6 Best Authenticator Apps for 2024
Tech Republic Security
MARCH 26, 2024
Authenticator apps provide an extra layer of security. Learn about the best authenticator apps to secure your online accounts and protect your privacy.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.
 Authentication Related Topics
Authentication Related Topics 
Tech Republic Security
MARCH 26, 2024
Authenticator apps provide an extra layer of security. Learn about the best authenticator apps to secure your online accounts and protect your privacy.
Tech Republic Security
MARCH 5, 2024
Learn about passwordless authentication, and explore the different types, benefits and limitations to help you decide which solution to choose.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Schneier on Security
NOVEMBER 17, 2022
Twitter is having intermittent problems with its two-factor authentication system: Not all users are having problems receiving SMS authentication codes, and those who rely on an authenticator app or physical authentication token to secure their Twitter account may not have reason to test the mechanism.

Tech Republic Security
APRIL 2, 2024
Discover the top passwordless authentication solutions that can enhance security and user experience. Find the best solution for your business needs.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers.

Tech Republic Security
MARCH 20, 2024
Explore top multi-factor authentication solutions for enhanced security and user authentication. Learn about the benefits and features of leading MFA providers.

Schneier on Security
NOVEMBER 22, 2023
Signal has had the ability to manually authenticate another account for years. iMessage is getting it : The feature is called Contact Key Verification, and it does just what its name says: it lets you add a manual verification step in an iMessage conversation to confirm that the other person is who their device says they are.
Schneier on Security
OCTOBER 5, 2020
A Study on Usability and Security Perceptions of Risk-based Authentication “: Abstract : Risk-based Authentication (RBA) is an adaptive security measure to strengthen password-based authentication. I’ve blogged about risk-based authentication before. Paper’s website.
Tech Republic Security
MARCH 14, 2024
The benefits of passwordless authentication include enhanced security, convenience, and boosted productivity. Learn how your organization can take advantage.

Schneier on Security
APRIL 1, 2022
FIDO2 multi-factor authentication systems are not susceptible to these attacks, because they are tied to a physical computer. .” Calling the target, pretending to be part of the company, and telling the target they need to send an MFA request as part of a company process.

Schneier on Security
NOVEMBER 9, 2022
CISA is now pushing phishing-resistant multifactor authentication. Roger Grimes has an excellent post reminding everyone that “phishing-resistant” is not “phishing proof,” and that everyone needs to stop pretending otherwise. His list of different attacks is particularly useful.

Security Boulevard
MARCH 18, 2024
Just a few days earlier, threat researchers at Proofpoint reported a phishing campaign by the well-known threat group TA577 that targets Windows NT LAN Manager (NTLM) authentication information. The post Protecting Against Attacks on NTLM Authentication appeared first on Security Boulevard. The fallout remains unknown.

Schneier on Security
OCTOBER 21, 2021
Roger Grimes on why multifactor authentication isn’t a panacea : The first time I heard of this issue was from a Midwest CEO. His organization had been hit by ransomware to the tune of $10M. Operationally, they were still recovering nearly a year later. And, embarrassingly, it was his most trusted VP who let the attackers in.

Tech Republic Security
JUNE 6, 2022
Check out these features from Authy and Google Authenticator before deciding which authentication tool is best for you. The post Authy vs Google Authenticator: Two-factor authenticator comparison appeared first on TechRepublic.

Tech Republic Security
JANUARY 25, 2024
Learn how to protect yourself and your sensitive information from phishing attacks by implementing multi-factor authentication.

Bleeping Computer
MARCH 4, 2024
The hacking group known as TA577 has recently shifted tactics by using phishing emails to steal NT LAN Manager (NTLM) authentication hashes to perform account hijacks. [.]
Security Boulevard
APRIL 17, 2024
Authentication: The digital gatekeeper. The post The Unseen Powerhouse: Demystifying Authentication Infrastructure for Tech Leaders appeared first on Security Boulevard. Explore the hidden infrastructure and cutting-edge security keeping your data safe online.

