Microsoft in November fended off a massive distributed denial-of-service (DDoS) attack in its Azure cloud that officials said was the largest ever recorded, the latest in a wave of record attacks that washed over the IT industry in the second half of 2021.
The enterprise software and cloud giant said in a blog post this week that during the last six months of the year, there was a 40 percent increase in the number of DDoS attacks worldwide over the first half of 2021, with an average of 1,955 attacks per day and a maximum of 4,296 on Aug. 10. Microsoft itself mitigated 359,713 unique attacks against its infrastructure between July and December, a 43 percent jump from the first half of 2021.
In addition, the DDoS activity also was unprecedented in its complexity and frequency, Anupam Vij, principal PM manager, and Syed Pasha, principal network engineer, both with Azure Networking, wrote in the blog post.
They noted that the “availability of DDoS for-hire services as well as the cheap costs – at only approximately $300 USD per month – make it extremely easy for anyone to conduct targeted DDoS attacks.”
New Record Attack
Azure officials in October reported that they were able to mitigate a 2.4 terabit-per-second DDoS attack against a European cloud customer that originated in the Asia-Pacific region. That attack was 140 percent larger than a 1 Tbps attack in 2020 and larger than any similar event ever detected on the Azure public cloud, they said.
Since then, Azure was able to stave off three larger attacks, including one in November that hit a throughput of 3.47 Tbps and had a packet rate of 240 million packets per second (pps). It targeted an Azure customer in Asia.
“This was a distributed attack originating from approximately 10,000 sources and from multiple countries across the globe, including the United States, China, South Korea, Russia, Thailand, India, Vietnam, Iran, Indonesia, and Taiwan,” Vii and Pasha wrote.
The DDoS assault used multiple attack vectors for User Datagram Protocol (UDP) reflection, including Simple Service Discovery Protocol (SSDP), Connection-less Lightweight Directory Access Protocol (CLDAP), Domain Name System (DNS), and Network Time Protocol (NTP). There was one peak in the attack, which lasted about 15 minutes.
Also read: How to Stop DDoS Attacks: 6 Tips for Fighting DDoS Attacks
Two Other Big DDoS Attacks
There also were two other large attacks in December, including a UDP attack in Asia that reached 3.25 Tbps and lasted more than 15 minutes and included four main peaks, with the highest reaching the 3.25 Tbps mark. A second peak hit 2.54 Tbps. The other attack was a 2.55 Tbps UDP flood that lasted just over five minutes.
The attacks were part of a larger and changing DDoS landscape that not only is seeing rapidly increasing numbers of incidents but also greater sophistication and a shift away from times when such incidents typically occur.
“Interestingly, there was not as much of a concentration of attacks during the end-of-year holiday season compared to previous years,” they wrote. “We saw more attacks in Q3 than in Q4, with the most occurring in August, which may indicate a shift towards attackers acting all year round – no longer is holiday season the proverbial DDoS season! This highlights the importance of DDoS protection all year round, and not just during peak traffic seasons.”
See the Top DDoS Protection Service Providers for 2022
Time and Intensity Increase
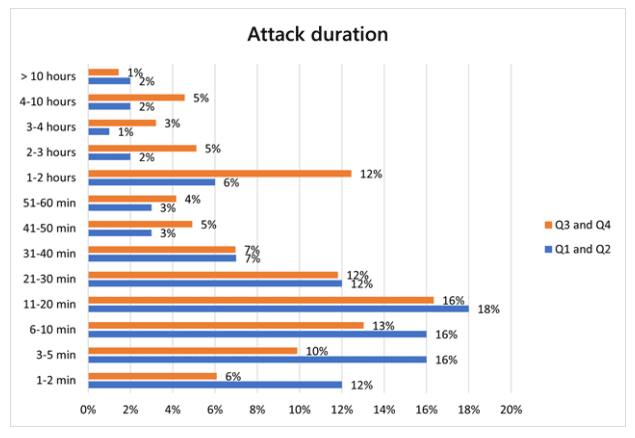
There also was a rise in the second half of the year in the number of attacks that lasted longer than an hour. As in the first six months, most attacks were short-lived. However, the number of attacks in the second half of 2021 that were 30 minutes or less accounted for 57 percent of all incidents, down from 74 percent. Meanwhile, those lasting more than an hour made up 27% of attacks, more than twice the 13 percent in the first half of the year.
