Researchers have successfully dismantled a massive ad fraud campaign they stumbled upon by accident.
The Satori Threat Intelligence and Research Team dubbed the campaign VASTFLUX, a portmanteau of “fast flux”—an evasion technique involving the constant changing of IP addresses behind a single domain—and “VAST” (Video Ad Serving Template), a framework to embed ads in videos. The researchers said they came across the VASTFLUX operation while investigating a different ad fraud scheme. While looking at the other scheme, they noticed an app creating an abnormally large number of requests using different app IDs.
Since then, they have studied the campaign in depth, uncovering its inner workings, before taking everything down.
VASTFLUX, up close
Satori researchers defined VASTFLUX as “a malvertising attack that injected malicious JavaScript code into digital ad creatives, allowing the fraudsters to stack numerous invisible video ad players behind one another and register ad views”. Its sophistication only mirrors the intimate knowledge its operators have of the digital advertising ecosystem.
Apparently, this campaign was an adaptation of an earlier ad fraud scheme called Matryoshka that made headlines in 2020. Researchers said VASTFLUX exploited apps that run ads, particularly on iOS. “More than 1,700 apps and 120 publishers were spoofed in the course of the operation, reaching a peak volume of 12 billion ad requests a day and impacting nearly 11 million devices,” they further said.
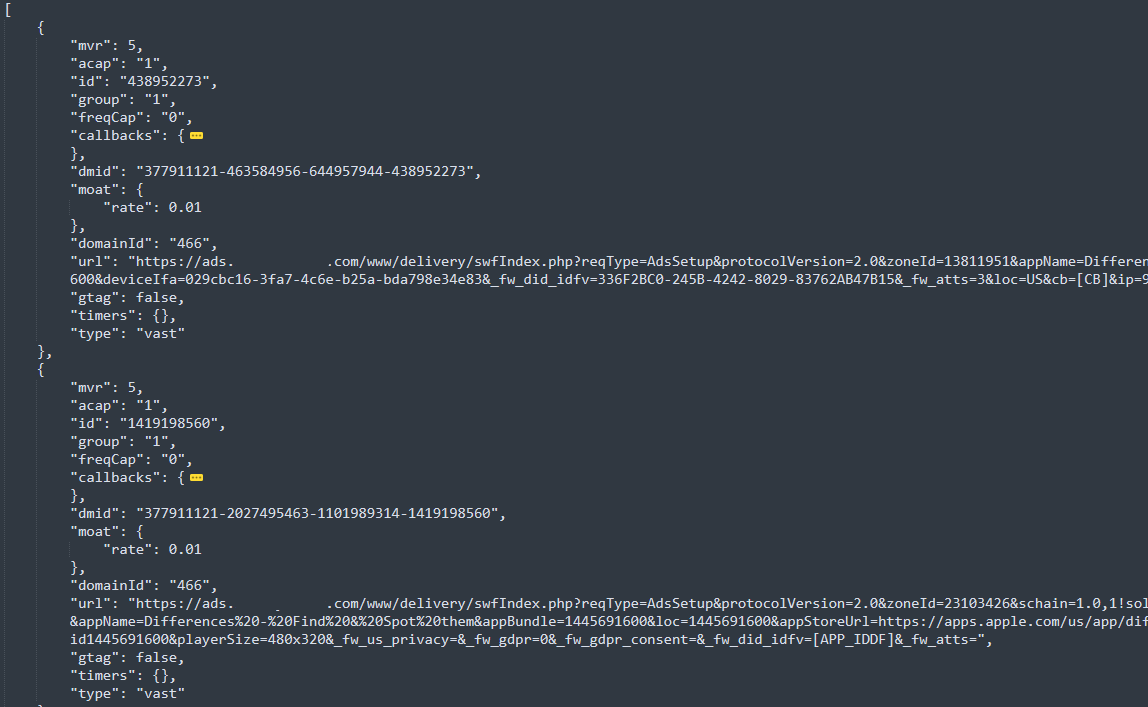
VASTFLUX begins with JavaScript (JS) injections into a static ad the operators issue. These scripts decrypt the encrypted ad configurations, which include a static banner image for the ad slot, a video ad player behind the banner image, and parameters for stacked video players. A script then calls home to its command-and-control (C2) server for additional information on what to place behind the static banner.
The researchers say VASTFLUX spoofs legitimate publisher and app IDs, including the size of the ads, and operators do it in a way that could easily be missed with cursory glances at the code. The code also contained masked instructions on what apps to spoof, how to spoof them, and how video players can be stacked up to play 25 streams with ads. These ads generate income, but the videos they play on are hidden behind a visible ad, rendering the video stack invisible to users.
As this video stack renders the ads simultaneously, they also “keep loading new ads until the ad slot with the malicious code is closed”.
“The URL of the VAST players are encoded in base64,” the researchers said. “When decoded, they show that each player has its own ‘playlist’ of ads to cycle through, each with its own URL with tracking code attached. It’s in this capacity that VASTFLUX behaves most like a botnet; when an ad slot is hijacked, it renders sequences of ads the user can’t see or interact with.”
VASTFLUX is very much capable of operating under fraud tracking schemes. It does this by avoiding using ad verification tags, which is a piece of technology that allows marketers to check whether their ads have been seen by real people or not. Since the real ads VASTFLUX runs are all out of sight with no tags to track them, the campaign appears virtually nonexistent.
The takedown
VASTFLUX’s takedown didn’t happen in one go. In fact, the Satori team carried out three waves of “distinct mitigation responses”, which all occurred between June and July 2022, before finally pulling the plug. The first resulted in a dramatic decrease in VASTFLUX’s traffic, but the operators adapted quickly. The second mitigation reduced 92 percent of the billions of requests the campaign sent at the peak of its operations. The third and final mitigation further blocked VASTFLUX’s activity.
The Satori team identified the operators behind this ad fraud scheme, but they didn’t name them. Working closely with fraud abuse organizations, VASTFLUX met the inevitable in December. “[B>id requests associated with VASTFLUX, which reached a peak of 12 billion requests per day, are now at zero,” the team proudly declared in their blog.
Because this ad fraud campaign particularly targets ad slots within apps, it is highly likely that legitimate apps would start showing VASTFLUX-related ads. That said, any or all iOS users may start experiencing the effects of having multiple videos playing in the background while using an app, such as device performance drops, battery drains quicker, and even overheating.
These are classic symptoms of adware infection, and if your device is experiencing one or more of these, be suspicious and try looking for which apps have caused these. Perhaps it’s time to start paying attention to how your device behaves. The researchers provided the following other red flags you should be looking out for:
- The device’s screen seems to turn on at unexpected times and without prompting, like in the middle of the night.
- An app suddenly slows down the performance of the device.
- Data use jumps dramatically from one day to the next.
- An app crashes frequently and without warning.
Stay safe!
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.