CakePHP Application Cybersecurity Research – Forgotten Endpoint: Authentication bypass with /open prefix
Web applications are often the first target for attackers due to the vast amount of sensitive information they contain. Ensuring the security of these applications is crucial to protect both users and businesses from potential cyber threats. One of the most effective ways to identify vulnerabilities in web applications is through web application penetration testing. In this comprehensive guide, we’ll explore the importance of web application penetration testing, focusing primarily on uncovering authentication bypass vulnerabilities with an example vulnerability that Dawid found in Cerebrate using the /open prefix.
!This is the last of nine articles in the “CakePHP Application Cybersecurity Research” series. Here you can find the previous ones dedicated to this topic:
- Be Careful with Reflections For Your Web Application Security
- Protect Your Website from Stored XSS Attacks: Understanding and Preventing Vulnerabilities in Open-source Applications
- Exploring the PHAR Deserialization PHP Vulnerability: A White Box Testing Example
- The Impact of a PHP Vulnerability: Exploring the Password Confirmation Bypass in MISP
- Hiding in Plain Sight: The Hidden Danger of SQL Injection in Input Field Names
- Bypassing security mechanisms in CakePHP vulnerability scanning
- Attack surface in CakePHP web application penetration testing
- White box penetration testing in action
In this article you will find:
- Introduction to Web Application Penetration Testing
- Authentication in Web Applications
- Authentication Bypass Vulnerabilities
- Understanding the
/openPrefix Vulnerability in Cerebrate - Detecting Authentication Bypass Vulnerabilities
- Impact of Authentication Bypass Vulnerabilities
- Preventing Authentication Bypass Vulnerabilities
- Conclusion
Introduction to Web Application Penetration Testing
Web application penetration testing is a systematic process of evaluating web applications’ security by simulating real-world attacks. The goal is to identify vulnerabilities and weaknesses that attackers could exploit to gain unauthorized access, steal sensitive data, or disrupt operations. By conducting web application penetration testing, companies can proactively address security issues and reduce the risk of a successful cyber attack.
Authentication in Web Applications
Authentication is a critical component of web application security, as it verifies the identity of users attempting to access the application. By providing login credentials (such as a username and password), users prove their identity and are granted access to specific resources and functionalities within the application.
However, attackers can exploit vulnerabilities in the authentication process to gain unauthorized access to sensitive data and functions. One such vulnerability is authentication bypass, where an attacker can bypass the authentication mechanism and directly access protected resources without providing valid credentials. On the other hand, in some rare cases there could be a vulnerable endpoint like our example /open prefix that allow direct access to functions and information without any authorization control.
Authentication Bypass Vulnerabilities
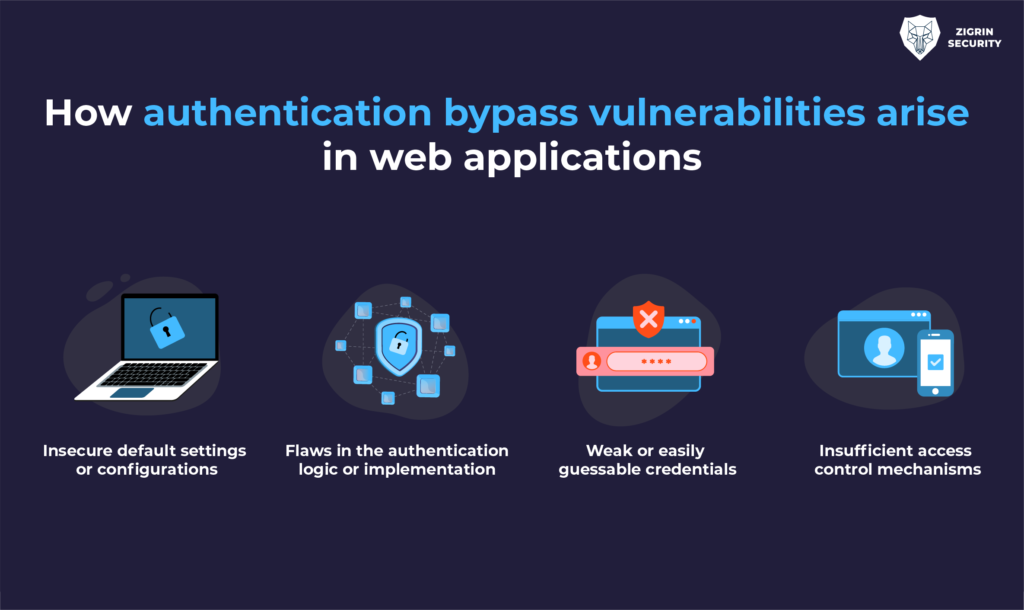
An authentication bypass vulnerability could occur when an application exposes an alternative path to a protected resource that does not require authentication. This allows unauthenticated users to access resources and functionalities that should only be available to authenticated users. Such vulnerabilities can compromise the confidentiality and integrity of the application’s data and functionalities.
There are several reasons why authentication bypass vulnerabilities can exist in web applications:
- Insecure default settings or configurations
- Flaws in the authentication logic or implementation
- Weak or easily guessable credentials
- Insufficient access control mechanisms
Understanding the /open Prefix Vulnerability in Cerebrate
During the web application penetration testing, Dawid detected a vulnerable endpoint that allows access “Organisations” and “Individuals” controllers by unauthenticated visitors. This /open prefix vulnerability is an example of an authentication bypass vulnerability.
An attacker could exploit this vulnerability by sending a request to the application with the /open prefix, bypassing the need for authentication. The application would then return a list of organizations or individuals, potentially exposing sensitive information to an unauthorized user.
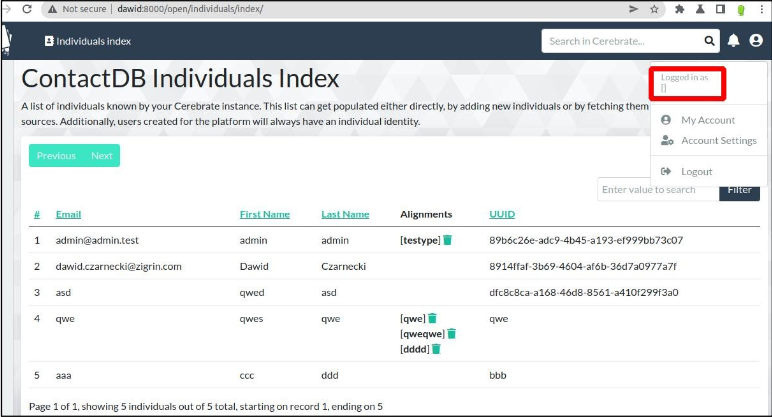
As you can see in the following screenshots, we were able to exfiltrate a list of organisations and individuals.
This one is for individuals:
And this one is for organisations:

