Another Malware with Persistence
Schneier on Security
MARCH 9, 2023
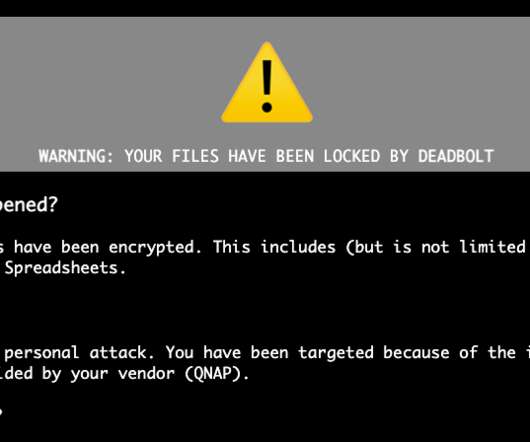
Here’s a piece of Chinese malware that infects SonicWall security appliances and survives firmware updates. The campaign was notable for the ability of the malware to remain on the devices even after its firmware received new firmware. The malware also adds a backdoor root user to the mounted file.













































Let's personalize your content