Attack surface management (ASM) is a relatively new cybersecurity technology that combines elements of vulnerability management and asset discovery with the automation capabilities of breach and attack simulation (BAS) and applies them to an organization’s entire IT environment, from networks to the cloud.
That makes ASM’s ambitions much greater than legacy vulnerability management tools. Attack surface management aims to automate the process of discovering, assessing, and prioritizing vulnerabilities and third-party, digital supply chain, and cloud risks. It addresses both internal and external (EASM) risks. CAASM (cyber asset ASM) and DRPS (digital risk protection) are also related terms and elements of ASM.
Here are our seven picks for the early leaders in the attack surface management market:
- CyCognito: Best for uncovering attack vectors
- Google Cloud Security by Mandiant: Best for identifying and managing your external attack surface
- Palo Alto Cortex Xpanse: Best for continuous monitoring and managing surface attacks
- Microsoft Defender: Best external surface defense tool
- CrowdStrike Falcon Surface: Best cloud-based ASM solution
- Tenable: Best for external attack surface management
- IBM Randori: Best for attack surface simulation and testing
Top Attack Surface Management Software Comparison
Here is a comparison of the top attack surface management tools, followed by in-depth reviews.
| Asset Discovery | Reporting | Integrations | Certifications | Pricing | |
|---|---|---|---|---|---|
| CyCognito | Dynamic asset inventory, natural language processing, advanced analysis of open-source intelligence (OSINT) | Attack Vector Reports | Zendesk, Microsoft 365, Azure, Excel, Outlook, Google, Sheets, Gmail, Slack, AWS, PagerDuty, Okta | Member of Cloud Security Alliance (CSA) and OWASP | Starts at $11 per asset or $30,000 per year |
| Google Mandiant Cloud Security | Infrastructure-as-code (IaC) templates, virtual machines (VMs), containers, and storage buckets | Asset Inventory, Vulnerability Reporting, Compliance Reporting | Google Cloud Security Command Center (SCC), Google Cloud Identity and Access Management (IAM), Google Cloud Key Management Service (KMS) | ISO/IEC 27001, SOC 2 Type II | Free trial to start |
| Palo Alto Cortex Xpanse | Internet-facing asset discovery and dynamic port/service monitoring features | Report Center found in their platform | Prisma Cloud, Cortex XSOAR | CSA Labs | $95,000/unit per annum |
| Microsoft Defender | Build my Attack Surface feature on the dashboard | 4 built-in Microsoft Defender EASM inventory reports in Azure: Attack Surface SummarySecurity PostureGDPR ComplianceOWASP Top 10 | Microsoft 365, Microsoft 365 Defender, Microsoft Sentinel, Microsoft Defender for Cloud, Azure, Windows, Office 365, Dynamic 365 | N/A | 30-day free trial, then $0.011 asset/day after trial ends |
| CrowdStrike Falcon Surface | AI-powered attack surface analytics | Custom data generated reports within the platform | CrowdStrike Platforms, Slack, Jira, ServiceNow | NSA-CIRA | $299.95 – $924.95 per year |
| Tenable | Tenable One, an exposure management platform | Identifies assets using DNS records, IP addresses, and ASN, and provides over 180 metadata fields | Tenable Attack Surface Management, Add-on for Splunk | ISO/IEC 27001/27002 | $5,290 – $15,076.50 per year |
