Big Game Ransomware being delivered to organisations via Pulse Secure VPN
A security vulnerability in a popular enterprise remote access product is being used to deliver ransomware into organisations, with targeted delivery to also delete backups and disable endpoint security controls.
The 2019 backstory
Back in April 2019, Pulse Secure issued an advisory for their Zero Trust VPN product, warning organisations of an out of cycle patch which fixed a vulnerability in their product Pulse Connect Secure:
As you can imagine with updates outside the Windows ecosystem, organisations are terrible at applying patches properly.
That vulnerability is incredibly bad — it allows people without valid usernames and passwords to remotely connect to the corporate network the device is supposed to protect, turn off multi-factor authentication controls, remotely view logs and cached passwords in plain text (including Active Directory account passwords).

On 14th August 2019 somebody posted an exploit for the issue on my forum, OpenSecurity.global. A few days later a public exploit by Justin Wagner and Alyssa Herrera appeared.
On August 22nd 2019, I realised somebody was scanning the internet for the issue, via the help of BinaryEdge.io.
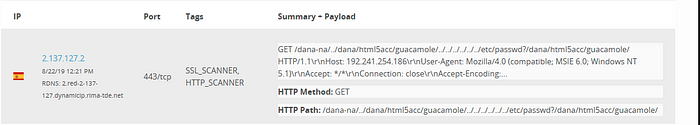
I sent up the flare that organisations needed to urgently patch this (by the 3 months old) issue:
On August 25th 2019, Bad Packets scanned the internet and found almost 15000 endpoints across the world had the issue directly exploitable:

Those results included networks at governments across the world — many incredibly sensitive organisations included — and basically a list of the world’s largest companies. It was clear organisations were simply not patching.
Since then Bad Packets has been working with CERTs, CSIRTs and ISACs and related government groups to share the scan data and encourage organisations to patch.
It then became clear Advanced Persistent Threat groups were using the vulnerability to gain access to networks.
In October 2019, warnings to patch were sent out via US CISA, US National Security Agency, and the UK’s National Cyber Security Centre:



The Now ransomware
I follow big game ransomware and general cyberattacks, as I work in corporate cybersecurity, so want to know what attackers are up to.
I realised in some recent incidents, impacted companies ran Pulse Secure VPN (it’s super easy to spot with Shodan). I also realised through the vulnerability scanning which has been happening across the internet that many of the organisations either hadn’t patched their Pulse Secure system at the time of the incident, or had only patched recently (you can backdoor Pulse Secure systems, and still gain access after patching).
Earlier this week I’ve seen two notable incidents where they believed Pulse Secure was the cause of a breach, and used to deliver Sodinokibi (REvil) ransomware. In both cases the organisations had unpatched Pulse Secure systems, and the footprint was the same — access was gained to the network, domain admin was gained, VNC was used to move around the network (they actually installed VNC via psexec, as java.exe), and then endpoint security tools were disabled and Sodinokibi was pushed to all systems via psexec.
I’ve now seen an incident where they can prove Pulse Secure was used to gain access to the network.
You need to patch
As I write this, there’s still over a thousand unpatched devices in the US alone:
If you want to gain access to the report submit a request to Bad Packets here.
Statement from Pulse Secure

Update 06/01/2020
I understand Travelex has been ransomware’d by this group: https://www.computerweekly.com/news/252476283/Cyber-gangsters-demand-payment-from-Travelex-after-Sodinokibi-attack
They had 7 unpatched Pulse Secure servers:

