A host-based firewall is installed directly on individual networked devices to filter network traffic on a single device by inspecting both incoming and outgoing data. Larger enterprises use this to manage the spread of malware throughout a network in the event that one device is infected. Its goal is to establish a uniform security posture throughout the network and improve endpoint security by creating a protective barrier at the individual computer level.
Table of Contents
How Host-Based Firewalls Work
Organizations often adopt host-based firewalls for device-specific security control. These firewalls include six inherent functionalities encompassing direct-to-device installation, rule-based decision making, traffic monitoring, logging and reporting, rule set updates, and security suites integration.
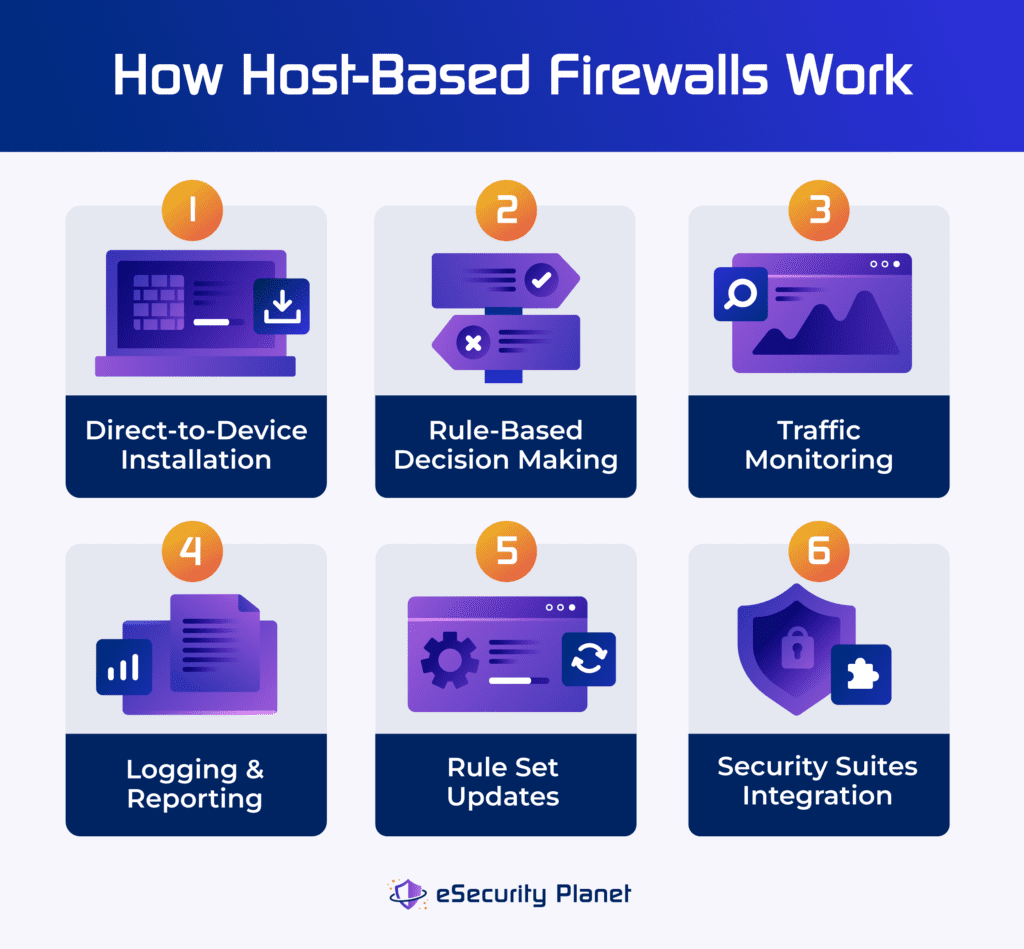
Here’s what each function entails:
- Installation design: Host-based firewalls are installed directly on individual devices such as computers, servers, routers, and switches. If it’s properly set up, it becomes an integral part of the device’s security infrastructure by monitoring and controlling traffic.
