Cyber Risk Quantification – The What, The Why and The How!
CRQ (Cyber Risk Quantification) is the latest acronym doing the rounds in the cyber security industry. Many security professionals regularly use this acronym but few actually understand what CRQ is and even fewer know how to implement it.
In this blog, I will attempt to demystify the concept of CRQ, express why a robust CRQ model is an essential requirement for every organization and describe the compelling business value it offers to those who have successfully implemented it. Finally, I will discuss the two primary approaches currently advocated in the market, highlight a few limitations of these approaches and provide details of a more effective way to implement CRQ.
The What?
Simply put, CRQ is the quantification of an organization’s cyber risk expressed in monetary terms. An organization’s cyber risk is the intersection of its internal and external threat environment, its current cyber capabilities (i.e. security controls and other mitigations that exist within the organization), and the business value at risk from a cyber attack. CRQ enables an organization to express this interaction in a language that is understood and accepted by a large number of internal and external stakeholders.
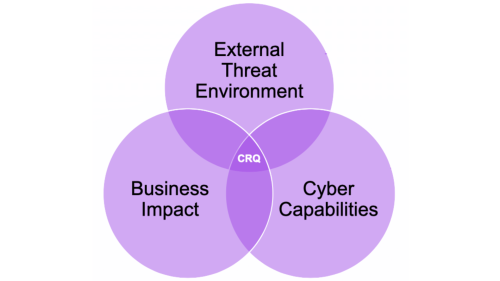
The Why?
CRQ is a key enabler for risk-based business decision making. It allows CISOs and their infosec teams to articulate cyber risk to senior management and the Board in a language that is consistent with the way other risks such as market, credit and operational risks are presented. Its ability to do so is extremely powerful. In my previous role, I witnessed the stunned reaction of a non-executive director when he realized that their cyber exposure was in the hundreds of millions of dollars! What ensued was a flurry of requests to understand the drivers of this risk and the actions that the organization could take to mitigate it. More generally speaking, CRQ empowers the CISO to:
