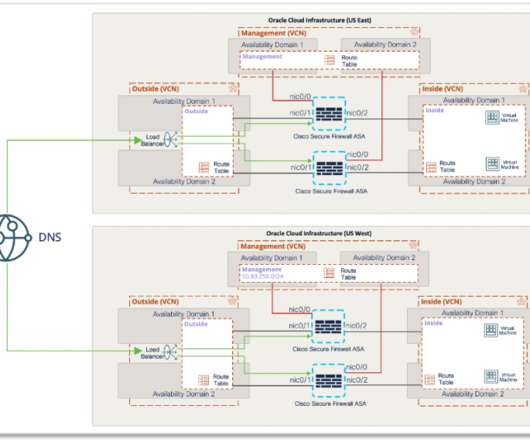
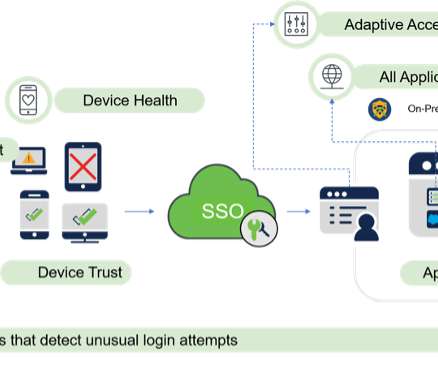
Zero Trust Architecture & Elements of Multi-Factor Authentication
Security Boulevard
SEPTEMBER 12, 2021
Multi-Factor Authentication (MFA) is a security method that requires more than one method of verification. The goal of MFA is to authenticate a user’s identity to assure the integrity of their digital transactions. The post Zero Trust Architecture & Elements of Multi-Factor Authentication first appeared on SecureFLO.














































Let's personalize your content