Digital rights management (DRM) is an encryption technology that enforces creator’s rights. The most well-known examples restrict making copies of digital files, yet there are other techniques and use cases to explore — as well as benefits and challenges. To round out understanding, I cover how DRM is applied, top available technologies, and legal considerations for using DRM.
Table of Contents
How Does Digital Rights Management (DRM) Work?
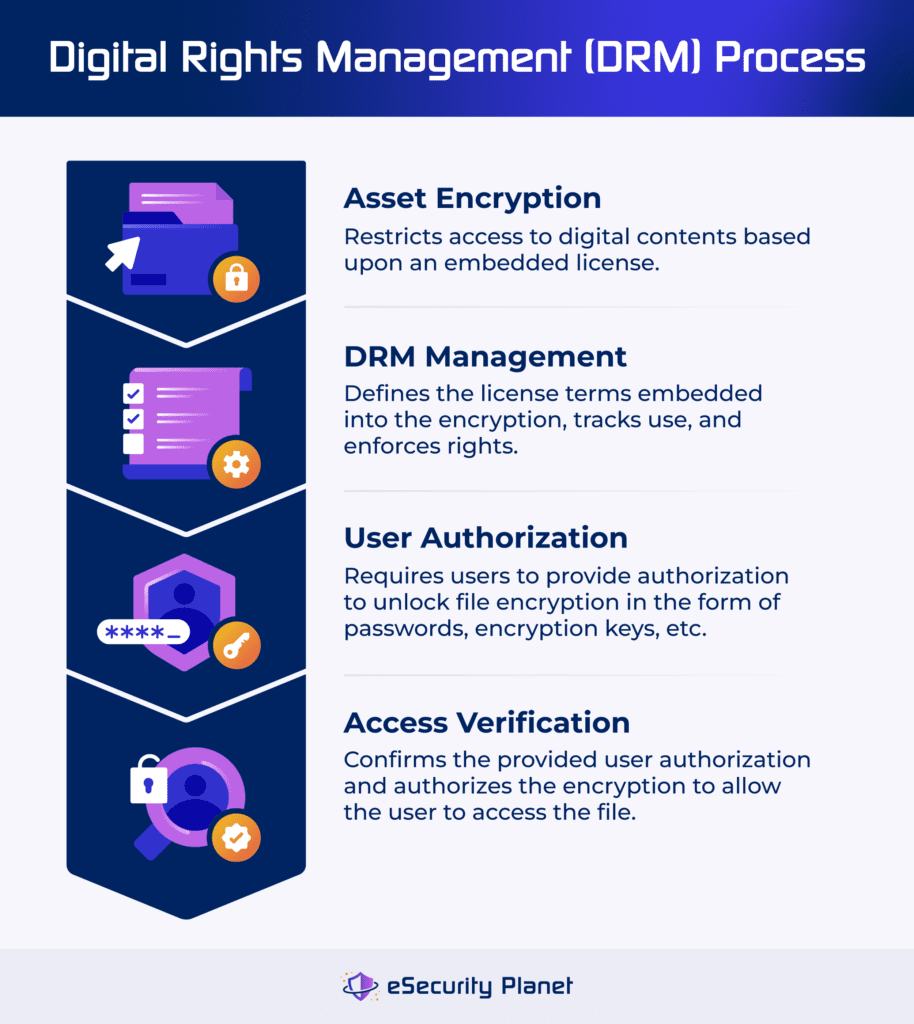
Digital rights management wraps digital data into an encrypted wrapper tied to a license that contains the rules for how the content may be used. After encryption, you can distribute the file and users will access it according to the DRM license rules. DRM typically requires four stages to function: encryption, management, authorization, and verification.
- Encryption of digital files enforces content owner’s rights and restricts the future use of the protected data. A common restriction involves controlled access that will only allow file access in the presence of specific hardware (microchip set, etc.), IP address, geographic location, or device type. Other restrictions could include limited duration access, flagged ownership (watermarks, metadata, etc.), or use restrictions such as limited copies or blocked printing.
- Management of DRM defines the encryption process, controls the software performing encryption, defines the license terms, and controls the file access restrictions. The management software will also track encrypted file use and continuously enforce digital rights.
- Authorization provides the key for the encrypted file tied to the digital license with rules for how to use the content, but doesn’t unlock the asset without verification. The authorization can be associated with specific hardware, shared encryption keys, passwords, and more.
- Verification of the DRM process validates the authorization key and finally unlocks the file. This process can be built-in to the DRM encryption file itself for a combined authorization and verification step or require an internet connection to verification servers.
6 Benefits of Digital Rights Management
When an organization applies digital rights management to an asset, most seek the primary benefit of securing content. Yet, DRM also helps to claim ownership of the digital content, enables potential revenue streams, helps track files, provides enforcement evidence, and reduces labor costs for internal use.
Secures Content for Specific Use
DRM secures content to limit theft and restrict use to authorized users. This primary benefit extends to third-party partners to limit use and prevent damage from data breaches or attempts to illegally distribute or access the content. Secured content remains private until unlocked and can also be regionally restricted to comply with local laws regarding age or content restrictions.