- Decision-making: Firewalls make autonomous decisions on whether to accept or prohibit each packet based on the created rules. This occurs quickly to provide minimal latency and is fundamental to a firewall’s role in filtering and controlling data traffic.
- Traffic monitoring: Firewalls continuously analyze the device’s incoming and outgoing network traffic, comparing data packets to established rules. Then, they filter potentially malicious or illegal network activities.
- Logging and reporting: Host-based firewalls keep track of authorized and rejected traffic, which helps with troubleshooting and security analysis. This capability assists post-event analysis, troubleshooting, and keeping an audit record of network activity.
- Automatic updates: Firewalls frequently receive automatic rule set updates to monitor emerging threats and provide protection against the most recent vulnerabilities.
- Integration with security suites: Host-based firewalls can be used with antivirus and other security technologies to provide layered protection against cyber attacks.
Host-based firewalls’ efficiency relies on proper setup and configuration across endpoints. They’re applied in certain use cases and have different advantages and disadvantages. To improve its effectiveness, determine the most appropriate firewall type and solutions for your organization’s demands.
When to Use Host-Based Firewalls
Host-based firewalls improve the security posture of individual devices, apps, or servers. They’re especially helpful when used strategically as part of a larger cybersecurity strategy that prioritizes seamless network functionality balanced with security, emergency solutions for vulnerable assets, individual device security outside the corporate network, and protection of sensitive data.
Adjusting for Seamless Network Functionality
Organizations often use host-based firewalls when specific network applications or services require open communication channels that aren’t allowed under default firewall settings. In other circumstances, users may need to carefully customize or temporarily disable their host-based firewalls to enable seamless network functionality for certain applications.
Strengthening Layers of Security Upstream
Host-based firewalls typically work with an additional layer of security positioned “upstream” in the network, like a stronger network firewall or a secure web gateway. They serve as part of a multi-layered security strategy, enhancing effectiveness when integrated into a comprehensive security at higher levels of the network architecture. Regular assessments, modifications, and security measures help create a comprehensive, multi-layered security plan.
Providing Emergency Solutions for Vulnerable Assets
Host-based firewalls can act as an emergency measure to safeguard your most sensitive assets until a more complete security solution, such as network-based firewalls or endpoint detection and response (EDR), is implemented. This offers a rapid and effective security measure for your critical assets.
Securing an Individual Device Outside the Corporate Network
Host-based firewalls give an extra layer of security in situations where individual devices may be vulnerable to attacks, especially when used outside of the corporate network. They monitor and handle traffic specific to each device, ensuring protection regardless of network security.
Protecting Sensitive Data on Limited Devices
Consider adopting host-based firewalls if you have a small number of devices, servers, or applications that handle sensitive data. Host-based firewalls provide an extra layer of defense, allowing you to apply tight rules and configurations tailored to these assets.
How to Set Up a Host-Based Firewall Across All Endpoints
To install a host-based firewall across all endpoints, choose your firewall solution first, then develop a firewall policy. Deploy the firewalls across all endpoints, configure default rules, create specific application rules, enforce the principle of least privilege, test and document rule changes, and employ endpoint protection solutions. Lastly, monitor and update your rules, conduct audits, and train users regularly.
Identify a Suitable Firewall Solution
Choose the best-fit firewall solution for your network, whether it be the operating system’s built-in firewall (like Windows Firewall, iptables on Linux, or pf on BSD) or a third-party firewall. Consider centralized management, budget, and trial versions to ensure that the solution you select meets your network’s specific needs and limits. Verify documentation and support for a smooth deployment and ongoing operations.
Develop a Firewall Policy
Create a comprehensive firewall policy that’s customized to your organization and includes rules and configurations for inbound and outgoing traffic. To do this, state the policy’s purpose, scope, definitions, and exceptions and change guidelines. Next, define your policies and processes, compliance guidelines, documentation, and violations and penalties. Lastly, plan the policy’s dissemination.
For the full steps and a template to start with, read our article on how to develop a firewall policy.