“It’s important to note that for longer attacks, each attack is typically experienced by customers as a sequence of multiple short, repeated burst attacks,” Vii and Pasha wrote. “One such example would be the 3.25 Tbps attack mitigated, which was the aggregation of four consecutive short-lived bursts that each ramped up in seconds to terabit volumes.”
Gaming Industry a Top DDoS Target
The gaming industry is most targeted by DDoS attacks, but Microsoft is finding that other industries – including financial institutions, media, internet service providers (ISPs), retailers and supply-chain companies – are seeing an increase in such incidents.
UDP attacks accounted for 55 percent of all DDoS campaigns – a 16 percent increase over the first half of 2021 – and UDP is commonly used in gaming and streaming applications.
“UDP is commonly used in gaming and streaming applications,” they wrote. “The majority of attacks on the gaming industry have been mutations of the Mirai botnet and low-volume UDP protocol attacks. An overwhelming majority were UDP spoof floods, while a small portion were UDP reflection and amplification attacks, mostly SSDP, Memcached, and NTP.”
In addition, while the United States continues to be the top target, sustaining 54 percent of attacks, there was a spike in attacks in India – from 2 percent to 23 percent – and there was a drop in Europe, from 19 percent in the first half to 6 percent in the second.
IoT Devices Multiply Attacks
There are multiple reasons for the uptick and growing sophistication of DDoS attacks. As Vii and Pasha noted, the rise of inexpensive DDoS services – giving even the least experienced of threat actors a cheap way to launch such attacks – are a factor. In addition, the proliferation of Internet of Things (IoT) devices is giving hackers a large number of targets to be hijacked and absorbed into a botnet that can then be used in increasingly larger DDoS attacks.
“DDoS attacks are increasing in both volume and force due to the enormous number of vulnerable IoT devices that cyber criminals leverage to create botnets,” Bud Broomhead, CEO of cybersecurity firm Viakoo, told eSecurity Planet. “IoT vulnerabilities must be quickly remediated in order to eradicate the risk of them being used in cyberattacks.”
Cybersecurity firm CrowdStrike this month released a report noting a 35 percent year-over-year increase in 2021 of malware targeting Linux-based IoT devices, with the primary goal of compromising the devices and pulling them into a botnet for use in DDoS attacks. Other companies, such as Kaspersky and NetScout, also have reported rises in DDoS attacks over the past year.
See the Top IoT Security Solutions
Skilled Adversaries Raise Stakes
“DDoS attacks remain a persistent, malicious technique regularly used by countless threat actors,” Stefano De Blasi, cyber threat intelligence analyst at Digital Shadows, told eSecurity Planet. “Although DDoS attacks are frequently associated with technically unsophisticated attackers, these events remind us that highly skilled adversaries can mount high-intensity operations that may result in severe consequences for their targets.”
De Blasi said there are a range of motivations behind such attacks, which typically aim to temporarily disrupt a target’s infrastructure or act as a decoy for more dangerous activity.
“However, attacks like the ones reported by Microsoft are a powerful reminder that some DDoS attacks can have a significant impact standing on their own,” he said. “In fact, organizations affected by high-intensity DDoS attacks may experience a long-time interruption of business, which may cause financial loss, brand or reputational damage and influence customer trust.”
Yehuda Rosen, senior software engineer at cybersecurity company nVisium, told eSecurity Planet that while DDoS “is a nuisance for most companies,” it can be more dangerous when it involves mission critical services, including traffic lights, medical charts and water pumps.
“Ransomware attacks can be avoided by simply following best practices around information security, backups, and updates, but DDoS can occur despite doing everything correctly,” Rosen said. “Even the best DDoS-protection companies aren’t immune to attacks such as these.”
Read next: Cybersecurity Outlook 2022: Third-Party, Ransomware and AI Attacks Will Get Worse