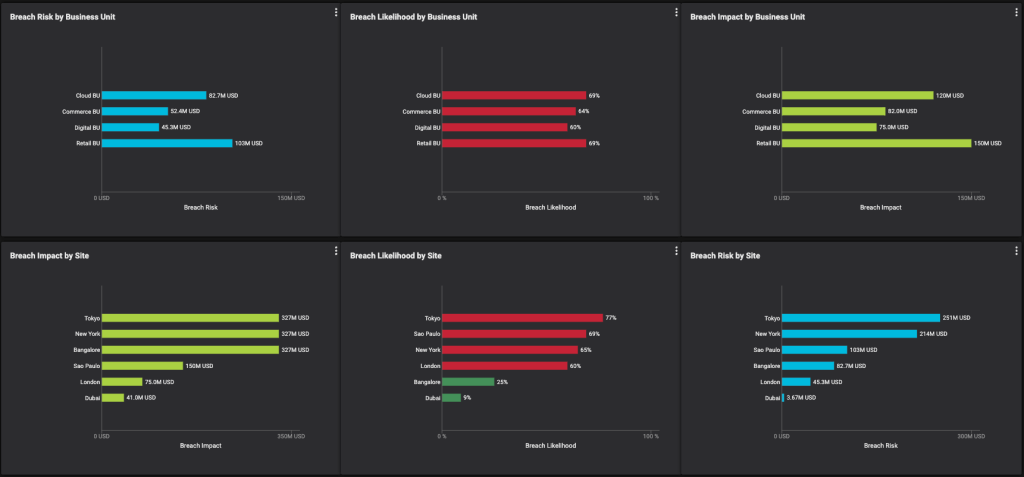
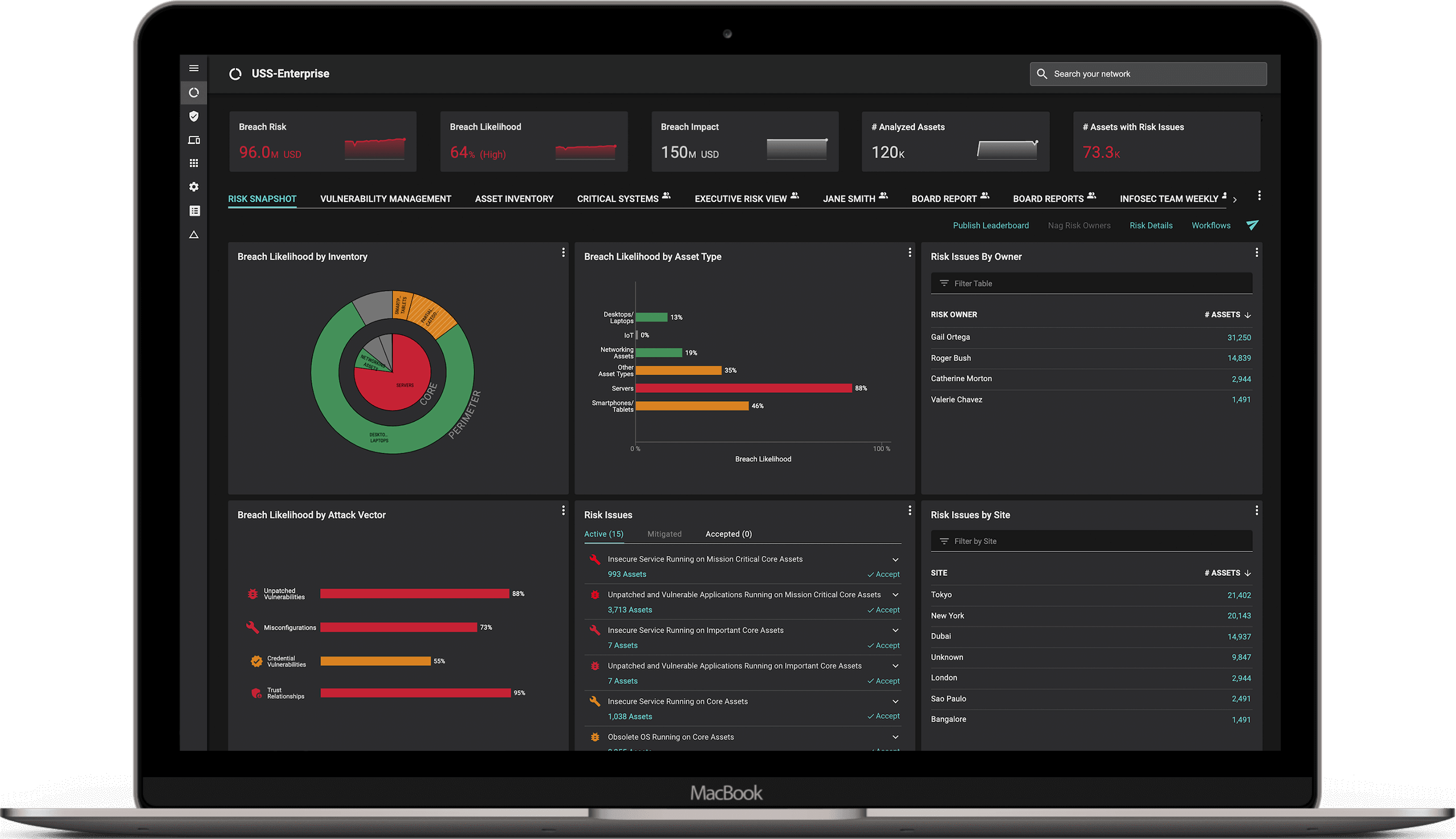
- Effectively report on the cyber risk exposure: When done properly, CRQ allows the CISO to report effectively on enterprise cyber risk. One such example is the illustrative dashboard below:
- Prioritize and justify cyber spend: CRQ allows for budgeting and ROI calculations, which are a good way to build a business case for security funding. For example, you can make a case for deploying two new tools that cost $5M when you provide a defensible calculation that they will reduce risk by $35M i.e., a 700% return on investment.
- Comply and stay ahead of emerging regulatory requirements: CRQ allows organizations to provide an assessment of their cybersecurity risk exposure as well as provide targeted remediation advice to bring the organization’s risk exposure to an acceptable level. In this way, the organization would be able to proactively engage with regulators in an open and transparent way. This is increasingly important as emerging regulations, for example in the US and Australia, will require organizations to enhance their governance, disclosure and risk management related to cybersecurity risk.
- Cyber insurance vs self insurance decisions: CRQ is an effective way for a CISO to articulate the cyber risk exposure of their organization to the Board for informed decision making. This is timely as cyber insurance premiums have increased significantly due to the large number of ransomware attacks and business interruption claims in recent years. Customers are now having to re-evaluate the cyber insurance value proposition and make decisions on whether they self insure or alter the level and type of cyber coverage.
The How?
