

In the last several months the XDR acronym is being used by almost every security product manufacturer. It is one thing to say that you have it, but the hard work that goes into building the detections takes years. It is not enough to say that you have a big data platform that you can dump things into and search; you need actionable detections that lead to meaningful correlations. Here are two key things to consider as you look at XDR.
Data Normalization – To get full visibility, the first thing you need to consider is the data itself. Every security product has a different way of presenting its logs and alerts. Network solutions, endpoint security tools, firewalls, identity tools, cloud security tools and many others all have their own alert formats and frequency. Every SIEM tool can store logs from these devices – that’s the easy part.
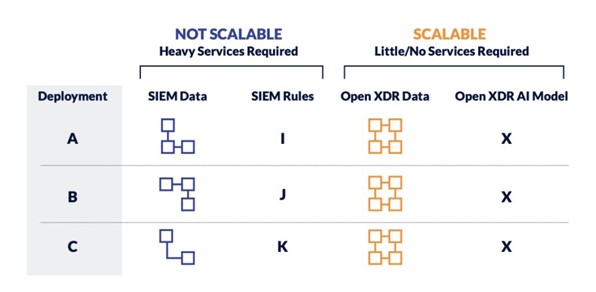
The problem is that creating complex, multi-dimensional rules to keep up with the current pace of attacks is nearly impossible. For example, on an IDS you could see upwards of one million alerts per day. Suricata rules may be able to filter out the known vulnerabilities down to 200,000, but from there you would normally have to create a series of rules based on your knowledge of the customer’s environment.
This is an area where leveraging machine learning (ML) across the IDS data can significantly reduce that number down to a manageable handful of alerts. Instead of writing rules to detect things, you can leverage ML to baseline what is normal behavior on that network. When does the customer normally log in? Where do they log in from? How long do they normally stay logged in? Instead of 200,000 alerts, ML detections can reduce that to a handful. Seeing this information correlated across all of your security tools is significantly faster and easier for your SOC analyst to manage.
Open Integrations – In addition, make sure that the XDR platform you are considering is open. As security technologies change rapidly over the next few years, these platforms will help you avoid vendor lock-in. This will help you maintain your ability to adjust to the changing cybersecurity landscape and your customers’ needs.
At Stellar Cyber – we think X means everything – regardless of where you are coming from and which existing tools you use, and regardless of where you want to go in terms of security maturity. To us this means we help compose a strategy they work for you and your customers, leveraging the investments you both have made.


