| IBM Security Randori | Center-of-mass-out approach | Discovery Path within the platform | Splunk Enterprises, ServiceNow, Axonius, Rapid7 InsightIDR, Panaseer, Qualys Cloud Platform, IBM Security QRadar, Splunk Phantom, Tenable, LogicHub | N/A | Free 7-day trial |
Table of Contents

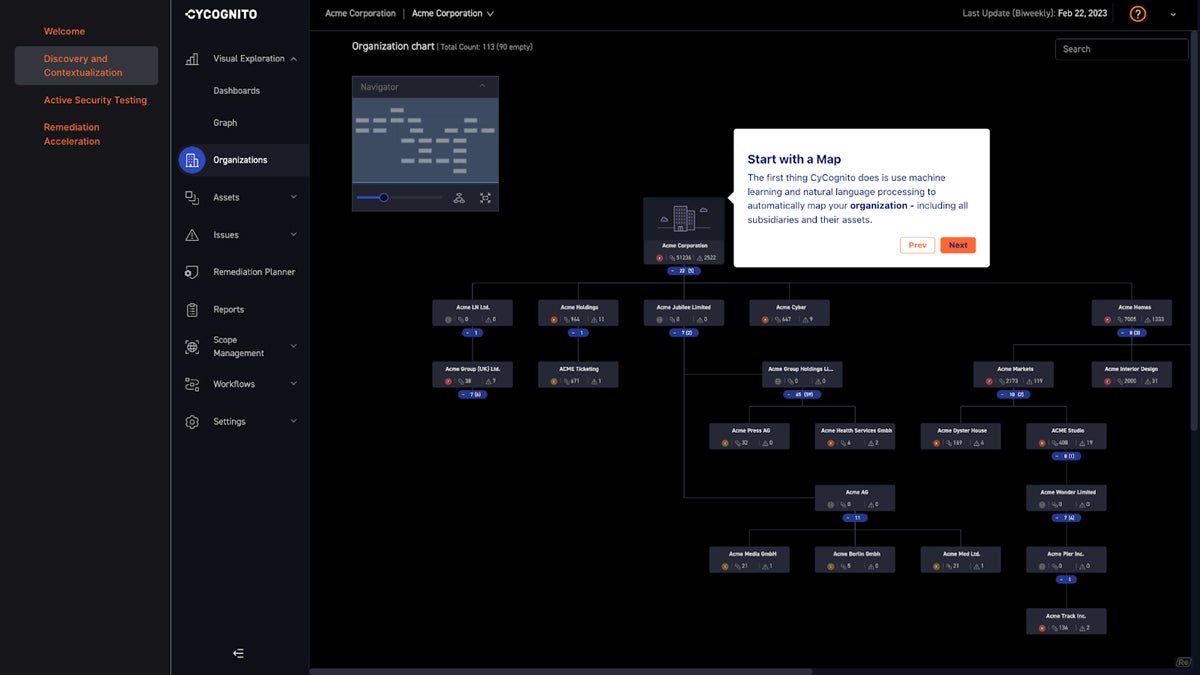
CyCognito
Best for Uncovering Attack Vectors
CyCognito excels at finding concealed attack routes by modeling adversary tactics, techniques, and procedures (TTPs). It creates a comprehensive picture of your attack surface, including assets that typical security solutions can’t see. Its technology specializes in managing the attack surface by recognizing, prioritizing, and removing external security issues. CyCognito also provides information on a company’s digital footprint, including unknown and shadow IT assets.
Pricing
Through its SaaS architecture, CyCognito provides tiered pricing for security testing, intelligence, and premium support. Pricing is dependent on the quantity of Internet-facing assets.
- Starts at $11 per asset per month
- The entire expense for a 12-month commitment is $30,000
- A 24-month package is offered for $60,000 in total
- Businesses can choose a 36-month package for $80,000 in total
Features
- Zero-input discovery
- Contextualization
- Security testing
- Prioritization
- Remediation acceleration
Pros
- Comprehensive visibility
- Automation features
- Real-time threat intelligence
- Risk prioritization
- User-friendly
- Compliance support
Cons
- Can generate false positives
- Limited to external threats
- Effectiveness depends on regular vulnerability database updates

Mandiant Attack Surface Management
Best for Identifying and Managing External Attack Surfaces
Mandiant Attack Surface Management (ASMS) is a cloud-based solution that helps organizations identify, assess, and manage their external attack surface. Google-owned Mandiant provides a comprehensive view of all internet-facing assets, including public-facing websites, subdomains, cloud resources, and third-party assets. ASMS also provides insights into the risks associated with each asset and how to mitigate them.
Pricing
Mandiant Attack Surface Management doesn’t reveal pricing, but a free trial is available on their signup page.
Features
- Continuous exposure monitoring
- Operationalize expertise and intelligence
- Assess high-velocity exploit impact
- Identify unsanctioned resources
- Digital supply chain monitoring
- Subsidiary monitoring
Pros
- Accurate IOCs
- Easy API integration
- In-depth vulnerability understanding
- Optimized threat intelligence
- Quick reporting of zero-day vulnerabilities
Cons
- Needs adjustments in feeds according to threat profiling, requiring ongoing attention
- Support response delays
- Complex architecture during implementation and in the system’s architecture


Palo Alto Cortex Xpanse
Best for Continuous Monitoring and Managing Surface Attacks
Palo Alto Cortex Xpanse is best for continuously monitoring and managing your attack surface. It provides a real-time view of assets and the risks associated with them. Cortex Xpanse also provides insights into how attackers are targeting your organization and how to defend against them.
