Contents:
As industry experts continuously predict that cybercrime will only get worse in the following years, we see that the digital world is keen to find and implement new strategies to bolster cybersecurity. Today I am going to talk about one of these strategies: the Kerberos authentication protocol.
What Is Kerberos?
As you know, normally, users access computer systems by using a password. The problem with this authentication system is that if malicious actors get hold of the password, they can assume the user’s identity and obtain access to corporate networks. Companies should improve the security of their systems and users by using technologies that provide secure authentication over insecure networks. This is where Kerberos can help.
Kerberos is a computer network security protocol that authenticates service requests between two or more trusted hosts across a non-secure network, like the Internet. This system, which works like a gateway between users and untrusted networks, was developed to keep threat actors out of a private network.
Because Kerberos builds on symmetric-key cryptography (also known as secret-key cryptography), it significantly outperforms previous authorization mechanisms. It also requires a trusted third party for user identity verification and client-server application authentication, making it much more challenging for intruders to infiltrate a network.
The protocol was developed in 1983, the same year that the Domain Name System (DNS) emerged, so it has been around for quite some time. Initially created for Project Athena, an educational project at MIT, it now supports a wide range of functions, such as single sign-on (SSO) implementations, and is the preferred authentication protocol for websites.
Kerberos support is built into multiple popular operating systems, including Microsoft Windows, Apple macOS, FreeBSD, and Linux. Like DNS, the security protocol is a commonly used service that the majority of users aren’t even aware of using.
The Curious Case of the Name
This computer network authentication protocol was named after Kerberos (also spelled Cerberus) from Greek mythology, which is the legendary ferocious three-headed guard dog of the Gates to the Underworld.
In the modern world, Massachusetts Institute of Technology (MIT) computer scientists decided to go with this name for the protocol thinking that the three heads of the mythical creature represent the following three factors:
- Client: The party that wishes to provide its identity
- Application server: The service to which the client or user wishes to gain access
- Key Distribution Center (KDC): A trusted third-party authentication service that provides tickets
Because Kerberos requires these three elements to authenticate and has a proven track record of making computing safe and secure, we’d say that the name is perfect.
