
GitHub, used by the majority of major tech companies, has announced that it is rolling out 2FA. Acknowledging supply chain security risks, which have been on the rise, the company starts a nine-month rollout on Monday, March 13. All developers who contribute code on the platform will eventually have to adopt the security protocol, the company announced on Thursday.
SEE: Hiring kit: Full stack developer (TechRepublic Premium)
The Microsoft-owned DevOps service said the move aligns with the National Cybersecurity Strategy, which, among other things, puts the onus and more security responsibility on software vendors.
Jump to:
- Being a developer doesn’t make you invulnerable
- Different 2FA choices, but biometrics and passkeys trump SMS
- Latest move follows cadence of GitHub security programs
- Months-long rollout to minimize disruption, optimize protocols
- GitHub offers developers 2FA timeline
- Email flexibility to avoid lockout
Being a developer doesn’t make you invulnerable
Even developers make mistakes and can become victims of security breaches. Mike Hanley, chief security officer and senior vice president of engineering at GitHub, wrote in a May 2022 blog — which mentioned the 2FA plan for the first time — that compromised accounts can be used to steal private code or push malicious changes to that code.
“This places not only the individuals and organizations associated with the compromised accounts at risk, but also any users of the affected code,” he wrote. “The potential for downstream impact to the broader software ecosystem and supply chain as a result is substantial.”
Justin Cappos, a professor of computer science at NYU and co-developer of the in-toto and Uptane software security frameworks, said Github’s adoption of 2FA is a critical first step in addressing a major problem.
“Inserting code into an organization is one of the worst kinds of attacks someone can do. So protecting the way in which people are working on code, which today often means working on code through GitHub, is really key. To the extent that they are making it harder for attackers to do this, is a huge positive,” he said.
SEE: How to minimize security risks: Follow these best practices for success (TechRepublic Premium)
Different 2FA choices, but biometrics and passkeys trump SMS
GitHub is also offering a preferred 2FA option for account login with a sudo prompt, allowing users to choose between time-based one-time passwords, SMS, security keys or GitHub Mobile. However, the company is urging users to go with security keys, including physical security keys, such as Yubikey, and TOTPs, noting that SMS-based 2FA is less secure.
NIST, which no longer recommends 2FA, pointed out that:
- An out-of-band secret sent via SMS can be received by an attacker who has convinced the mobile operator to redirect the victim’s mobile phone to the attacker.
- A malicious app on the endpoint can read an out-of-band secret sent via SMS and the attacker can use the secret to authenticate.
“The strongest methods widely available are those that support the WebAuthn secure authentication standard,” said GitHub in its announcement. “These methods include physical security keys as well as personal devices that support technologies such as Windows Hello or Face ID/Touch ID.”
Cappos said the importance of differentiating 2FA methods can’t be overstated. “For 2FA, not all things are the same. Yubikeys, for example, are the gold standard because you would physically have to steal the key to cause something to happen,” he said.
SEE: 1Password is looking to a password-free future. Here’s why (TechRepublic)
GitHub said it is also testing passkeys, the next-generation credential protocol, as a defense against exploits like phishing.
“Because passkeys are still a newer authentication method, we’re working to test them internally before we roll them out to customers,” said a spokesperson. “We believe they’ll combine ease of use with strong and phishing-resistant authentication.”
Latest move follows cadence of GitHub security programs
In a move toward closing loopholes to combat threat actors, GitHub expanded its secret scanning program last fall, allowing developers to track any publicly exposed secrets in their public GitHub repository.
And earlier this year, GitHub launched a setup option for code scanning called “default setup” that lets users automatically enable code scanning.
“Our 2FA initiative is part of a platform-wide effort to secure software development by improving account security,” the company said in a release, noting that developer accounts are social engineering and account takeover targets.
Months-long rollout to minimize disruption, optimize protocols
The process for disseminating the new protocols is meant to minimize disruption to users, with groups selected based on the actions they’ve taken or the code they’ve contributed to, according to GitHub (Figure A).
Figure A
The company said the slow rollout would also make it easier for GitHub to make adjustments as needed before scaling to larger and larger groups over the course of this year.
A spokesperson for GitHub explained that, while the company won’t offer specifics on how users qualify for being part of certain groups in the 2FA cadence, the person did say groups are determined, in part, based on their impact on the security of the broader ecosystem. High-impact groups will include users who:
- Published GitHub or OAuth apps, Actions or packages.
- Created a release.
- Contributed code to repositories deemed critical by npm, OpenSSF, PyPI or RubyGems.
- Contributed code to any of the approximate top four million public and private repositories.
- Act as enterprise and organization administrators.
For those with a proactive bent, the company is offering 2FA immediately at a dedicated site.
GitHub offers developers 2FA timeline
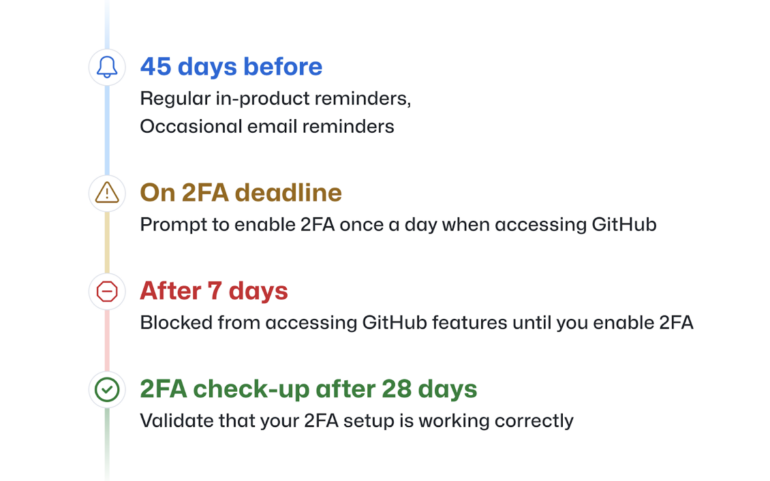
The process for GitHub contributors sets several time markers for initiating 2FA around a soft deadline (Figure B).
Figure B
Before the deadline
GitHub contributors selected for a pending 2FA group will get advance notification by email 45 days before the deadline, informing them of the deadline and offering guidance on how to enable 2FA.
Once the enablement deadline passes
Those notified will be prompted to enable 2FA the first time they access GitHub.com each day. They can snooze this prompt once a day for up to one week, but after that, they will be unable to access GitHub.com features until they enable 2FA.
28 days after 2FA is enabled
Users will receive a 2FA “check-up” while using GitHub.com, which validates that their 2FA setup is working correctly. Previously signed-in users will be able to reconfigure 2FA if they have misconfigured or misplaced second factors or recovery codes during onboarding.
Email flexibility to avoid lockout
Fortunately, the new protocols let users unlink email from a 2FA-enabled GitHub account to avoid the paradox of being locked out of the very thing — email — that allows them to verify the account if they’re unable to sign in or recover it.
“If you’re unable to find an SSH key, PAT, or a device that’s been previously signed into GitHub to recover your account, it’s easy to start fresh with a new GitHub.com account and keep that contribution graph rightfully green,” said the company.