Pricing
- Palo Alto Cortex Expander web-based subscription platform covers 999 AUM and Basic Customer Success support, all for an annual price of $95,000 per unit.
Features
- Addresses security blindspots
- Helps eliminate shadow cloud
- Improves zero-day response
- Merger and acquisition (M&A) evaluation
- Scalable across environments
Pros
- Cloud-based and highly scalable, catering to the needs of large enterprises
- Behavior alert functionality
- Detailed reports allow drilling down into vulnerabilities, with information on severity and likelihood of exploitation
- Highly intuitive UI, making it easy to access and understand information
- Works across cloud, hybrid, and on-premise environments, ensuring comprehensive security coverage
Cons
- SIEM tool integration challenges reported
- Cloud-based nature affects performance on certain browsers
- Depth of visibility into attack chains is limited
- Additional licensing may be required
Microsoft Defender
Best for External Surface Defense
Microsoft Defender is best for organizations that are already using Microsoft security solutions. It offers an all-encompassing attack surface management solution connected with other Microsoft security solutions. In addition, Microsoft Defender integrates seamlessly with the larger Microsoft ecosystem, allowing enterprises to capitalize on synergies across several platforms and apps. This integrated strategy improves overall security by enabling more efficient threat detection, response, and repair operations.
Pricing
- Microsoft Representative – $0.011 asset/day
- Azure Portal – $0.011 asset/day
Features
- Real-time inventory
- Exposure detection and prioritization
- More secure management for each resource
Pros
- Microsoft Defender External Attack Surface Management takes a proactive approach to controlling external attack surfaces, allowing businesses to keep ahead of possible attacks
- Automates asset discovery by searching the internet and network, resulting in a list of actionable items for InfoSec and Infrastructure teams
- Multicloud view and threat intelligence
- Real-time protection and integration
Cons
- Limited to the Microsoft ecosystem
- Users struggle with customization and a complicated interface
- The tool may generate false positives, necessitating manual verification, and it extensively relies on automation, resulting in occasional failures
- Requires Microsoft Defender for Endpoint subscription and can have integration issues with legacy systems


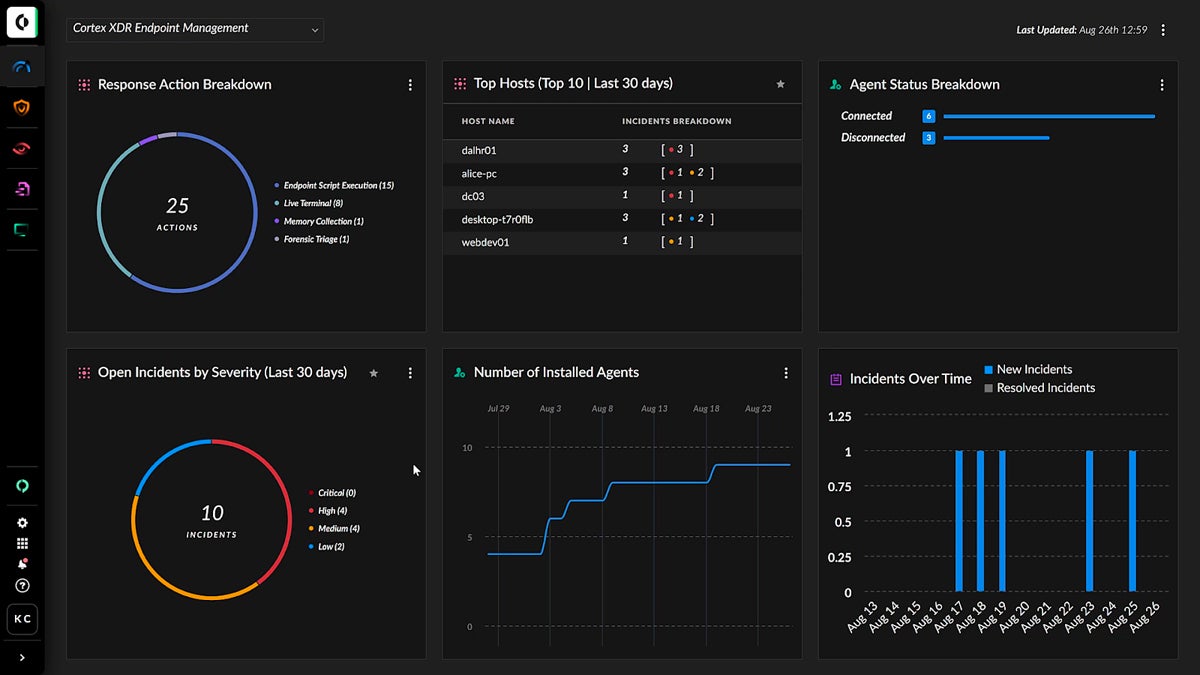
CrowdStrike Falcon Surface
Best Cloud-Based ASM Solution
CrowdStrike Falcon Surface is ideal for businesses seeking a cloud-based attack surface management solution. It gives you a complete picture of your attack surface, encompassing assets on-premises, in the cloud, and in hybrid settings. Integration with the Falcon platform also makes it ideal for existing CrowdStrike customers.