How Does Kerberos Authentication Work?
As I mentioned before, Kerberos authenticates and verifies user identities using symmetric key cryptography and a Key Distribution Center (KDC). The three components that make up a KDC are:
- A Ticket Granting Server (TGS) that makes the connection between the user and the service server (SS)
- A Kerberos database that keeps all verified users’ passwords and identification.
- An Authentication Server (AS) that carries out the initial authentication
So, let’s take a closer look at the steps:
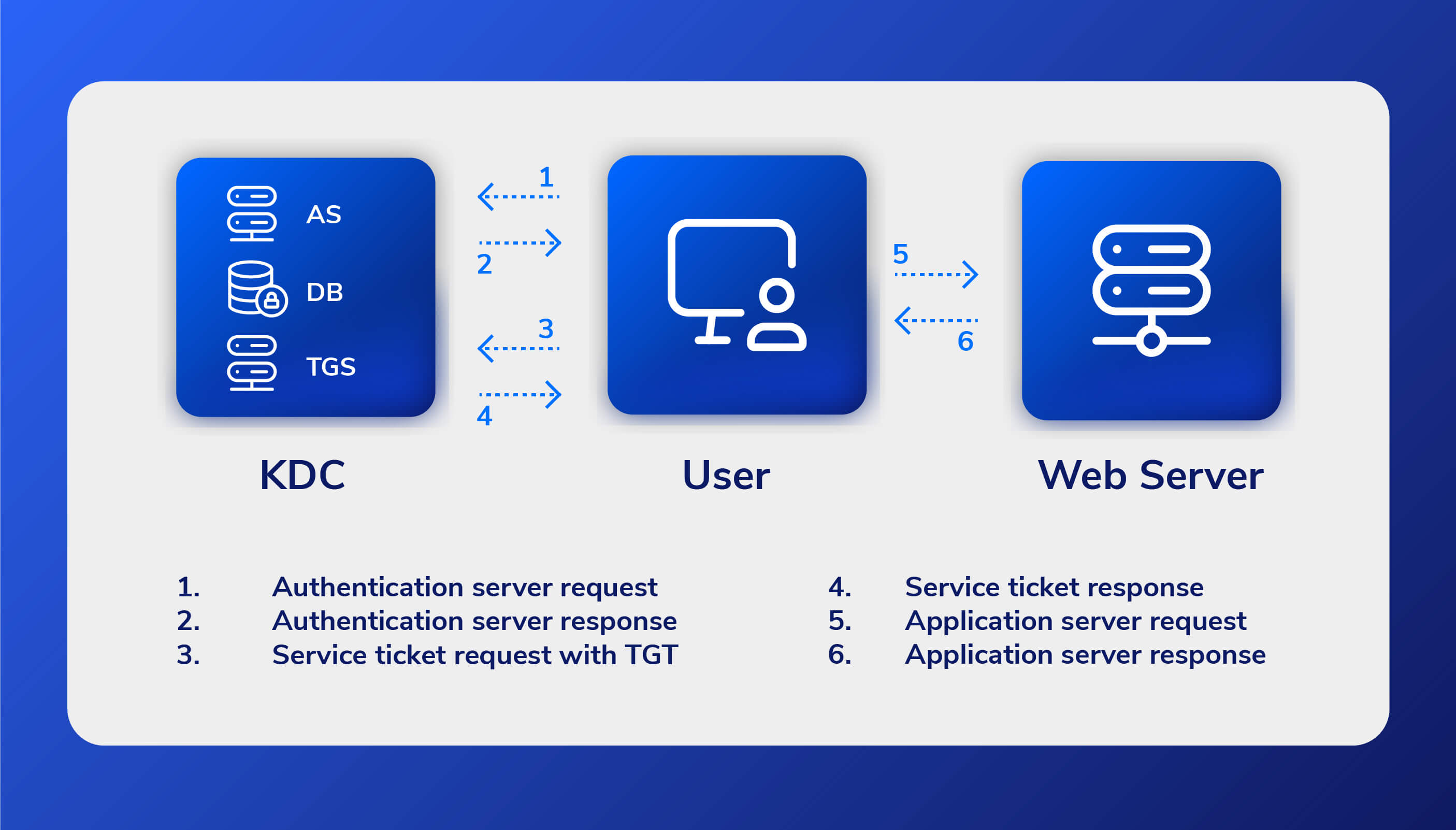
1. Authentication server request
In order to begin the Kerberos client authentication process, the initiating client sends an authentication request to the Kerberos KDC authentication server. Since no confidential data is contained in the request, the initial authentication request is transmitted in plaintext. The authentication server confirms that the client exists in the KDC database and retrieves the private key of the initiating client.
2. Authentication server response
If the username of the client is not found in the KDC database, the client cannot be authenticated, and the entire process is terminated. Otherwise, the authentication server issues a Ticket Granting Ticket (TGT) and a session key to the client.
3. Service ticket request with TGT
After being authenticated by the authentication server, the client asks for a service ticket from the TGS. The TGT that the KDC authentication server sent must be attached to this request.
4. Service ticket response
If the Ticket Granting Server is able to authenticate the client, it sends credentials and a ticket to access the requested service. This transference is encrypted using a session key unique to the user and service that are being accessed. Access to the requested service is granted using this identity proof. The service verifies the initial request before confirming its identity to the system making the request.
5. Application server request
The client sends an access request to the application server, which includes the service ticket obtained in the previous step. Client access is permitted if the application server can successfully authenticate this request
6. Application server response
This response is necessary when the client requests that the application server authenticate itself. The client has already authenticated itself, and the AS response includes Kerberos authentication of the server. The client has access to the service thanks to the service ticket sent by the TGS. Since the service ticket is timestamped, one ticket can be used for a set amount of time without requiring a new authentication. Limiting the ticket’s validity lowers the likelihood that someone else will be able to use it in the future.
