business customers, their window to report is 1 day. Plus if their business controls are loose, they are probably not covered.
Thanks Brian for the insight, I see where we fumble now and what we’re doing wrong. With love from war.
It’s one thing to hold the bank responsible for poor security — 100% agree with that. However, I find the presumption that the banks should have to pay for someone not doing due diligence and transferring money to fraudsters themselves offensive. If the user submitted the transaction themselves because that user fell for a scam, how is that the bank’s responsibility?
As a Zelle user, I hold to the same standard as cash. If I wouldn’t hand you cash, I am not going to send you a Zelle or Venmo payment. I am never going to act on a payment request via email or text, unless I know and confirmed with the sender. I see these tools as a way to settle payments with people I know. If I don’t know you and I am willing to pay you, I would use a credit card or cash. You have to know exactly what you are paying for before you authorize the payment, whether it is with cash or electronically.
How many different ways do banks have to say, “we will never ask you for a security code,” before suckers stop giving it out? If you give the info, or send money through Zelle to someone you don’t know that is YOUR responsibility, not your bank’s. Zelle does a good job of saying “make sure you know the person you’re sending money to” and “once the money is sent, it’s GONE.” And for Pete’s sake, use two-factor on your email so hackers can’t get in to retrieve password resets, codes, or other valuable info.