Pricing
- CrowdStrike Falcon Surface pricing is offered within CrowdStrike’s Falcon Bundles. Falcon Go is at $299.95 per year, Falcon Pro is at $499.95 per year, and Falcon Business is at $924.95 per year. Falcon Enterprise’s price is upon request.
Features
- Adversarial-based risk prioritization
- Guided remediation
- AI-powered analytics identify critical exposures
- Asset discovery
Pros
- Leverages cloud and AI-based technology
- Customized threat detection
- Covers wide range of devices and operating systems
- Custom reports
- Accuracy in uncovering risks
Cons
- Can be expensive for SMBs
- Requires high-speed internet due to its cloud-based service
- Interface can be complex for beginners


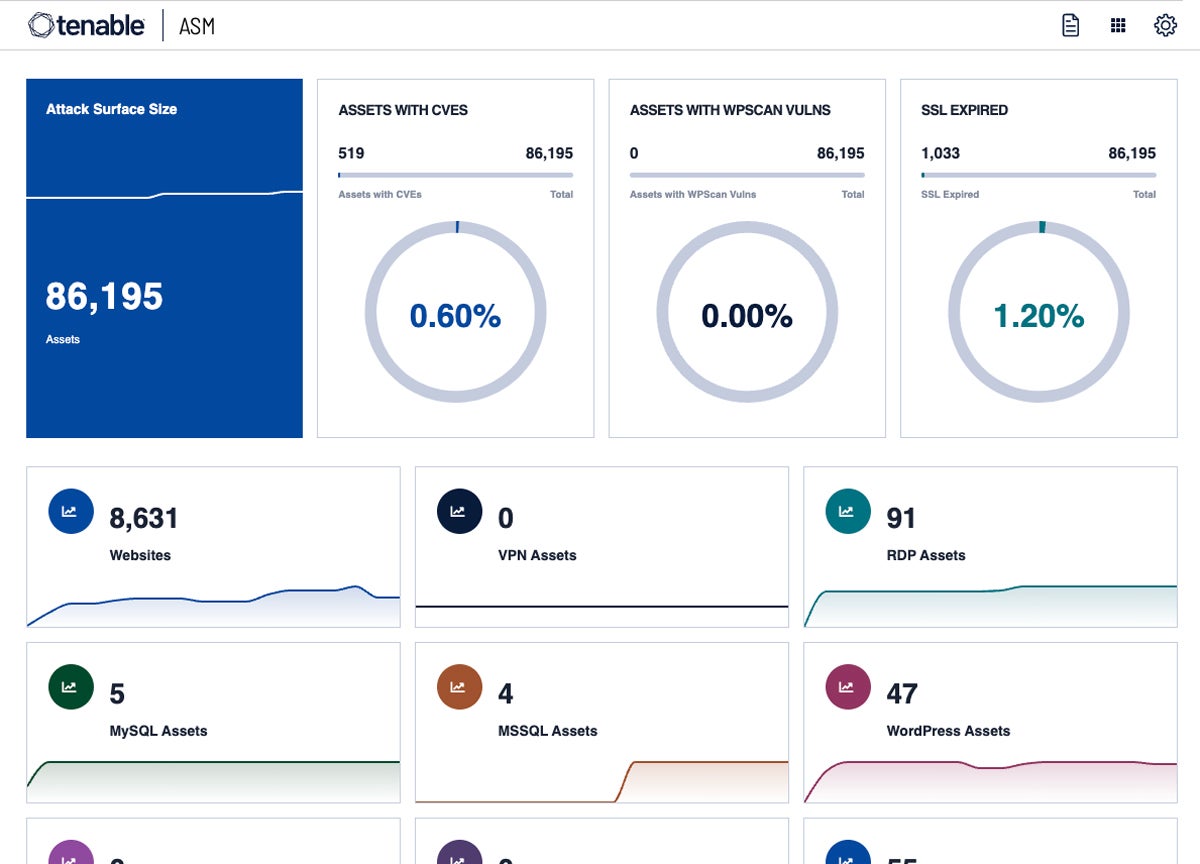
Tenable Attack Surface Management
Best for External Attack Surface Management
Tenable Attack Surface Management continuously maps the environment and discovers connections to internet-facing assets, allowing you to quickly identify and analyze the security posture of your entire external attack surface. Its continuous mapping and monitoring capabilities give real-time data so you can stay ahead of new threats and make educated defensive decisions. Tenable helps you analyze the present security posture and also execute proactive steps that increase your overall resilience against external attacks by providing complete insight into internet-facing assets and their interconnections.
