How would you feel if your car, the vehicle you drive 60 MPH to work and pick up your kids from school in, was potentially compromised by hackers due to a security vulnerability?
Security researchers at BitSight have discovered six critical vulnerabilities in a popular vehicle GPS tracker produced in China, the MiCODUS MV720. The device is typically used by consumers for theft protection and location tracking, and by some organizations for fleet management, but it could be used by threat actors for something completely different.
The tracker has roughly 1.5 million devices in use worldwide, and if exploited in an attack, it could cut off fuel, stop vehicles from running, and be used as surveillance to track routes and locations. MiCODUS customers include government, military, law enforcement agencies, and Fortune 1,000 companies.
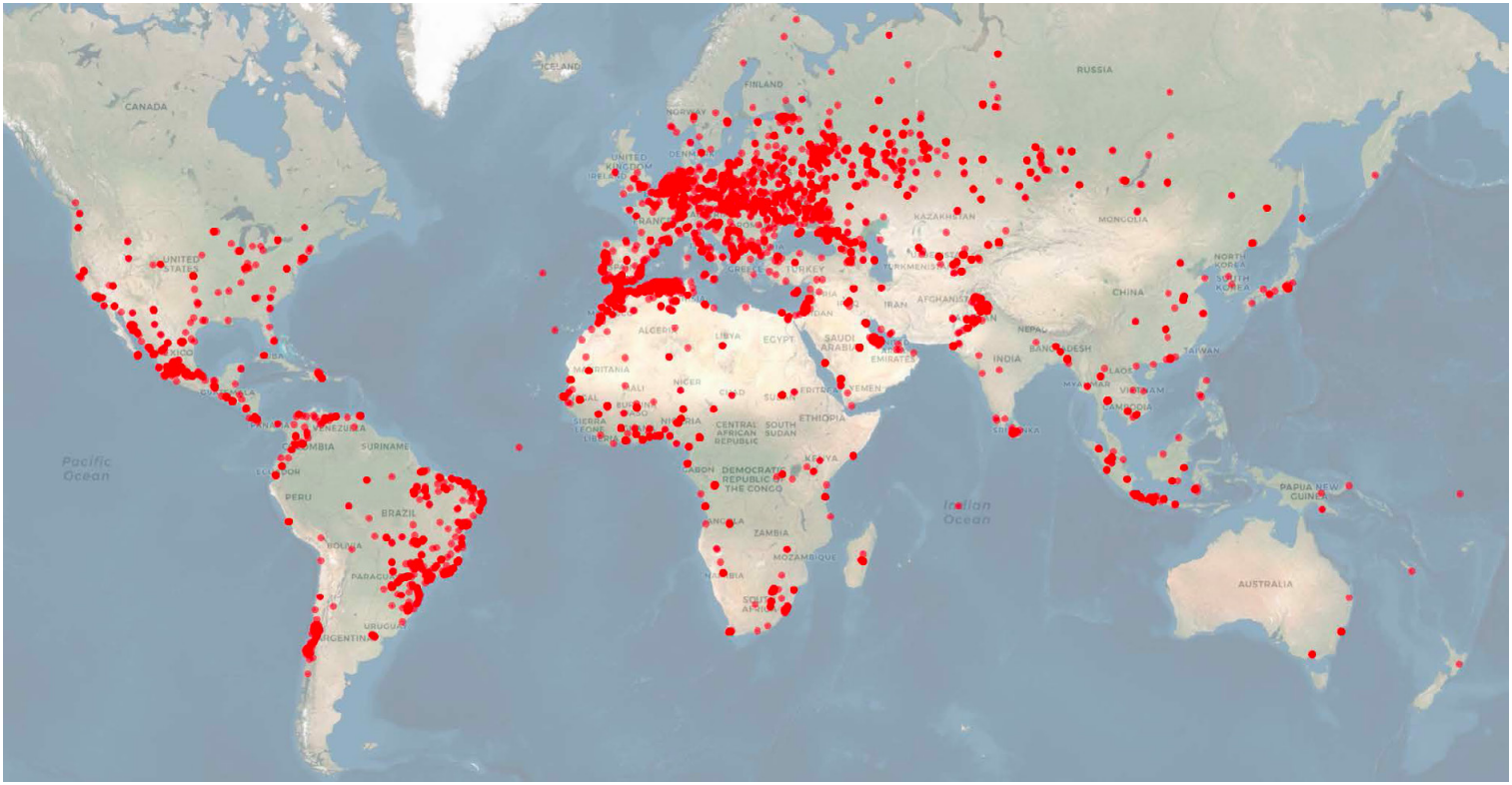
This map provided by BitSight shows its users around the world:
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued an Industrial Controls Systems Advisory (ICSA) after BitSight shared its research, determining these vulnerabilities required disclosure.
MiCODUS GPS vulnerabilites
BitSight and CISA strongly recommend that users immediately stop using the GPS tracker, or at least disable it, until a patch is made available. There is currently no workaround for the vulnerability.
CISA has assigned identification numbers to five of the six vulnerabilities, with two of them having a CVSS (Common Vulnerability Scoring System) score of 9.8:
- CVE-2022-2107 (CVSS score of 9.8) — "The API server has an authentication mechanism that allows devices to use a hard-coded master password. This may allow an attacker to send SMS commands directly to the GPS tracker as if they were coming from the GPS owner’s mobile number."
- CVE-2022-2141 (CVSS score of 9.8) — "SMS-based GPS commands can be executed without authentication."
- CVE-2022-2199 (CVSS score of 7.5) — "The main web server has a reflected cross-site scripting vulnerability that could allow an attacker to gain control by tricking a user into making a request."
- CVE-2022-34150 (CVSS score of 7.1) — "The main web server has an authenticated insecure direct object reference vulnerability on endpoint and parameter device IDs, which accept arbitrary device IDs without further verification."
- CVE-2022-33944 (CVSS score of 6.5) — "The main web server has an authenticated insecure direct object references vulnerability on endpoint and POST parameter 'Device ID,' which accepts arbitrary device IDs."
- The vulnerability without an identification number (CVSS score of 8.1) uses a preconfigured default password of "123456" that allows threat actors to access any GPS tracker at random.
Richard Clarke, a renowned security expert and former presidential advisor on cybersecurity, shared his thoughts on the vulnerabilities of the GPS tracker with BitSight:
"If China can remotely control vehicles in the United States, we have a problem. With the fast growth in adoption of mobile devices and the desire for our society to be more connected, it is easy to overlook the fact that GPS tracking devices such as these can greatly increase cyber risk if they are not built with security in mind.
BitSight's research findings highlight how having secure IoT infrastructure is even more critical when these vulnerabilities can easily be exploited to impact our personal safety and national security, and lead to extreme outcomes such as large-scale fleet management interruption and even loss of life."
It might be time check on your vehicle's GPS tracker and make sure that it is not a MiCODUS product—unless you don't mind getting stopped in the middle of the road for no good reason.
For more information, see the report from BitSight and the advisory from CISA.





