Considerations for Operational Technology Cybersecurity
The Hacker News
APRIL 4, 2024
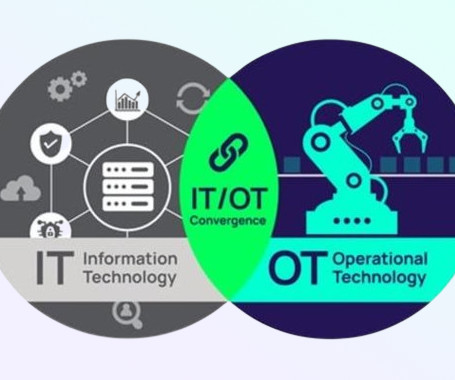
Operational Technology (OT) refers to the hardware and software used to change, monitor, or control the enterprise's physical devices, processes, and events. Unlike traditional Information Technology (IT) systems, OT systems directly impact the physical world.


















































Let's personalize your content