Deploy Firewalls on Endpoints
Install firewall software or enable built-in capabilities on every network endpoint to implement your selected firewall solution. Administrators on Windows can use Group Policy Management to centrally manage host firewalls, providing identical settings across all endpoints. MacOS users require proprietary software, such as Mobile Device Management, to regularly implement host-based firewall settings. Next, proceed with the steps below to effectively deploy firewalls.
Configure Default Rules
Create default rules to set a basic security posture for all endpoints, such as disabling unnecessary services, limiting port access, and denying unauthorized traffic. Modern host-based firewalls can distinguish between internal and external networks, facilitating customized security rules.
For example, intra-subnet traffic may be restricted internally, while a public network connection restricts activity to HTTP/HTTPS, necessitating the use of a VPN for additional access. Host-based firewalls can use binary libraries to detect and prevent future exploitation attempts. Setting up warnings for irregular binary use indicates potential security threats and warrants more investigation.
Create Specific Application Rules
Host-based firewalls let users define particular application rules that manage how individual programs or services interact with the network. Configure these rules to determine how each program behaves and which network activities are allowed or restricted. This fine-grained control guarantees that each application follows preset parameters. It offers a targeted approach to managing network traffic.
Enforce the Least Privilege Principle
Follow the concept of least privilege by allowing only essential traffic. Limit inbound and outbound connections to the minimum required for business activities, and deny endpoint access to server environments and administrator dashboards. Prioritize safeguarding high-yield ports against potential hacker exploits, allowing only a few workstations access while blocking all others.
Test & Document Rule Modifications
Develop particular test scenarios that simulate real-world network usage, including a variety of apps and services. Create appropriate test cases and prioritize critical services for continuous functionality. Simulate probable security risks to determine the firewall’s responsiveness and efficacy in preventing unauthorized access. During testing, keep an eye on the firewall logs to look for any unusual blocks or anomalies.
Verify the sequence and prioritization of rules, testing across many networks to adjust for differences. Simulate user behavior to check if the firewall permits necessary actions without interference. Evaluate the effects of rule modifications on network performance and user experience. Then, document the results, noting any concerns or changes needed, and make the necessary changes to improve security without jeopardizing key services.
Employ Endpoint Protection Solutions
For comprehensive security, combine firewall measures with endpoint protection solutions like antivirus software and intrusion detection/prevention systems (IDPS). Antivirus software checks files, emails, and apps for known malware signatures and behavioral anomalies, providing an extra layer of protection over typical firewall capabilities.
IDS constantly scans network or system traffic for unexpected patterns or known attack signatures. When potential risks are found, the IDS sends out alerts or notifications, prompting additional research. IPS can automatically carry out predetermined actions, such as blocking malicious IP addresses or terminating suspicious connections. IPS aggressively mitigates and responds to security occurrences in order to protect the host system from potential harm.
Monitor & Update Any Changes
Review firewall logs on a regular basis via the administrative interface to identify recorded events and potential security problems. Identify any irregularities or patterns that may suggest unauthorized access or suspicious activity. Evaluate the effectiveness of existing firewall rules in preventing security events and adjust rules as needed depending on the results.
Consider changes to applications and network architecture, align rules with organizational security standards, and document any changes for a comprehensive audit trail. If desired, automate rule modifications to ensure prompt responses to emerging threats. For long-term network security, test the effectiveness of changed rules and develop a regular monitoring and updating plan.
Audit & Review Firewall Configurations
Conduct frequent audits by accessing the firewall configuration settings and assessing the effectiveness of current rules. Identify any misconfigurations, confirm compliance with organizational security rules, and handle any network infrastructure modifications. Evaluate application access rules, taking into account new or changed apps, and document audit findings for future reference.
Update firewall configurations depending on the results to improve security and compliance. Collaborate with the IT team to address complicated issues, and set up a regular audit schedule to keep the network up to date and safe.