Schneier on Security
AUGUST 6, 2021
” Abstract: A master face is a face image that passes face-based identity-authentication for a large portion of the population. Fascinating research: “ Generating Master Faces for Dictionary Attacks with a Network-Assisted Latent Space Evolution.”

Schneier on Security
DECEMBER 18, 2020
The NSA has published an advisory outlining how “malicious cyber actors” are “are manipulating trust in federated authentication environments to access protected data in the cloud.” From the summary : Malicious cyberactors are abusing trust in federated authentication environments to access protected data.

Schneier on Security
MARCH 1, 2023
A reporter used an AI synthesis of his own voice to fool the voice authentication system for Lloyd’s Bank.

Schneier on Security
DECEMBER 15, 2020
Logs from the Exchange server showed that the attacker provided username and password authentication like normal but were not challenged for a second factor through Duo. The logs from the Duo authentication server further showed that no attempts had been made to log into the account in question.

Tech Republic Security
AUGUST 19, 2022
The post Alternatives to facial recognition authentication appeared first on TechRepublic. Learn the problem with facial recognition as well as software and hardware alternatives to the technology.

Daniel Miessler
MARCH 24, 2021
Basically, how secure is someone’s current behavior with respect to passwords and authentication, and how can they improve? Mar 24, 2021 — Someone mentioned that there are higher ranks of authentication out there, which I agree with, but this is specifically for everyday users. How to use this model.

Tech Republic Security
MARCH 16, 2022
We compare the features and costs of two of the biggest players in this space, Duo and Microsoft Authenticator, and pit them head-to-head. The post Duo vs. Microsoft Authenticator: Compare multifactor authentication software appeared first on TechRepublic.

Security Boulevard
APRIL 11, 2024
The post Hackathon: Authenticating header-based apps appeared first on Strata.io. The post Hackathon: Authenticating header-based apps appeared first on Security Boulevard. Strata’s CEO loves it when people tell him something is impossible, and that “challenge, accepted” mentality has clearly filtered through.

Security Boulevard
OCTOBER 2, 2021
October is Cybersecurity Awareness Month so in this episode we discuss multi-factor authentication and the use of authenticator apps. Multi-factor authentication is one of the most important things that you can enable to secure your online accounts but its unfortunately overlooked by most people.
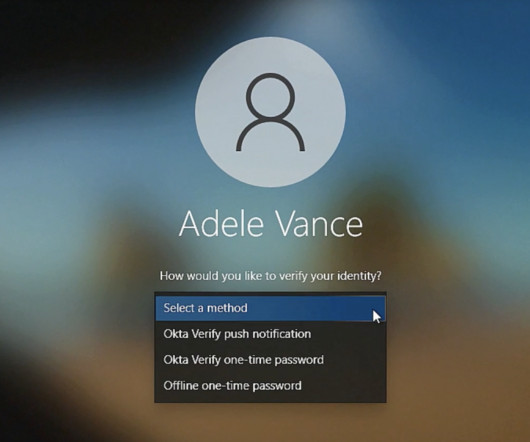
Tech Republic Security
JUNE 20, 2023
Okta’s formula for multi-device identity authentication for a hybrid workforce: extract passwords, add ease of passkeys across devices. The post Okta moves passkeys to cloud, allowing multi-device authentication appeared first on TechRepublic.

Security Affairs
MARCH 8, 2024
The three flaws fixed are: CVE-2024-21899 : an improper authentication vulnerability could allow users to compromise the security of the system via a network. CVE-2024-21900 : an injection vulnerability could allow authenticated users to execute commands via a network.

Security Boulevard
APRIL 4, 2024
Portland, Oregon, April 4th, 2024, CyberNewsWire Center Identity, a pioneering cybersecurity company, is excited to unveil its patented secret location authentication, reshaping how businesses manage workforce digital identity. This proprietary technology enables users to authenticate their identity using a secret location selected on a map.

