Google continues to struggle with cybercriminals running malicious ads on its search platform to trick people into downloading booby-trapped copies of popular free software applications. The malicious ads, which appear above organic search results and often precede links to legitimate sources of the same software, can make searching for software on Google a dicey affair.
Google says keeping users safe is a top priority, and that the company has a team of thousands working around the clock to create and enforce their abuse policies. And by most accounts, the threat from bad ads leading to backdoored software has subsided significantly compared to a year ago.
But cybercrooks are constantly figuring out ingenious ways to fly beneath Google’s anti-abuse radar, and new examples of bad ads leading to malware are still too common.
For example, a Google search earlier this week for the free graphic design program FreeCAD produced the following result, which shows that a “Sponsored” ad at the top of the search results is advertising the software available from freecad-us[.]org. Although this website claims to be the official FreeCAD website, that honor belongs to the result directly below — the legitimate freecad.org.
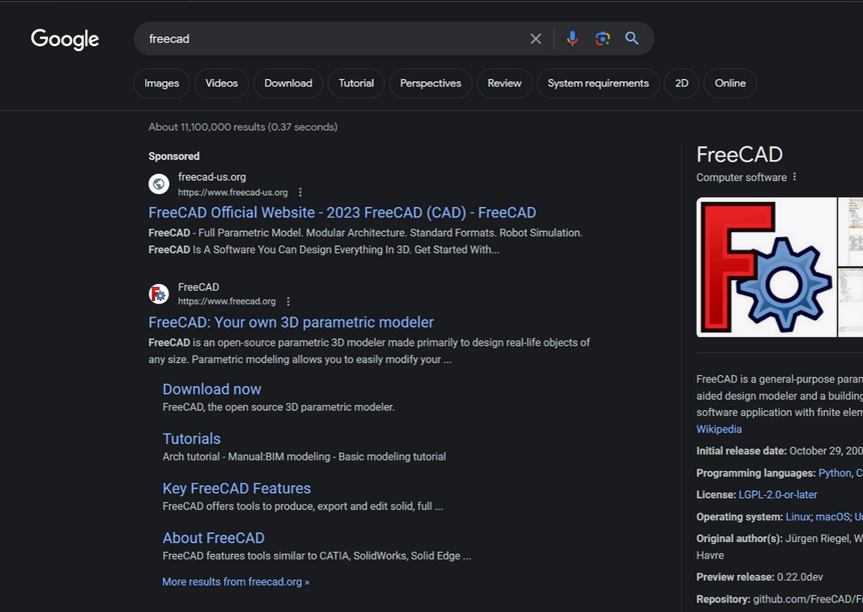
How do we know freecad-us[.]org is malicious? A review at DomainTools.com show this domain is the newest (registered Jan. 19, 2024) of more than 200 domains at the Internet address 93.190.143[.]252 that are confusingly similar to popular software titles, including dashlane-project[.]com, filezillasoft[.]com, keepermanager[.]com, and libreofficeproject[.]com.
Some of the domains at this Netherlands host appear to be little more than software review websites that steal content from established information sources in the IT world, including Gartner, PCWorld, Slashdot and TechRadar.
Other domains at 93.190.143[.]252 do serve actual software downloads, but none of them are likely to be malicious if one visits the sites through direct navigation. If one visits openai-project[.]org and downloads a copy of the popular Windows desktop management application Rainmeter, for example, the file that is downloaded has the same exact file signature as the real Rainmeter installer available from rainmeter.net.
But this is only a ruse, says Tom Hegel, principal threat researcher at the security firm Sentinel One. Hegel has been tracking these malicious domains for more than a year, and he said the seemingly benign software download sites will periodically turn evil, swapping out legitimate copies of popular software titles with backdoored versions that will allow cybercriminals to remotely commander the systems.
“They’re using automation to pull in fake content, and they’re rotating in and out of hosting malware,” Hegel said, noting that the malicious downloads may only be offered to visitors who come from specific geographic locations, like the United States. “In the malicious ad campaigns we’ve seen tied to this group, they would wait until the domains gain legitimacy on the search engines, and then flip the page for a day or so and then flip back.”