Claims Ownership of Content
Applying DRM to content stakes an ownership claim as unobtrusive as a watermark for photos or marketing material or as complete as password-protected content with highly restrictive use restrictions. DRM reinforces copyright with tangible restrictions and can secure secret or sensitive information against theft or breach.
Enables Payment Opportunities
Secured DRM files protected against free use enable opportunities to unlock the files. Payments could be direct or related to subscriptions through third parties, such as a movie licensed to Netflix. Without DRM, copyright owners risk widespread distribution of intellectual property without compensation.
Permits File Tracking
The full range of free-use to fully-secured DRM content can be configured to contact a validation server. The IP address that sends the validation request can be tracked and used for usage statistics, geographic use limitations, or to comply with local regulations such as age restrictions or territorial licensing.
Provides Evidence for Enforcement
DRM incorporates watermarks and metadata that provide third parties with evidence of ownership. Third-party licensees will be more confident that their licensing fee investments are protected and law enforcement can also use the DRM to verify ownership when pursuing piracy or IP infringement cases.
Reduces Internal Use Labor Costs
DRM can apply to internal digital resources to help marketing, sales, legal, and other teams understand where and when digital resources may be safely used. By affiliating licensing or use information to the files themselves, teams save significant time because they don’t have to check databases, expiration dates, or go through permissions processes. Additionally, risk of misuse will be decreased which saves further time and legal costs from mistakes.
5 Challenges & Limitations of DRM
Digital rights management helps rights holders, but the technology also has limitations. It can bring about disrupted availability, usability issues, dissatisfied consumers, and insufficient security, and the tools tend to be limited.
- Disrupted availability: Products that require validation fail when used without internet access or when validation servers are disrupted or discontinued. Reduce this poor user experience by protecting servers sufficiently or a different DRM validation option.
- Diminished usability: DRM schemes can slow performance, fail to meet industry standards, or lose copyright holder support, which affects a user’s experience. Test DRM tools for potential performance issues in advance to avoid this issue.
- Disgruntled consumers: Consumer rights concerns and notable DRM incidents, such as the security flaw added by the 2005 Sony BMG DRM, introduces strong consumer resistance. Minimize resistance with a non-disruptive DRM experience.
- Incomplete security: Even good DRM exposes assets to theft or copying from expert users or under specific conditions (analog conversion, screen recording, etc.). Consider overlapping security controls where possible in anticipation of a small failure rate.
- Limited tools: DRM tools won’t protect all digital assets equally and may be specialized in specific types of assets or under specific conditions (ex: video streaming). Be sure to select a tool appropriate for the asset and maintain realistic expectations.
In addition to the challenges for an organization to use DRM, network security professionals must also worry about malicious use of DRM. Some attackers take advantage of DRM capabilities to protect files against antivirus inspection and conceal malware. While this proves the capabilities of DRM to secure assets, it also creates circumstances that undermine DRM adoption.
Common Use Cases of DRM-Protected Contents
Many different companies use DRM protection to protect assets. The most common examples seen daily include music, books, protected files or emails, software or games, and stock photography.
- Digital music: Applies various DRM to allow purchases of single songs (iTunes, etc.), or to track songs played to pay artists for streaming (Spotify, YouTube, etc.).
- eBooks: Limits sharing and devices, and can impose time-based restrictions for digital book files distributed to devices and apps such as the Kindle.
- Intellectual property: Implements DRM protection for patent documents, pharma research, and other top secret documents for secure sharing and tight access control.
- Regulated emails: Adds DRM email encryption for HIPAA-regulated health information and other sensitive content that must be shared with external parties.
- Software licenses: Use license numbers to unlock DRM and allow installation and continued use of software or games from Microsoft, Activision, Adobe, etc.
- Stock photography: Applies watermarks to photos and tracks metadata for licensed photos to ensure compliance with the terms of purchase and use.
The use of DRM will continue to expand as costs lower and more organizations seek the benefits of DRM protection.
DRM License Models & Architecture
Digital rights management uses three categories of licensing models and four general verification architectures to unlock DRM-protected assets. Once implemented, DRM will use one of two possible support architectures to enable DRM access. Each option provides unique advantages and disadvantages for implementation and user experience.
Licensing Models
DRM users license access to DRM products through subscriptions, pay-per-use fees, or perpetual licensing options.
- Subscription-based: Charges regular fees on a regular basis (monthly, annually, etc.) for continued access to the asset, such as a streaming music subscription.
- Pay-per-use: Requires users to pay for each access attempt or can allow for a limited duration with each purchase, such as seven-day access to a streamed movie.
- Perpetual licensing: Unlocks access to the asset for a single payment, either directly to the asset holder or through resellers, such as a video game purchased at a store.
All three models may be implemented directly by the DRM rights holder or may be outsourced to a third party to manage both the DRM and the payment infrastructure. For example, Disney offers a subscription-based access to movies through Disney+, pay-per-use access to movies through Amazon.com, and perpetual licenses when consumers buy DVDs from a retailer.