Security Boulevard
NOVEMBER 16, 2023
The post Google And Yahoo New Email Authentication Requirements appeared first on EasyDMARC. The post Google And Yahoo New Email Authentication Requirements appeared first on Security Boulevard. Google and Yahoo have recently announced new requirements.

Security Boulevard
FEBRUARY 5, 2024
Two-factor authentication and multi-factor authentication are often used interchangeably; however, that’s not the case. Both authentication methods aim to strengthen security protocols and fortify security, but they differ. With this blog, let’s understand more about MFA security and 2FA vs MFA debate.

Tech Republic Security
AUGUST 11, 2023
Looking for an alternative to Google Authenticator? Here's our comprehensive list covering the top competitors and alternatives to help you find your best fit.

Tech Republic Security
MARCH 27, 2023
GitHub wants you to protect your account with the right type of authentication. The post How to secure your GitHub account with two-factor authentication appeared first on TechRepublic.

Bleeping Computer
NOVEMBER 7, 2023
Microsoft has introduced a new protective feature in the Authenticator app to block notifications that appear suspicious based on specific checks performed during the account login stage. [.]
Security Boulevard
DECEMBER 22, 2023
At AWS re:Invent, Shira Rubinoff talks with Graeme Speak of BankVault Cybersecurity about passwordless authentication. The post AWS re:Invent 2023: Passwordless Authentication appeared first on Security Boulevard.

Tech Republic Security
MARCH 17, 2022
The first line of defense against ransomware lies with email authentication. The post Email authentication helps governments and private companies battle ransomware appeared first on TechRepublic. Learn more information about how to take a proactive approach to cyber attacks.
Security Boulevard
MARCH 14, 2024
Learn how to enable multi-factor authentication. This comprehensive guide explores MFA's importance and best authenticator apps. The post How to Enable Multi-Factor Authentication: Comprehensive Guide appeared first on SternX Technology.

Tech Republic Security
JUNE 11, 2020
A password alone will not protect sensitive information from hackers--two-factor authentication is also necessary. Here's what security pros and users need to know about two-factor authentication.

Malwarebytes
NOVEMBER 24, 2023
Researchers have found several weaknesses in Windows Hello fingerprint authentication on Dell Inspiron 15, Lenovo ThinkPad T14, and Microsoft Surface Pro X laptops. They found vulnerabilities that allowed them to completely bypass Windows Hello authentication on all three. The input has to be authenticated.

Heimadal Security
AUGUST 11, 2023
Risk-Based Authentication (also known as RBA, context-based authentication, or adaptive authentication) is a security mechanism that looks at the profile (IP address, device, behavior, time of access, history, and so on) of the agent asking for access to the system in order to assess the potential risk associated with that transaction.

Tech Republic Security
MARCH 9, 2023
The post GitHub rolling out two-factor authentication to millions of users appeared first on TechRepublic. Over the next nine months, the largest internet hosting service for software development and collaboration will make all code contributors add another layer of electronic evidence to their accounts.

Duo's Security Blog
OCTOBER 13, 2023
Multi-factor Authentication (MFA) protects your environment by guarding against password weaknesses with strong authentication methods. In our last blog, we discussed using strong passwords and a password manager to provide better defense at the first layer of the authentication process. What is MFA?

Security Boulevard
FEBRUARY 27, 2024
In this article, you will find a more in-depth look at the specific issue, with real-world scenarios where it is applicable, as well as […] The post Weak or Misconfigured Multi-Factor Authentication (MFA) Methods appeared first on TuxCare.

Security Boulevard
JANUARY 17, 2024
s namesake platform that enables end users to securely be authenticated on-demand using any device is now generally available. The post Badge Makes Device-Independent Authentication Platform Available appeared first on Security Boulevard. Badge Inc.'s
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?

Let's personalize your content