Apple accidentally approved one of the most popular Mac malware threats – OSX.Shlayer – as part of its security notarization process.
The Apple notary service is an automated system on recent macOS versions that scans software (ranging from macOS apps, kernel extensions, disk images and installer packages) for malicious content and checks for code-signing issues. Then, when a macOS user installs the software, Apple’s Gatekeeper security feature notifies them about whether any malicious code was detected before they open it.
Security researchers Peter Dantini and Patrick Wardle recently discovered that Apple inadvertently notarized malicious payloads that were utilized in a recent adware campaign.
“Unfortunately a system that promises trust, yet fails to deliver, may ultimately put users at more risk,” said Wardle in a Sunday analysis. “How so? If Mac users buy into Apple’s claims, they are likely to fully trust any and all notarized software. This is extremely problematic as known malicious software (such as OSX.Shlayer) is already (trivially?) gaining such notarization.”
On Friday, Dantini noticed that a website (homebrew[.]sh) was actively hosting an adware campaign. The website is likely spoofing the legitimate Homebrew site (hosted at brew.sh), a free and open-source software package management system that simplifies the installation of software on macOS.
https://twitter.com/PokeCaptain/status/1300440938301607939
When users visited the website, it redirected several times before telling them that their Adobe Flash Player is out of date and recommending an update (via at least three separate pop ups in the browser). While the campaign seems like a fairly run-of-the-mill adware attack, what’s different is that Apple’s notarization requirements do not trigger a warning notification telling the user that the developer cannot be verified, and that it is unknown whether the app is free from malware.
The adware payloads were fully notarized in this campaign, meaning the malicious payloads were submitted to Apple prior to distribution. They were scanned by the mobile giant and no malicious code was detected via Apple’s automated system.
 Upon further inspection, Wardle discovered that the notarized payloads appear to be OSX.Shlayer malware.
Upon further inspection, Wardle discovered that the notarized payloads appear to be OSX.Shlayer malware.
After running the payloads in an instrumented virtual machine captures, Wardle was able to discover the execution of various shell commands. These commands change file modes, execute and delete files, and more.
Shlayer is a top common threat for Macs — In fact, last year it made up 29 percent of all attacks on macOS devices in Kaspersky’s telemetry for 2019, making it the No. 1 Mac malware threat for the year. More recently, a new variant of the malware has been spotted actively using poisoned Google search results in order to find its victims.
After the malicious payloads were spotted, Wardle notified Apple, which revoked their certificates on Aug. 28. Then, on Aug. 30 (Sunday), the adware campaign was still live and serving up new notarized payloads.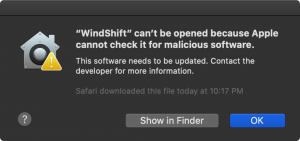
“Both the old and ‘new’ payload(s) appears to be nearly identical, containing OSX.Shlayer packaged with the Bundlore adware,” said Wardle. “However the attackers’ ability to agilely continue their attack (with other notarized payloads) is noteworthy. Clearly in the never-ending cat and mouse game between the attackers and Apple, the attackers are currently (still) winning.”
The Bundlore adware’s goal is generally to install various browser extensions and show victims various ads, Wardle told Threatpost. As of Monday, these newer notarized payloads were also revoked by Apple, Wardle told Threatpost.
“Malicious software constantly changes, and Apple’s notarization system helps us keep malware off the Mac and allow us to respond quickly when it’s discovered,” an Apple spokesperson told Threatpost. “Upon learning of this adware, we revoked the identified variant, disabled the developer account, and revoked the associated certificates. We thank the researchers for their assistance in keeping our users safe.”
On Wed Sept. 16 @ 2 PM ET: Learn the secrets to running a successful Bug Bounty Program. Resister today for this FREE Threatpost webinar “Five Essentials for Running a Successful Bug Bounty Program“. Hear from top Bug Bounty Program experts how to juggle public versus private programs and how to navigate the tricky terrain of managing Bug Hunters, disclosure policies and budgets. Join us Wednesday Sept. 16, 2-3 PM ET for this LIVE webinar.