Kerberos VS other Authentication Protocols
Although there are other authentication protocols in use, Kerberos is arguably the most popular. In addition to being widely used, Kerberos has shown to be a secure protocol that can handle unforeseen input or execution errors.
Kerberos VS Microsoft New Technology LAN Manager (NTLM)
Microsoft NTLM is an old authentication protocol that can still be used in Active Directory domains to provide SSO services. Starting with Windows 2000, Microsoft discourages the use of NTLM for authentication and switches to Kerberos instead. At the moment, Kerberos is the preferred authentication protocol for Windows.
The primary distinction between Kerberos and NTLM is how the two protocols manage authentication. To authenticate a user, the former employs a two-part process that uses a Ticket Granting Service (TGS) or Key Distribution Center (KDC), whereas the latter relies on a three-way handshake between the client and server.
Kerberos VS Lightweight Directory Access Protocol (LDAP)
Lightweight Directory Access Protocol is widely used to authorize user access to accounts on networked services. This authentication protocol is frequently used in combination with Kerberos, with LDAP providing authorization services and Kerberos providing authentication services for large-scale networks.
Benefits of Kerberos Authentication
Using Kerberos as an authentication service has some important advantages. Some of them are:
Effective access control
Effective access control can be achieved with the Kerberos authentication protocol. Users benefit from having a single location to monitor all logins and the implementation of security policies.
Mutual authentication
Users and service systems are able to verify each other’s identities using Kerberos authentication. Throughout the process, both the user and the server will be aware that the counterparts with whom they are communicating are legitimate.
Limited key ticket lifetime
All Kerberos tickets have timestamps and lifetime data, and administrators control the duration of authentication.
Reusable authentication
Kerberos authentication is both long-lasting and reusable. The system will need to validate each user only once. The user will not have to enter their personal details for verification purposes as long as the ticket is valid.
Robust security
In order to build a solid defense, Kerberos security authentication protocols use cryptography, various secret keys, and third-party authorization. It is challenging for threat actors to masquerade as users or services because passwords are not communicated over networks, and secret keys are encrypted.
How Secure Is Kerberos?
Even though Kerberos has strong encryption to safeguard sensitive information, which is why cybersecurity experts from all over the world consider it to be secure, no security measure is 100% bulletproof, and Kerberos is no exception. The fact that Kerberos has been around for so many years and is one of the most widespread authentication protocols has given attackers the chance to figure out ways to breach it. Some of these ways include:
- Pass-the-ticket: the process of creating a false session key and providing the resource with the forged credentials
- Golden ticket: a ticket that gives domain admin access to a user
- Silver ticket: a fake ticket that allows access to a service
- Credential stuffing/ brute force: automated repeated password-guessing attempts
- Encryption downgrade with Skeleton Key Malware: malware that can go past Kerberos authentication protocol, but the attack requires administrative access
- DCShadow attack: a new type of cyber threat in which malicious actors obtain sufficient access within a network to establish their own DC for further infiltration.
Despite this, Kerberos continues to be the top security access protocol on the market right now. It has been widely used for decades and is regarded as an advanced and secure method of user authentication.
Security researchers have been looking into Kerberos since its appearance, and they have discovered flaws in both the protocol and specific Kerberos implementations. The vulnerabilities have been fixed, and Kerberos continues to be essential for online authentication.
How Can Heimdal® Help?
Kerberos authentication enables service systems and users to authenticate each other. As mentioned before, this is called mutual authentication and is a key component of the zero-trust approach, Zero-Trust being a central element in the Heimdal cybersecurity strategy.
We want to let you know that we have a product that facilitates zero-trust implementation effortlessly: it’s called Privileged Access Management and supports a zero-trust function. PAM is an automated tool that permits you to escalate and de-escalate user rights, giving you full control and protection over privileged permissions within your organization.

Heimdal® Privileged Access Management
- Automate the elevation of admin rights on request;
- Approve or reject escalations with one click;
- Provide a full audit trail into user behavior;
- Automatically de-escalate on infection;
If you liked this article, make sure you follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