Train Users
Initiate end-user education on host-based firewalls with basic firewall concepts, installation, and rule setup. Demonstrate how to understand firewall logs, respond to alerts, and use safe browsing techniques. Then, run simulated scenarios, reinforce corporate policies, and teach users about upgrading settings and regular maintenance. Conduct interactive training sessions, assess their knowledge after training, and solicit feedback for improvement.
Consider Optional Steps
Some additional ways to strengthen your organization’s firewall configuration procedure include:
- Choose a centralized management solution: Consider using a centralized administration system to deploy and manage firewalls on all endpoints. Some firewall solutions provide centralized admin consoles for easier configuration and monitoring.
- Implement network segmentation: Try utilizing network segmentation to create different security zones within your network. This helps to prevent potential security breaches and enables more granular firewall rule control.
- Automate firewall updates: If possible, look into automation techniques for updating firewall rules across all endpoints. Automated updates can help to ensure consistency and efficiency when maintaining security configurations.
To determine whether you need to follow these optional steps, consider your network’s size and complexity, your available resources, the need for granular control, and your organization’s overall security policy.
7 Advantages of Host-Based Firewalls
Host-based firewalls come with several key benefits, including comprehensive network security, customization, mobile device protection, adaptability across various device types, effectiveness against specific attacks, and additional protection in the event of primary firewall failure.
Enhanced Security for the Entire Network
A host-based firewall improves not only the security of the device it’s placed on, but also the overall security of the network it’s linked to. It prevents malicious apps from spreading to other networked devices, thus providing comprehensive security.
Easy Customization
Host-based firewalls are highly customizable, allowing a single device to host several firewalls with different configurations for various types of security. This flexibility helps users adjust security measures to their own needs or preferences.
Mobile Compatibility
When users are on the move, a company’s network firewall may not protect their mobile devices. Host-based firewalls close this gap, providing continuous security for mobile devices regardless of their location.
Customizable Security Rules
Users can modify security rules to their individual needs. This customization delivers a more targeted and effective approach to security by matching firewall settings with the device or user’s specific requirements.
Versatility Across Device Types
Host-based firewalls protect any device that connects to the internet, making them useful for securing many kinds of devices such as PCs, laptops, servers, and other connected devices.
Effectiveness Against Certain Attacks
When it comes to stopping specific sorts of threats, host-based firewalls can outperform network-based firewalls. Their ability to focus on particular devices enables more detailed defense against attackers that target specific weaknesses.
Protection Against Firewall Failure & Simplicity
Host-based firewalls offer additional protection in the event of a primary firewall failure. Having numerous firewalls of different designs reduces the likelihood of a primary firewall failure. Furthermore, configuring a host-based firewall is often simpler than configuring a perimeter firewall, which reduces complexity and allows for faster rule set verification.
5 Disadvantages of Host-Based Firewalls
While they offer plenty of advantages, host-based firewalls also pose challenges. They may entail a complex unified changes rollout across devices, lack powerful logging capabilities, carry the risk of blocking legitimate traffic if misconfigured, demand tailored configuration per device, and offer limited protection for offline devices due to their reliance on real-time internet monitoring.
Complex Unified Changes Rollout
Host-based firewalls contain specific configurations for each device, making it difficult to deploy consistent modifications across the organization. Unlike network firewalls, which may be configured centrally and affect all connected users, host-based firewalls require tailored configurations.
Weak Logging Capacity
Host-based firewalls have less powerful logging features than network firewalls. This constraint makes it difficult to track and analyze security occurrences properly. Furthermore, loggings may be insufficient to detect advanced attacks, making it easier for such attacks to sneak through the firewall undetected.
Potential to Block Legitimate Traffic
If not properly configured, host-based firewalls might block genuine traffic, causing disruptions in normal operations. This risk originates from the personalization of settings for each device, emphasizing the significance of proper configuration to avoid unintentionally blocking vital network activity.
Need for Tailored Configuration Per Device
Host-based firewalls need individualized setup and adjustments for each device, which can be time-consuming, complex, and error-prone, especially if you’re not familiar with the centralized management approach. This tailored configuration raises administrative costs, particularly in large firms with several devices.