Pricing
- 1 Year – $5,290
- 2 Years – $10,315.50 (Save $264.50)
- 3 Years – $15,076.50 (Save $793.50)
Features
- Advanced technology fingerprinting identifying common vulnerabilities and exposures (CVEs)
- Thousands of software versions
- Geolocation
- Programming frameworks
- Continuous dynamic data refreshes
- Attack surface change alerts
Pros
- Maps externally visible infrastructure and keeps this info up to date
- Can show scan findings in its Business Context to aid in management reporting
- Very good asset management
- Strong vulnerability scanning engine
Cons
- Takes time to get used to navigating the platform
- Some filters can be hard to find
- You may need to pay for additional components for full visibility across your tech surface

IBM Security Randori
Best for Attack Surface Simulation and Testing
IBM Security Randori is a cloud-based attack surface management tool that assists businesses in identifying and mitigating security flaws. Randori employs a novel technique to attack surface management the company calls adversary simulation. Adversary simulation includes mimicking an attacker’s behavior in order to find security flaws that might be exploited.
Pricing
- IBM Security Randori doesn’t publicly display their ASM pricing. But they offer a 7-day free trial, which you can access through their website.
Features
- External reconnaissance
- Discovery path
- Risk-based prioritization
- Remediance guidance
- M&A risk management
- Shadow IT discovery
Pros
- Comes with a target temptation tool that users give high marks to
- Continuous perimeter monitoring for external cyberattacks in real time
- Helps identify blind spots and obsolete assets
Cons
- Doesn’t have an email alert for updates and upgrade recommendations
- Not all defensive tools are available globally
Key Features of Attack Surface Management Software
Features and capabilities can vary in the emerging attack surface management market, but here are some essential features to look for in ASM solutions:
- Asset discovery: Safeguard assets housed on partner or third-party sites, cloud workloads, IoT devices, abandoned or deprecated IP addresses and credentials, Shadow IT, and more.
- Business context and importance of an asset: Once assets have been discovered, you must assess their business context and importance. This will help organizations prioritize their remediation efforts and focus on the assets that are most critical.
- Continuous risk assessment: Assessing vulnerabilities, misconfigurations, data exposures, and other security gaps is constantly changing as new assets are added, vulnerabilities are discovered, and misconfigurations are introduced. Continuous risk assessment helps organizations identify and address risks as soon as they emerge.
- Prioritization: Once risks have been identified, it’s important to prioritize them based on the likelihood of exploit and the potential impact on the business.
- Remediation plan: A thorough remediation plan is critical for minimizing identified risks and strengthening an organization’s cybersecurity posture. It provides a strategy roadmap that is adapted to the organization’s issues, guaranteeing focused and proactive efforts to counter potential risks.
- Validating fixes: Once fixes have been implemented, the next step is to test them to ensure they are effective.
- Reporting: Attack surface management requires regular reporting to help organizations track their progress in reducing risk and identify areas for improvement.
- Integration with SIEM, ITSM, and CMDB: Other security solutions, such as security information and event management (SIEM) systems, IT service management (ITSM) systems, and configuration management databases (CMDBs), should be integrated with attack surface management solutions. This integration assists enterprises in streamlining their security operations and improving the efficacy of their attack surface management program.
