3 Ways to Defend a Cybersecurity Budget with Cyber Risk Quantification
 Deloitte’s “CFO Signals” Q4 2022 survey of chief financial officers found 41% feeling pessimistic about their companies’ financial outlook. Survey participants named “cost management” their number one priority for 2023. On the other hand, 79% said they intend to make new investments in the new year in “digital transformation.”
Deloitte’s “CFO Signals” Q4 2022 survey of chief financial officers found 41% feeling pessimistic about their companies’ financial outlook. Survey participants named “cost management” their number one priority for 2023. On the other hand, 79% said they intend to make new investments in the new year in “digital transformation.”
For CISOs and other cybersecurity leaders, that might as well be a flashing yellow light over a sign that says, “Do More with Less.”
RiskLens is the leader in cyber risk quantification software and services.
The pressure will be on CISOs to prioritize and justify their budgets to CFOs in the financial language that bean counters understand best: return on investment for cybersecurity programs in terms of cyber risk reduced for dollar spent.
The FAIR™ standard for cyber risk quantification, implemented through the RiskLens platform and services, hits that mark, starting with identifying the top cyber risk to the organization for probable impact, and moving through comparative modeling of the effect of controls spending on decreasing risk.
Let’s see how that plays out with four common buckets of cybersecurity spend:
Compliance
Particularly for heavily regulated industries, a good chunk of annual budget will go into responding to compliance or findings. First, ongoing FAIR analysis of top risks satisfies the common regulatory requirement for risk assessments, and – bonus — gives actionable intelligence for cyber defenders on most probable risk scenarios. Second, quantitative analysis can be a shield against busywork generated by audit findings identifying controls gaps that don’t have enough risk reduction value to be cost-effective to remediate.
Learn more: ‘High Risk’ Audit Finding Doesn’t Hold Up to FAIR Analysis
Ongoing Maintenance
With cyber risk quantification, a CISO can build a bulletproof budget by essentially self-auditing the top ongoing contracts for value for risk reduction. Example: A RiskLens client evaluated whether to continue the annual $1 million fee for the technology vendor that maintained the order fulfillment system or move the support in-house. What would the cost of a system outage be inhouse vs. third party? FAIR analysis showed the faster response time for the vendor well justified the contract.
Read the case study: Operational Risk from Outage of a Manufacturer’s Order Fulfillment System
New Projects
The 2023 version of an effective CISO doesn’t propose new spending based on FUD or “it’s technical, just trust me.” The CISO walks in to pitch the CFO or CIO or other decider with business-friendly presentation like the image below, showing the effect of a cloud migration in reducing probable risk in dollar terms compared to the status quo. Bonus points earned for showing how cybersecurity enables a major digital transformation initiative of the company.
Learn more: Video Demo: Cloud Security Risk Analyzed in 15 Minutes
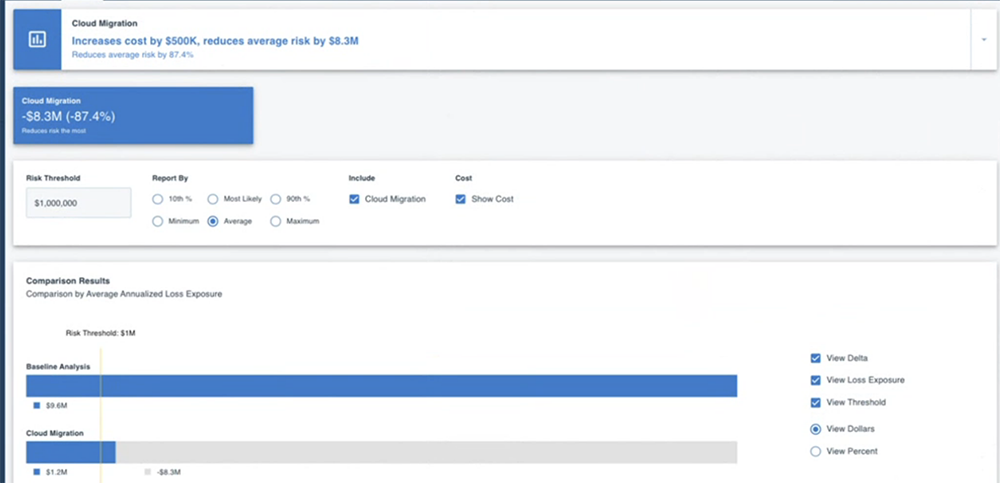
RiskLens platform analysis output
Budget Support – We Offer Alternatives
The Enterprise SaaS subscription to the RiskLens platform supports fast, risk-informed decisions at any level of the enterprise, from planning a new digital initiative down to day-to-day audit findings.
RiskLens Pro is an easy and affordable managed service that helps organizations quickly define, assess, and communicate cyber risks in financial terms, with no in-house expertise or significant time commitment necessary.
As an entry guide to budget allocation with quantitative risk analysis, we offer My Cyber Risk Benchmark, showing how your organization’s quantified risk compares to your industry’s average across a range of cyber risk categories.
![]()
*** This is a Security Bloggers Network syndicated blog from RiskLens Resources authored by Jeff B. Copeland. Read the original post at: https://www.risklens.com/resource-center/3-ways-to-defend-a-cybersecurity-budget-with-cyber-risk-quantification