Limited Protection for Offline Devices
Because their efficiency is dependent on network traffic monitoring, devices that aren’t connected to the internet may lack the firewall’s real-time security. This shortcoming makes it difficult to guarantee device security in offline or isolated contexts.
4 Best Host-Based Firewall Solutions
Most modern operating systems feature built-in firewall software, which reduces human error; however, host firewalls are improving with increased manageability. Some of the most accessible host-based firewall solutions on the market are Windows Firewall, Little Snitch, Glasswire, and ZoneAlarm.
Windows Firewall
Windows Firewall, a built-in security feature included by default in all Windows OS, is ideal for Windows users who need a built-in, adaptable solution. It provides network traffic filtering based on IP addresses, protocols, and port numbers, with the option to block or allow traffic for certain applications. When paired with IPsec, it enables authentication for secure communication and Network Location Awareness, hence improving defense against potential attacks.
Little Snitch
Little Snitch is an ideal choice for macOS users who want granular control over their network connections at the application level. Users can choose restrictions or allow specific applications to access the internet. Additionally, the firewall generates real-time alerts for new connection attempts, giving users complete control over their network traffic on a MacOS system and improving overall network security. Price starts at $52 for a single license.

Glasswire
Glasswire is a good choice for users seeking firewall solutions with both free and paid options. The free edition, which supports two PCs, is appropriate for individuals with basic requirements. Premium versions, which cost $2.99+ per month, are available for customers who want more capabilities and the ability to monitor and operate many faraway PCs at the same time, making it ideal for both casual and advanced users.

ZoneAlarm by Check Point
ZoneAlarm Free Firewall is a no-cost firewall solution tailored specifically for Windows 11, 10, and 7 users. It acts as a barrier, monitoring and filtering both incoming and outgoing information to prevent malware and cyber threats. With two-way protection, it shields PCs from hackers and avoids spyware exposure. It’s regarded as one of the world’s top free firewalls, making it a great alternative for those looking for strong security measures on Windows systems.

Firewalls Comparison: Host vs Network vs Application
Firewalls come in various types, each catering to specific functions. Host-based firewalls work at the device level, protecting specific PCs. Network-based firewalls serve as network perimeter defenses, protecting the entire network from threats. Application-based firewalls regulate specific application communications and provide granular control over certain applications, such as web traffic, for targeted protection.
Here’s how host-based, network-based, and application-based firewalls differ:
| Host-Based Firewall | Network-Based Firewall | Application-Based Firewall | |
|---|---|---|---|
| Functions | Software-based, 2nd line of defense | Hardware-based, network perimeter, can be deployed as virtual machines | Often near application servers |
| Mobility | Mobile-friendly | Can’t be moved until LAN is migrated | Flexible deployment |
| Protection | Internal security | Strong network defense | Targeted protection for specific apps |
| Maintenance | Less centralized management, more labor-intensive to change | Depends upon firewall manager, less device to manage | More centralized and software-based management, may require more regular adjustments |
| Scalability | Based on capabilities of the network card and computer memory | Easily scalable if software-based, hardware faces rigid limits | Depends on deployment |
| Skillset | Needs basic hardware or software skills | Needs highly skilled setup | Needs expertise in specific applications/protocols |
| Cost | Cost-effective for small units | Potentially more expensive to deploy, but cost is distributed over large number of users | Varies based on specialization and features |
Organizations commonly deploy different types of firewalls to address threats at various levels. Ultimately, the choice between host-based, network-based, and application-based firewalls depends on your unique priorities and protection requirements.
Bottom Line: Enhance Network Security via Host-Based Firewalls
Host-based firewalls installed on certain devices improve internal network security while complementing network firewalls. These firewalls act as effective security controls and communication protection solutions for the same VLAN, resulting in a layered security strategy. Do a proper configuration, update your firewall configurations regularly, and train users to optimize firewall performance and network security.
A host-based firewall contributes to network security, but understanding the appropriate firewall type and additional security solutions strengthens your overall security strategy.