Also, if you want to make sure there is no cookie or token sent via your browser during request, you could use the following curl command to access the protected pages without providing any credentials while testing similar vulnerabilities:
curl -X GET 'http://example.com/open/organisations' curl -X GET 'http://example.com/open/individuals'
Here is another screenshot that demonstrates curl command usage to access organizations without providing any token, cookie or credentials:

Detecting Authentication Bypass Vulnerabilities
Detecting authentication bypass vulnerabilities requires a thorough understanding of the web application’s authentication mechanism, access control policies, and potential alternative paths to protected resources.
Web application penetration testers can use various tools and techniques to identify these vulnerabilities but in such unexpected cases the best way is, manual testing and analysis of the application’s source code, configuration files, and access control policies.

Exploiting Authentication Bypass Vulnerabilities
Once an authentication bypass vulnerability is identified, an attacker can exploit it to gain unauthorized access to protected resources or functionalities. This could involve sending specially crafted requests to the application, manipulating input data, or modifying browser cookies and session tokens.
In the case of the /open prefix vulnerability, an attacker could use a tool like curl or a web browser to send requests to the vulnerable controllers without providing any authentication credentials. This would allow them to access sensitive data and potentially perform actions reserved for authenticated users.
Impact of Authentication Bypass Vulnerabilities
The impact of authentication bypass vulnerabilities can be severe, depending on the sensitivity of the data and functions exposed. Unauthorized access to an application can result in data breaches, loss of business-critical information, and reputational damage.
Moreover, if an attacker can compromise a high-privileged account function, such as an administrator, they could gain full control of the application and its underlying infrastructure. Even compromising low-privileged accounts functions can provide attackers with additional attack surfaces, as they may be able to access internal pages and resources not typically available to the public.
Preventing Authentication Bypass Vulnerabilities
To minimize the risk of authentication bypass vulnerabilities, organizations should:
- Implement robust and secure authentication mechanisms, including multi-factor authentication (MFA) and strong password policies
- Regularly update and patch systems, software, and applications to address known vulnerabilities
- Conduct thorough web application penetration testing to identify and remediate potential authentication bypass vulnerabilities
- Ensure proper access control policies and configurations are in place, including the principle of least privilege
- Continuously monitor and audit application access logs and user activities for signs of unauthorized access or suspicious activity
- And most importantly, review the authorization schema of the application. Access to all controllers and actions besides required ones like login or register should be accessible only to authenticated users

Conclusion
Web application penetration testing is a critical component of ensuring the security of web applications and protecting sensitive data from unauthorized access. By proactively identifying and addressing authentication bypass vulnerabilities, such as the /open prefix vulnerability, organizations can reduce the risk of successful cyber attacks and maintain a strong security posture.
Remember that web application penetration testing is an ongoing process, and new vulnerabilities may emerge as applications evolve and attackers develop new techniques. Regularly updating and testing your web applications is essential to maintaining a secure environment and protecting your organization from potential threats.

Let’s talk about conducting cybersecurity research of your web application.
Book a chat with a cybersecurity expert
Is this article helpful to you? Share it with your friends.