Subscriptions and pay-per-use options allow a rights holder to specify strict limitations for use and offer lower prices than perpetual licenses. However, many consumers prefer the ownership bestowed by a perpetual license, which can give additional rights (see Fair Use below).
Verification Architectures
DRM owners need to implement architecture to enable a selected licensing model. The four categories of verification architectures include online, always-on, offline, and hardware.
- Online verification: Requires a DRM license server available for users to access to validate access. This model supports all three license types but requires implementation of a licensing server, which can be vulnerable to disruption.
- Always-on verification: Provides a specialized version of online verification that regularly re-validates access. This model provides more stringent control over use (geolocation, time duration, etc.), but significantly increases server disruption risks.
- Offline verification: Eliminates DRM server requirements in favor of authentication and validation within the DRM encryption. This model broadens usability for the user and reduces support infrastructure, but requires validation mechanisms built into the DRM.
- Hardware verification: Represents a subcategory of offline verification using external hardware (ex: microchip), to validate access. This model improves protection, but requires significant preparation and expense. Costs can be offset by selling the hardware, such as a DVD player, for a separate fee.
To avoid poor user experiences, select a DRM verification that can be supported easily with the current available resources (budget, labor, technical talent).
DRM Support Architectures
Choosing a DRM solution also requires consideration of the technology required to continue to support the DRM. The two main options to select for support are DRM servers and viewers and each comes with associated security concerns:
- DRM license servers: Provide remote DRM validation on the web or through a local network and manage license restriction checks. However, server implementation requires various security solutions to protect this infrastructure from attacks such as distributed denial of service (DDoS).
- Specific DRM viewers: Enforce DRM capabilities through plugins, browsers, or installed software.
- DRM plugins (ex: PDF plugin) enable quick and easy deployment, but can be bypassed by updates or other plugins. Users also need to download plugins and keep them updated.
- Browser viewers use cloud-based asset storage and require the least user effort to implement, but can be slow, especially when combining large image files and slow local networks.
- Installed software offers the most control over user experience and the best security, but the local software installation will be resisted by some users and IT admins because it introduces requirements for regular maintenance and updates.
These security concerns will affect both corporate and user adoption and must be considered when examining DRM options to determine fit.
6 DRM Technologies to Use Now
Many vendors offer technologies to help manage internal and external assets with DRM protection. Some options, such as hardware-based DRM, will require extensive engineering and expense beyond the scope of this article. For much more turnkey DRM options, consider:
- Adobe Experience Manager: Supplies brands with cloud-based infrastructure for digital asset management (DAM) and DRM integrated with Creative Cloud applications.
- Fortra Digital Guardian: Facilitates secure collaboration for any file types without any software required for the end user to install.
- Kiteworks DRM: Provides editable file access for partners while retaining usage rights for office files, PDFs, graphics, and video files.
- Lock Lizard: Offers DRM protection for PDF files and a secure PDF viewer that provides control over file copies, printing, screenshots, or sharing.
- Red Points DRM: Supplies brands with a focused DRM solution to locate and counter counterfeits, gray markets, domain abuse, piracy, and similar issues.
- MemberSpace: Adds a membership paywall and DRM protection for websites to protect and monetize digital assets in a SaaS turnkey fashion.
When selecting a DRM option be sure to align the capabilities of the tool with the DRM needs. Specifically, the format of the digital files, tracking or monitoring requirements, infrastructure requirements, user installation requirements, and potential alerts to manage.
Legal Considerations of DRM
Digital rights management adds additional technical protections for assets, and the US Digital Millennium Copyright Act (DMCA) passed in 1998 makes it illegal for anyone but the entity that applied the DRM to remove it. However, enforcement of DMCA remains weak and many other countries tacitly or explicitly allow for DRM removal or circumvention:
- China: Doesn’t enforce or protect international copyright holders.
- European Union: Allows DRM circumvention under certain circumstances.
- Israel: Doesn’t prohibit DRM circumvention.
- Pakistan: Currently doesn’t criminalize DRM circumvention or enforce copyrights.
Some aspects of DRM that tightly restrict use conflict with the Fair Use clause of the US copyright law that allows free use under specific circumstances (parody, teaching, research, etc.). Similarly, DRM can conflict with the First Sale Doctrine, which provides the owner of a copyrighted work to sell, rent, lend, or share copies of the work. When adding DRM, be specific in the license terms presented to consumers to avoid potential conflicts with these laws.
Frequently Asked Questions (FAQs)
Bottom Line: DRM Provides Special-Use Encryption
Digital rights management progresses past the normal locked or unlocked nature of encryption to provide more granular control over digital asset use. When adopting DRM, you retain the protections of encryption and add additional options for collaboration, monetization, and secure distribution. Consider how DRM can expand your opportunities and explore the option that fits your specific use case.
To learn about various categories of more traditional encryption, read about the best encryption software and tools.