So how does an organization actually implement CRQ? Two schools of thought have emerged over the last few years. These are the Top Down and Bottom Up approaches to CRQ. By far, the more popular choice is the Top Down approach which utilizes scenarios and high level assumptions to estimate risk in monetary terms. This calculation is usually performed at the enterprise level. Based on my experience working with many clients, this approach has the following limitations:
- Subjective assessments do not consider the vast amount of data that already exists within the organization.
- Assumptions underpinning the risk model are usually made at a high level, lack credibility and often translate into model results which are indefensible and inconsistent with real world experience.
- Risk modeling is simplistic and rudimentary at best and is incapable of capturing the ever evolving nature of cyber risk.
- Risk allocation to business groups and down the organizational structure is difficult.
The other side of the coin is the Bottom Up approach to CRQ. This involves an asset by asset risk assessment. This is an approach that is attempted by customers who are at the more sophisticated end of the cyber risk management spectrum and usually involves creating a DIY data lake to feed the risk model. Needless to say, this is an incredibly challenging problem to solve. A few implementation pitfalls that need to be navigated include:
- What data should we consider and how should this data be used to inform the risk model?
- Where can I find a unified asset list (i.e. the golden source of truth) to build a risk model on?
- How do we capture the sub-additive nature of cyber risk and how do we aggregate up to the enterprise level in a meaningful and statistically correct way?
- There are also significant cost and resource pressures accompanying this approach. In particular, the breadth and depth of skills required, e.g. data science and technical cyber security professionals to implement and operationalize this approach, make this challenging. This often results in a ‘high risk, low reward payoff’ wherein the project is unable to evidence value to the business.
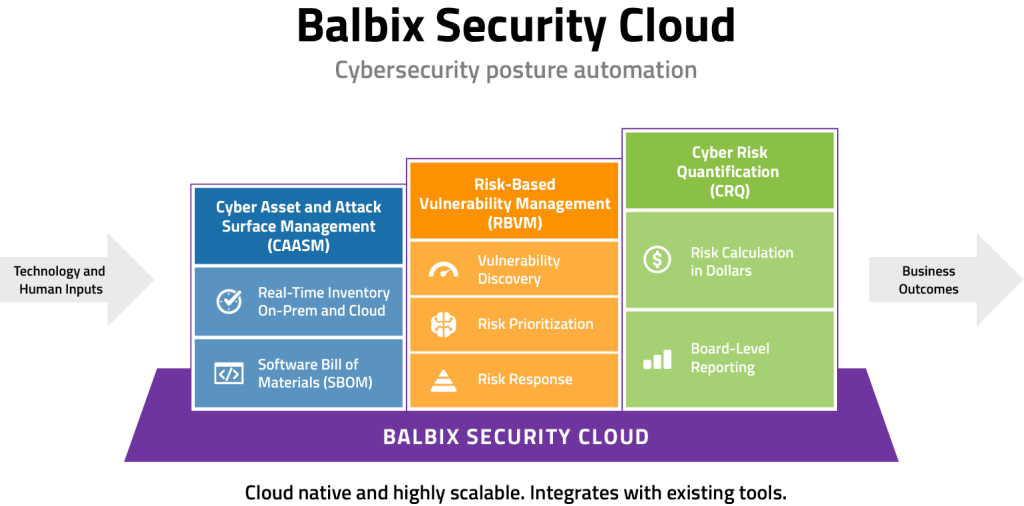
So here we are today and I ask myself if there is a better approach to CRQ that leverages the strengths of both the Top Down and Bottom Up approaches whilst negating their limitations. The answer is an emphatic YES. We at Balbix have developed an AI-powered, market-leading, dynamic CRQ model that estimates your enterprise breach risk in real time and surfaces key risk issues along with prioritized mitigation recommendations. So how do we do it?
Our SaaS platform, the Balbix Security Cloud, is the only solution that:
- Builds your entire asset inventory (hardware, software, on prem and cloud), including a software bill of materials. It does so by ingesting data from your existing security tools, and then correlates, deduplicates and normalizes your data to produce a unified asset inventory.
- Detects, enumerates and assesses breach risk against all known vulnerabilities.
- Maps the deployment of cybersecurity tools and assesses their effectiveness.
- Provides an up-to-date and monetized view of cyber risk for Board consumption.
If you would like to learn more about the Balbix CRQ model and methodology and the benefits it brings to your cybersecurity posture management, please do get in touch.
*** This is a Security Bloggers Network syndicated blog from Blog – Balbix authored by Sidharth Wahi. Read the original post at: https://www.balbix.com/blog/cyber-risk-quantification-the-what-the-why-and-the-how/