In February 2023, Hegel co-authored a report on this same network, which Sentinel One has dubbed MalVirt (a play on “malvertising”). They concluded that the surge in malicious ads spoofing various software products was directly responsible for a surge in malware infections from infostealer trojans like IcedID, Redline Stealer, Formbook and AuroraStealer.
Hegel noted that the spike in malicious software-themed ads came not long after Microsoft started blocking by default Office macros in documents downloaded from the Internet. He said the volume of the current malicious ad campaigns from this group appears to be relatively low compared to a year ago.
“It appears to be same campaign continuing,” Hegel said. “Last January, every Google search for ‘Autocad’ led to something bad. Now, it’s like they’re paying Google to get one out of every dozen of searches. My guess it’s still continuing because of the up-and-down [of the] domains hosting malware and then looking legitimate.”
Several of the websites at this Netherlands host (93.190.143[.]252) are currently blocked by Google’s Safebrowsing technology, and labeled with a conspicuous red warning saying the website will try to foist malware on visitors who ignore the warning and continue.
But it remains a mystery why Google has not similarly blocked more than 240+ other domains at this same host, or else removed them from its search index entirely. Especially considering there is nothing else but these domains hosted at that Netherlands IP address, and because they have all remained at that address for the past year.
In response to questions from KrebsOnSecurity, Google said maintaining a safe ads ecosystem and keeping malware off of its platforms is a priority across Google.
“Bad actors often employ sophisticated measures to conceal their identities and evade our policies and enforcement, sometimes showing Google one thing and users something else,” Google said in a written statement. “We’ve reviewed the ads in question, removed those that violated our policies, and suspended the associated accounts. We’ll continue to monitor and apply our protections.”
Google says it removed 5.2 billion ads in 2022, and restricted more than 4.3 billion ads and suspended over 6.7 million advertiser accounts. The company’s latest ad safety report says Google in 2022 blocked or removed 1.36 billion advertisements for violating its abuse policies.
Some of the domains referenced in this story were included in Sentinel One’s February 2023 report, but dozens more have been added since, such as those spoofing the official download sites for Corel Draw, Github Desktop, Roboform and Teamviewer.
This October 2023 report on the FreeCAD user forum came from a user who reported downloading a copy of the software from freecadsoft[.]com after seeing the site promoted at the top of a Google search result for “freecad.” Almost a month later, another FreeCAD user reported getting stung by the same scam.
“This got me,” FreeCAD forum user “Matterform” wrote on Nov. 19, 2023. “Please leave a report with Google so it can flag it. They paid Google for sponsored posts.”
Sentinel One’s report didn’t delve into the “who” behind this ongoing MalVirt campaign, and there are precious few clues that point to attribution. All of the domains in question were registered through webnic.cc, and several of them display a placeholder page saying the site is ready for content. Viewing the HTML source of these placeholder pages shows many of the hidden comments in the code are in Cyrillic.
Trying to track the crooks using Google’s Ad Transparency tools didn’t lead far. The ad transparency record for the malicious ad featuring freecad-us[.]org (in the screenshot above) shows that the advertising account used to pay for the ad has only run one previous ad through Google search: It advertised a wedding photography website in New Zealand.
The apparent owner of that photography website did not respond to requests for comment, but it’s also likely his Google advertising account was hacked and used to run these malicious ads.




The worlds largest advertising company is interested in clicks more than anything else. The search engine is a means to an end.
Because the search engine is a means to an end, it’s googles crown jewel. There is a huge financial interest in trying to keep the results clean; they don’t want users going to other search engines.
I am far from a google fan oy, but this is not at all an easy problem.Google is up against extremely highly motivated adversaries who have people every but as smart as Google engineers.
Crime is always a game of cat and mouse. Cyber-crime is just crime. We have never requested crime in the history of civilization.
I read Brian’s blog as information to use to prevent a false sense of security that could leave people far more vulnerable.
Google’s security team is probably working just as hard to secure their product as their marketing team is working to do much evil. That’s a lot of hard work.
If people think that Google’s security engineers are not by and large passionate about making the Internet a safer place, they have no clue.
Now let’s return to bashing Google for the sleaze they do deliberately perpetrate.
Shouldn’t Google be able to trace who paid for the ads? If these attackers are leaving legit sites (and ads?) up for weeks or months to gain legitimacy, I’d hope and expect they couldn’t do that with stolen cards.