How to Choose the Best Attack Surface Management Software for Your Business
When choosing an attack surface management software for your organization, look for one that offers a comprehensive view of your environment and continuous monitoring, provides insight into risks, integrates with your existing infrastructure, and is scalable. Here are some of the issues for potential buyers to consider.
- The size and complexity of your attack surface: The sophistication and functionality required in an attack surface management system are determined by the size and complexity of your attack surface. If your attack surface is broad and complicated, you’ll need a solution that can find and analyze all of your assets, including known and unknown assets, third-party assets, and cloud assets.
- Your security budget: Attack surface management software can cost thousands to tens of thousands of dollars each year. Be sure to select a solution that matches both your budget and your security requirements.
- Your existing security infrastructure: If you currently have a lot of security solutions in place, you will need to select an attack surface management solution that interfaces with your existing infrastructure. This will assist you in streamlining your security operations and avoiding redundant work.
- Your risk tolerance: The amount of security you require from an attack surface management system is determined by your risk tolerance. You may be able to pick a less expensive option with fewer features if you have a high-risk tolerance. If your risk tolerance is low, you may need to pick a more expensive option with additional features.
- Your individual/business requirements: In addition to the broad considerations indicated above, you should consider your specific requirements when selecting an attack surface management system. If you work in a regulated business, for example, you may need to select a solution that is certified to satisfy certain compliance criteria.
How We Evaluated Attack Surface Management Software
For our analysis of the attack surface management product market, we gave the highest weight to product capabilities, as ASM is a technology that requires broad reach and functionality. Other considerations included ease of use and deployment, user feedback, price and value, reporting, asset discovery, automation, integration, risk prioritization, and more.
Attack Surface Discovery & Assessment Capabilities – 50%
We looked at how well ASM products discover and identify assets and risks, the breadth of environments covered, and automation features such as risk prioritization, patching and mitigation recommendations, and validation.
Ease of Use & Deployment – 20%
Attack surface management tools cover a lot of risks, assets, and environments, so their ease of use is particularly important for overburdened security teams. This also includes false alerts and the amount of tuning required.
Pricing & Value – 20%
We looked at both the price of the products as well as the relative value and breadth of features that users get for that price.
Additional Features – 10%
These include integration with other tools like SIEM, CMDB, and CI/CD tools, and reporting, including compliance features.
Frequently Asked Questions (FAQs)
What Is the Significance of ASM in Business?
ASM is critical because it enables firms to identify and manage any security threats in advance, creating a strong defense against cyberattacks.
What Distinguishes ASM from Standard Security Measures?
ASM focuses on mapping the whole attack surface, including hidden or undisclosed assets, delivering a more complete security strategy and going beyond tools like vulnerability management.
What Characteristics Should I Look for in ASM Software?
In an ASM solution, look for effective threat exposure detection and remediation, user-friendly interfaces, seamless integration with remediation tools, real-time threat information, and thorough reporting capabilities.
Is ASM Appropriate for Small Businesses?
Yes, ASM is effective for all sizes of enterprises. Many ASM solutions provide scalable choices to meet the unique requirements and budgets of small organizations.
Is It Possible to Combine ASM Software with Current Security Tools?
Yes, ASM software is designed to integrate effectively with other security solutions, thus improving the overall security architecture.
How Frequently Should ASM Scans Be Performed?
To keep up with the changing nature of digital assets and evolving risks, regular ASM scans should be performed, ideally on a frequent, if not continuous, basis.
Is ASM Software Resistant to Zero-Day Vulnerabilities?
Yes, by delivering real-time threat intelligence and response capabilities, ASM software can be successful against zero-day vulnerabilities.
What Industries Are the Most Benefited by ASM Solutions?
Because of their superior threat detection and response capabilities, ASM solutions help industries dealing with sensitive data, such as banking, healthcare, and government.
Bottom Line: ASM Reduces Attack Surfaces
Attack Surface Management software is a welcome evolution in vulnerability management, securing digital assets by discovering, analyzing, and maintaining a wide range of assets and environments that attackers may try to exploit. The best ASM provider must be chosen carefully, taking into account criteria such as the size and complexity of the attack surface, security budget, current infrastructure, risk tolerance, location and type of sensitive data, and special features that match an organization’s needs. A solid reputation and track record are also a necessity, and the vendors we’ve reviewed here are all capable of meeting these criteria.







