Phantom Floods: Are Service Providers Blind to These DDoS Attacks?
The Data Growth Effect
It’s no secret that we consume more data than ever, according to the IDC report in the next three years their will be more data than what was created in the past 30 years. As a result, traffic bandwidth is growing exponentially and there is no stop to it.
When protecting a largescale network, service providers use a high traffic threshold to detect abnormal behavior. Large DDoS attacks will trigger the defined threshold and the mitigation process will start, but what about those attacks that will not trigger any threshold? What about phantom flood attacks (relatively low volume flood attacks) that sneak below the radar and yet are large enough to overwhelm the target’s defenses?
Service providers carry most of the traffic growth burden, and are turning to virtualized network solutions (Cloud shift, NFV, 5G, SDN, etc.) to balance network scalability and costs. The bandwidth growth does not only result in a new and complex network operation, but it also aggravates the ongoing cybersecurity threat awareness limitations.
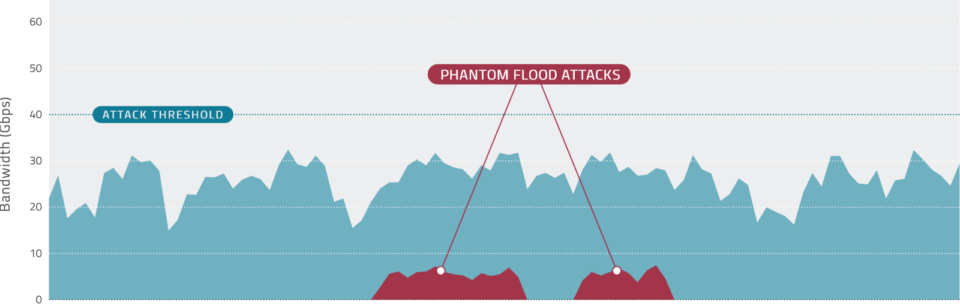
Service Providers Are Blind
The ability to detect the undetected is an ongoing issue for service providers, they are balancing between a wide and narrow protection spectrum. On one hand, they need to protect their network as a single, wide network range, while on the other hand, they need to provide a more granular protection for their customers.
Phantom flood attacks and other low volume attacks are a significant security threat for service providers and their customers. According to Radware’s research, more than 90% of DDoS attacks are less than 1Gbps and even those non volumetric attacks that are larger than 1Gbps will not be blocked easily by traditional solutions due to the lack of granular detection sensitivity.
The threat of Phantom flood attacks can be destructive to many service provider customers and as a result Service Provider’s SOC (Security Operations Center) teams are searching for any solution to enhance their visibility into these attacks and their ability to block them.
Traditional DDoS protection solutions do offer some manual workarounds to enable better detection sensitivity. The most common option is to use manual IP tracking per source/destination with separate security policies. The second option is to leverage a manual network segmentation and divide the network traffic to smaller bandwidth segments.
Both workarounds require high expertise, extensive manual configuration, and a never-ending tuning process. Moreover, even when embracing these manual solutions, service providers cannot achieve the desired visibility and threat awareness of Phantom flood attacks and other traffic anomalies.
[You may also like: Top 6 Questions to Ask When Selecting SSL Protection Solutions]
How to Detect the undetected?
Traditional security solutions are using manual workarounds and can’t deliver the desired protection against phantom flood attacks mainly because the dynamic nature of largescale networks cannot be manually regulated.
Service providers should seek a security vendor which can offer a security solution that automatically adjusts to the dynamic network, thereby eliminating the need for constant monitoring and tuning.
A dynamic solution that can leverage an automated behavioral-based detection and mitigation can deliver full protection against both traditional DDoS attacks and phantom flood attacks so no attack can avoid detection.
Radware’s Quantiles DoS Protection enables service providers with large scale networks to detect and mitigate hidden phantom flood attacks and other traffic anomalies leveraging dynamic quantile DoS algorithm. This sophisticated behavioral protection solution offers a granular detection sensitivity to low volume attacks and the ability to enjoy both wide and narrow protection spectrum, even in large scale networks.
For more details regarding Radware’s Quantiles DoS Protection – link to Solution white paper
*** This is a Security Bloggers Network syndicated blog from Radware Blog authored by Shai Haim. Read the original post at: https://blog.radware.com/serviceprovider/2021/10/phantom-floods-are-service-providers-blind-to-these-ddos-attacks/