Perhaps Google needs to be held to some past of banking’s “Know Your Customer” requirements?
This is a great point!!
Brian,
The URL for the REAL Rainmeter site is rainmeter.net not rainmeter.com (in paragraph 7).
Interesting. Does this also apply to ads on tpc.googlesyndication.com? Seems to try to communicate out to trackmenow.life which comes back to a google IP.
This is why I never click on ANY “sponsored” links.
Good reminder that you can’t be too careful.
No matter where I download software from, I always upload and check it using VirusTotal. I began screening everything (excluding automatically downloaded updates like Windows, of course) after coming across a couple of apps downloaded from official sites that VirusTotal red flagged based on their sandbox results. Max upload file size is currently 650 Mb. It’s not 100% but adds a layer of safety.
I also frequently use VirusTotal to check URLs.
Do remember that scanners on VirusTotal never say something is clean, they say undetected. There’s a huge difference.
My feel is that this is another example of convenient use by Google of 42 USC 230(c)’s free pass card. I’m a pro se litigant against Facebook over ads, so I’m a bit familiar. Plain and simple, they are not responsible for the content of the ads under 230(c), as long as they don’t create it themselves. They don’t even facilitate the download of malignant software because it isn’t hosted on Alphabet property (except rarely).
FREE is a dangerous word to search for online, especially if you download anything you intend to run. You click on something, it’s on you, and Google knows this. And remember with ‘free software’ miscreants only have to be lucky once. You have to be lucky every time…
Actually, 47 USC 230(c). Title 42 relates to public health, social welfare, and civil rights. Title 47 is Telecommunications. You might consider counsel that is actually familiar with law. Oddly enough, it doesn’t have to do with ads, but with “user-generated content.” Sure, ads aren’t created by Google, but there are additional causes of action/theories of recovery that apply to ads, and I’ve yet to hear of an ad on a platform being under 47 USC 230(c) or 47 USC 230 without the (c). Once again, your basis, understanding and conclusions are based on a misunderstanding of the law. With competent counsel …
A lot of these sites also use server side scripting, that if it detects the request came from google or any of the virus scanner sites, it will deliver a safe version always. then for all other sites it will randomly deliver the malware, to keep from triggering the blocks.
In light of the recent Krebs on Security article about ‘MalVertising’ and the risks of using Google search for finding software, I’d like to share an incident I experienced on January 8, 2024, that seems somewhat different. I clicked on a Google ad which displayed the URL ‘https://www.slack.com’, with all characters correct and no visible signs of deception. However, this led me to ‘https://slack.trialap.com’, a site not affiliated with Slack. This is intriguing because the article primarily highlighted issues with ads leading to malicious versions of software through fake but seemingly legitimate URLs. My experience seems different as the ad’s URL was exactly ‘slack.com’ but redirected elsewhere. Slack support confirmed ‘https://slack.trialap.com’ is not associated with them and their domain was not compromised. Does this situation represent a variation of ‘MalVertising’ that is more insidious than the examples cited in the article? How can users discern the legitimacy of such accurately labeled but misleading ads?
If in doubt, copy the URL to a plain text editor like notepad. Delete the hostname. Type in the hostname again manually, assuming it’s a host you know and trust. Then use the URL. Now you know the host is what it seems to be.
There might still be naughty strings in the rest of the URL, which might contain some sort of javascript attack. Especially if it is long and cryptic looking. The safest bet is to never use search result URLs, only use your own typing and your own bookmarks, and if necessary use the search on the host itself to find the page you’re looking for.
Even your own typing could contain a mistake, which sometimes leads to a host created with exactly that spelling mistake, for dishonest purposes. So the safest of all is to only use your own bookmarks, created after you have very carefully typed in each hostname only once. But few are willing to sacrifice that much convenience of course. Me neither.
I’m guessing posts with links are blocked as my previous post doesn’t show up.
I initially reported this IP with another domain name directly to the forum admins (not via forum post) on September 2nd.
At the time, the site was a blatant copy of the FreeCAD site, except the download link pulled in a malicious file from Discord.
My previous attempt to post included links to the VirusTotal analysis of the Discord download and the urlscan of the freecadocean DOT net site (still has the same IP mentioned in the article).