This Identity Management Day, Go BIG or Go HOME!
Thales Cloud Protection & Licensing
APRIL 11, 2023
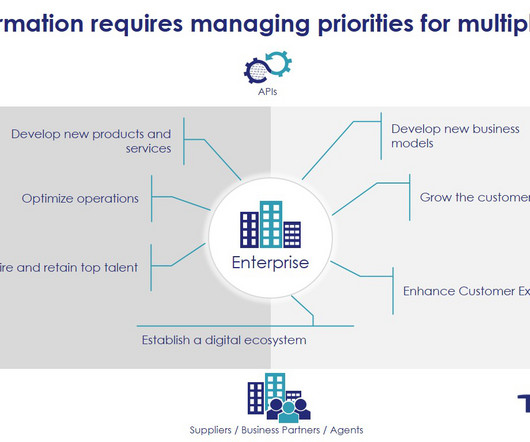
forced organizations of all sizes to drastically accelerate their digital transformation projects. The B2B landscape wasn’t that different either. For most companies, this challenge of B2C, B2B, and gig-worker interactions was far more daunting than enabling a remote style of working for their employees.














Let's personalize your content